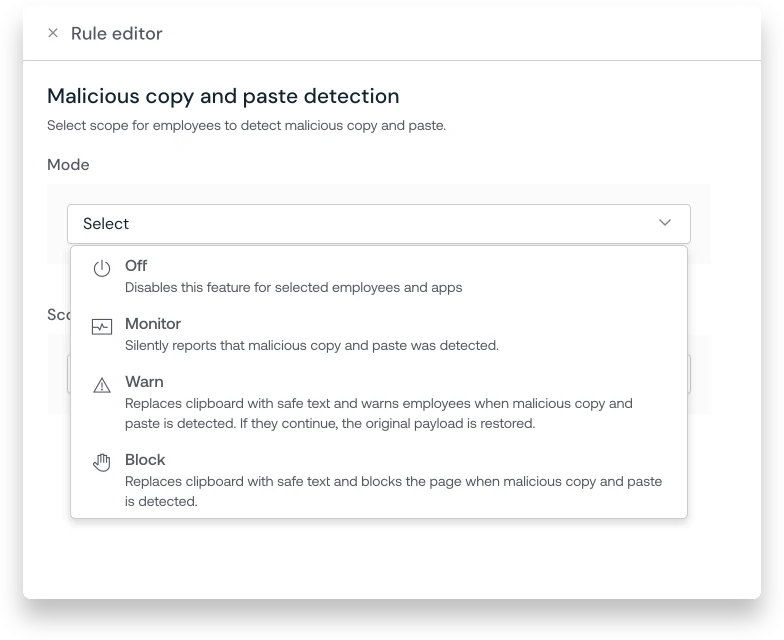
Push Security detects and blocks malicious copy-and-paste activity
Push Security announced the release of a new feature designed to tackle one of the fastest-growing cyber threats: ClickFix-style attacks. The company’s latest innovation, malicious copy-and-paste detection, blocks users from copying malicious scripts in their web browser, preventing them from being run on machines, and cutting off attackers at the earliest opportunity.
Push Security’s malicious copy-and-paste detection identifies and blocks the exact user action that makes ClickFix possible. By monitoring copy events in the browser, Push can distinguish legitimate activity, such as code copied from GitHub or SIEM tools, from malicious scripts. This approach ensures high-fidelity alerts and minimal false positives without disrupting employee workflows or productivity.
“ClickFix is now one of the most effective ways attackers have at their disposal to steal business data and disrupt operations,” said Jacques Louw, CPO at Push Security. “Existing email and network security tools struggle to detect it during delivery, and endpoint controls are being routinely bypassed during execution. Our new feature changes the game by stopping these attacks right where they start: in the browser.”
ClickFix, also known as fake CAPTCHA attacks with variants like FileFix, has rapidly become a go-to technique for cybercriminals. Reports show a 400% year-over-year increase in ClickFix attacks, with a separate study citing a 517% surge in just the last six months. The attack method is frequently leveraged by groups such as Interlock ransomware and has been linked to several high-profile enterprise breaches in a variety of industries including financial services, healthcare, and retail as well as state and local government.
Unlike traditional phishing, ClickFix attacks manipulate victims into copying malicious code from a fake web challenge, such as a CAPTCHA or “page error,” and running it locally. From there, attackers deliver malware, steal credentials and session cookies, and often deploy ransomware for double extortion.
“We see attack techniques like ClickFix evolve faster than traditional defenses can keep up. So for us, it is key to study attacker behavior in depth and design protections around the actions they can’t avoid,” said Louw. “This research-driven approach allows us to deliver practical, universally effective controls that other vendors often overlook, and it’s what we believe sets us apart as a true innovator in browser security.”
Key benefits of Push’s malicious copy-and-paste detection include:
- Universal protection: Effective across all ClickFix variants, regardless of lure type, delivery channel, or malware payload.
- Seamless user experience: Unlike heavy-handed endpoint or DLP controls, Push protects without blocking legitimate copy-paste activity.
- Early intervention: Stops attackers before malware delivery, rather than relying on endpoint detection after the fact.
This new feature adds another layer to Push Security’s browser-based defense platform, which already protects organizations against phishing, session hijacking, credential stuffing, malicious browser extensions, malicious OAuth integrations, and other browser-based attacks.
In addition, the research team’s continued deep dive into ClickFix also led to the discovery last week of a new ClickFix-style technique it has since dubbed “ConsentFix.” This new browser-based attack takes over user accounts with a simple copy and paste. If a user is already logged into the app in their browser, they don’t even need to supply credentials, or pass an MFA check, meaning it circumvents phishing-resistant auth like passkeys too.