Click fraud surge linked to “Bahama” botnet
Click Forensics announced it has identified an unusually large spike in click fraud traffic coming from a new botnet that appears to be eluding the filters of even the most sophisticated search engines, publishers and ad networks. Codenamed the “Bahama botnet”, the malware distributed botnet is using coordinated methods to mask itself as a legitimate high-quality source of search advertising traffic. Click Forensics has tracked instances when the botnet’s attacks have affected up to 30 percent of an advertiser’s monthly search budget for a specific campaign.
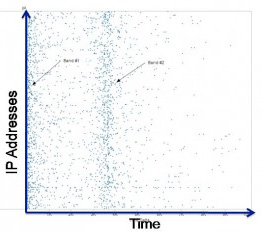
What looked like random clicks was recognized as suspicious activity through advanced pattern detection:
The company recently found links to the malware behind the Bahama botnet in Google search results for “Facebook Fan Check virus.” The malware program is extremely similar to the “scareware” or malvertising program found last weekend in advertisements on NYTimes.com.
The Bahama botnet commits click fraud in a number of different ways. It can generate paid clicks by using normal user behavior to transform an organic search into a paid click. It can also leverage the network of bot-infected machines to programmatically auto-generate paid clicks without any human interaction. The dual nature of this botnet makes it a more powerful vehicle for committing click fraud than other kinds of click fraud botnets.
Click Forensics began tracking the botnet after noticing a sudden and sustained rise in strange traffic patterns in live click stream data from multiple sources, including ad networks and search engines as well as publisher and advertiser web sites. They codenamed the botnet “Bahama” because when it was first detected it redirected traffic through 200,000 parked domains located in the Bahamas. The botnet has since been reprogrammed to redirect traffic through other intermediate sites hosted in Amsterdam, Netherlands; the United Kingdom; and San Jose, California.
In its onsite click fraud testing laboratory, Click Forensics has found only one antivirus program out of 20 popular ones capable of identifying and removing the malicious malware program responsible for bringing PCs under the control of the botnet. It is also cooperating closely with top ad networks, search engines, advertisers and online publishers to ensure that traffic from the botnet is properly identified.
For additional background on the botnet go here.