93% of DDoS attacks last 30 minutes
As the tide of DDoS attacks continues to expand, the rise of the Internet of Things (IoT) and the influx of network connected devices, such as webcams and routers, are leading to the growth of Simple Service Discovery Protocol (SSDP)-based amplification attacks, according to NSFOCUS.
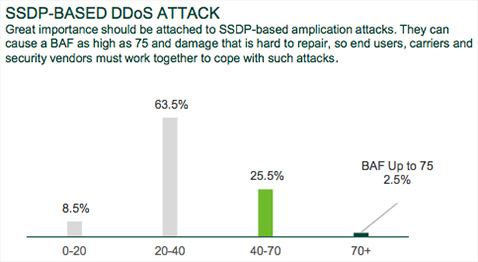
Results of statistical analysis and key observations are based on data from actual incidents of DDoS attacks that occurred during the second half of 2014. This data was collected from a mix of global enterprises, Internet service providers, regional telecom operators and Internet hosting companies.
The rise of IoT-connected devices responsible for an increase in SSDP reflection attacks: With the proliferation of the Internet of Things, any network-connected device with a public IP address and vulnerable operating system will increase the number of devices that could be used to launch SSDP-based reflection type attacks. This particular type of DDoS attack was seen as the second most dominant threat, after NTP-based attacks, in 2H 2014. More than 30 percent of compromised SSDP attack devices were network-connected devices such as home routers and webcams. Findings also revealed that globally, more than 7 million SSDP devices could potentially be exploited.
Attackers are becoming smarter: While 90 percent of DDoS attacks lasted less than 30 minutes, one attack lasted 70 hours. This shorter attack strategy is being employed to improve efficiency as well as distract the attention of IT personnel away from the actual intent of an attack: deploy malware and steal data. These techniques indicate that today’s attacker continues to become smarter and more sophisticated.
Online retailers, media and gaming remain top targets: As retailers, entertainment and gaming companies increasingly employ online environments, consumers demand the highest level of quality of service. By slowing down or flooding these servers, attackers look to take advantage of online businesses through a variety of means, including blackmail, unfair business competition or asset theft.
Yonggang Han, COO of global business, NSFOCUS, said: “We are watching the evolution of attack technologies that amount to nothing less than ‘bullying’ (flood attacks) and ‘leveraging’ (resource exhaustion) tactics that enhance the impact by exploiting network bandwidth. To counteract these assaults, organizations must look to traffic-cleaning devices in conjunction with other security protocols.”