Social engineering

Scattered Lapsus$ Hunters seeks women for vishing attacks
The Scattered Lapsus$ Hunters (SLH) hacking collective has launched a recruitment push aimed specifically at women, offering cash payments for participating in voice-phishing …

Windows Notepad Markdown feature opens door to RCE (CVE-2026-20841)
Among the many security fixes released by Microsoft on February 2026 Patch Tuesday is one for CVE-2026-20841, a command injection vulnerability in Notepad that could be …

AI-driven scams are eroding trust in calls, messages, and meetings
In this Help Net Security video, Miguel Fornés, Governance and Compliance Manager at Surfshark, discusses how AI is changing social engineering attacks. He describes how tasks …

ShinyHunters flip the script on MFA in new data theft attacks
Multi-factor authentication (MFA) is supposed to defend against phishing attacks, but threat actors operating under the ShinyHunters banner are using it as a pretext in …

Fake browser crash alerts turn Chrome extension into enterprise backdoor
Browser extensions are a high-risk attack vector for enterprises, allowing threat actors to bypass traditional security controls and gain a foothold on corporate endpoints. …

When the Olympics connect everything, attackers pay attention
Global sporting events bring a surge of network traffic, new systems, and short term partnerships. That mix draws attention from cyber threat actors who see opportunity in …

Browser-in-the-Browser phishing is on the rise: Here’s how to spot it
Browser-in-the-Browser (BitB) phishing attacks are on the rise, with attackers reviving and refining the technique to bypass user skepticism and traditional security controls. …

Rakuten Viber CISO/CTO on balancing encryption, abuse prevention, and platform resilience
In this Help Net Security interview, Liad Shnell, CISO and CTO at Rakuten Viber, discusses how messaging platforms have become critical infrastructure during crises and …
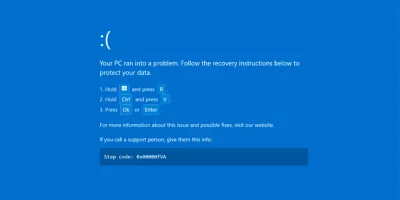
Fake Booking.com emails and BSODs used to infect hospitality staff
Suspected Russian attackers are targeting the hospitality sector with fake Booking.com emails and a fake “Blue Screen of Death” to deliver the DCRat malware. The …

Crypto theft in 2025: North Korean hackers continue to dominate
When they strike cryptocurrency-related targets, North Korean hacking groups are increasingly aiming for large services where a single breach can move serious money, a new …

The collapse of trust at the identity layer
Identity verification has become the latest front in the fight against industrialized fraud, according to a new report from Regula. The shift is visible across sectors that …
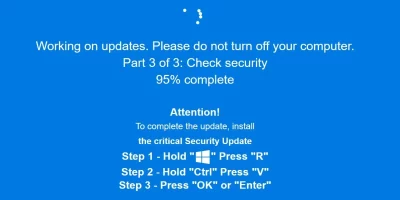
Fake “Windows Update” screen fuels new wave of ClickFix attacks
A convincing (but fake) “Windows Update” screen can be the perfect lure for tricking users into infecting their computers with malware. Add a multi-stage delivery …