Insecure car-controlling Android apps are a boon for car thieves
Being an expensive thing, a car requires an approach to security that is no less meticulous than that of a bank account. Yet, car manufacturers are infinitely more interested in providing car-controlling apps with features that will make the connected car owners’ life easier than providing them with good security, Kaspersky Lab researchers have discovered.
They have tested seven proprietary Android apps by different car manufacturers or third-party developers employed by them, and looked for things like reverse engineering and GUI overlay protection, availability of an integrity check in the app, whether they encrypt username and password, and so on.
Given how easy it is for malware to compromise Android devices, the results are fairly depressing:
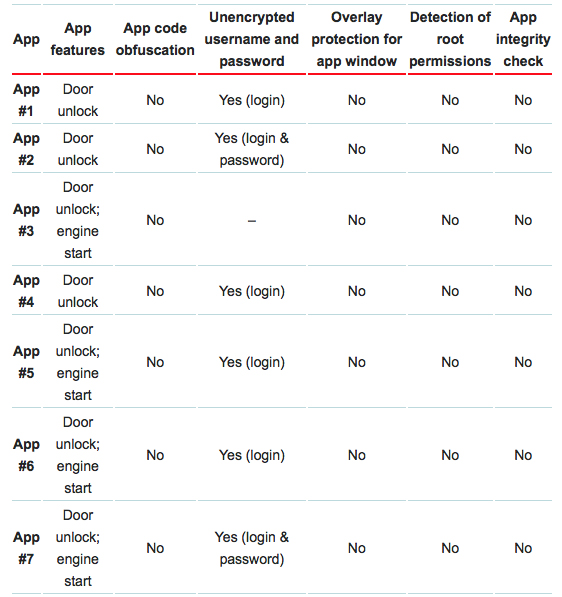
Stealing credentials can be as easy as tricking users into installing a malicious app that will search for the unencrypted credentials or overlay a phishing screen over a legitimate app’s screen – criminals that are after online banking credentials have been doing the latter for years.
“Theoretically, after stealing credentials, an evildoer will be able to gain control of the car, but this does not mean that the criminal is capable of simply driving off with it. The thing is, a key is needed for a car in order for it to start moving. Therefore, after accessing the inside of a car, car thieves use a programming unit to write a new key into the car’s on-board system,” the researchers noted.
“Now, let us recall that almost all of the described apps allow for the doors to be unlocked, that is, deactivation of the car’s alarm system. Thus, an evildoer can covertly and quickly perform all of the actions in order to steal a car without breaking or drilling anything.”
This research was not made to worry users, as much as it’s meant to spur car manufacturers to start implementing good security practices. In fact, the researchers noted that they have not witnessed a single attack on an app that controls cars or ever encountered malicious code aimed at downloading the configuration files of car-controlling apps.
But, they also told Wired that cybercriminals have begun buying and selling connected car app credentials (usernames and passwords, PIN numbers and Vehicle Identification Numbers) for different makes and models of car. So, the days of attacks leveraging this stolen information might not be far-off.
The researchers have informed car manufacturers of their findings, and advised them to perform the necessary changes to protect their consumers before such attacks become widespread.