Review: IS Decisions UserLock
According to a Rapid7 survey, 90% of organizations are worried about compromised credentials and around 60% say they cannot catch these types of attacks. French IT security company IS Decisions tries to tackle this major problem with UserLock, a solution that provides access security and concurrent login control for corporate networks.
Setup and deployment
UserLock works alongside Active Directory, so no modifications are needed to AD or its schema. The software should be installed on a Microsoft server ranging from Windows Server 2003 to Windows 2012 R2. The console is installed by default on the same computer, but you can deploy it to any other server or workstation. The installation procedure is quick, and a Microsoft Access database used for logging is bundled within. Or, you can use your own database solution.
To function properly, UserLock requires Remote registry and Microsoft File and Printer Sharing to be enabled on all machines that UserLock will protect. In case one of these is not enabled, the software will point you in the right direction to mend the situation.

The user interface is rather straightforward, especially for a seasoned Windows server administrator. The first thing you (the admin) need to do after setting up UserLock is to deploy its agents across the network. This can be done automatically, or you can select the specific resources that you want to protect and install agents solely on them. If you need them, 32-bit and 64-bit MSI packages of the desktop agent are also provided.

Protected accounts
Connection rules and restrictions are defined by user, group or organizational unit through an internal UserLock entity named Protected account. This account is based on the accompanying data from the Active Directory. Any entity from the domain can be used as a basis for a protected account, for instance AD user pw and group Sales will become protected accounts pw and Sales inside UserLock.
Upon creating a list of resources you are planning to monitor, it is time to get down to business.

When it comes to monitoring user behaviour, there are almost countless variables that can be taken into consideration, and this is where UserLock excels. For each protected account you can customize:
- Initial access points: number of unique locations where a user can enter the network
- Concurrent sessions: number of concurrent sessions per user with detailed specifics (workstation, terminal, Wi-Fi, VPN, IIS)
- Session limits: detailed customization per session type
- Workstation restrictions: you name it, it can be done – allow/deny, names, IP ranges, OUs, etc.
- Hour restrictions: rules enforced for specific timeframes, such as allow/block connections during or after working hours
- Session timings: limiting session duration, locked time, etc.
All of the predefined messages shown as a result of enforcing the rules can be customized. You can use your own text and reuse the internal variables (ex. %SessionType%) to provide dynamic details describing the situation. As per specific protected account policy, the actions and the alerts can be either informational (user gets just a descriptive pop up) or proactive (session or account gets blocked).

Actions
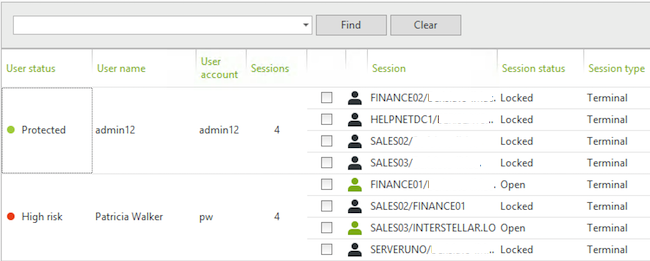
Based upon the rule set for every protected account, the administrator is able to enforce a set of actions that can mitigate a potential problem by locking access to specific user and/or resources. Within the UserLock server interface, it is easy to track current open sessions and analyze red flags. Some of these accounts will get automatically blocked (as per your policies), but you can always block a high risk user manually. This will disconnect all his active sessions and block the credentials until the issue is taken care of.
Reporting
The attention to detail that IS Decisions has shown when planning the protected account rules can also be seen in the built-in reporting mechanism. The software collects a wide range of usage patterns per each protected account and you can generate a report based on every one of these parameters.

Besides the fields pictured above, there are also options to audit the logs per specific entities other then users (groups, OUs), as well as further timeframe parameters. The reports are launched in the application and can be exported in PDF, TXT, XLS, CSV, HTMNL, MHT and RTF format.

Scheduling
All of the reports UserLock generates can be scheduled. The scheduler itself contains every possible time aspect you’ll need to optimize the creation and delivery of the selected reports. The scheduled reports are generated in a PDF format. There are no options to select other file types, but if you delete .pdf from the file name and add one of the other supported file types, it will work. This screen definitely needs to be upgraded in the next version.
The scheduler can also be used for automating the clean-up of existing older records.
Documentation
The UserLock documentation is quite extensive. While the software itself is easy to configure and manage, there is a large number of online resources that can help users discover the benefits of using the product. There is a step by step getting started guide, which you can follow to understand every aspect of what UserLock can do. The use cases section of the support page specifies 10 detailed usage scenarios which demonstrate UserLock’s powerful access protection capabilities.
For the purpose of this article, I have tested UserLock 9, which was released a couple of months ago. As a brief blast from the past, check out the visual overview of UserLock we published back in 2007.
Pricing
UserLock’s licensing scheme is based on per maximum simultaneous sessions in your network. The unit price for 50 to 99 user sessions is $16.80. There are a couple of predefined price tiers and in the biggest one the unit price for 1000 to 1999 user sessions would be $9.38. For larger deployments, you should contact IS Decisions to get a custom price quote. The important thing to add is that these are perpetual licenses. Pricing includes new releases and technical support for the first year.
Final thoughts
Stolen user credentials were at the root of some of the biggest hacks in the last few years. UserLock is a powerful product that focuses on preventing the internal and external threats related to compromised credentials, by providing the administrators with detailed options for monitoring and restricting access to their Windows-based networks.