The anatomy of a completely fileless attack
The use of fileless malware is definitely on the rise, and it’s used both by targeted threat actors and cybercriminals.
Trend Micro researchers, though, are keen to explain that there are malware that are fileless only while entering a user’s system (and they eventually reveal themselves when they execute their payload), and there are completely fileless malware attacks, where the entire infection chain is fileless.
One example of the latter starts with a downloader Trojan they dubbed JS_POWMET.
The attack
They don’t know how it arrives on target Windows computers, although they suspect it’s either downloaded by the users themselves from malicious sites, or dropped by other malware (via an autostart registry created by it).
In fact, the latter stage/approach is almost certain, as the researchers have identified a specific registry that has already been changed by the time the malware is downloaded into the system.
The infection chain that starts with its arrival looks like this:
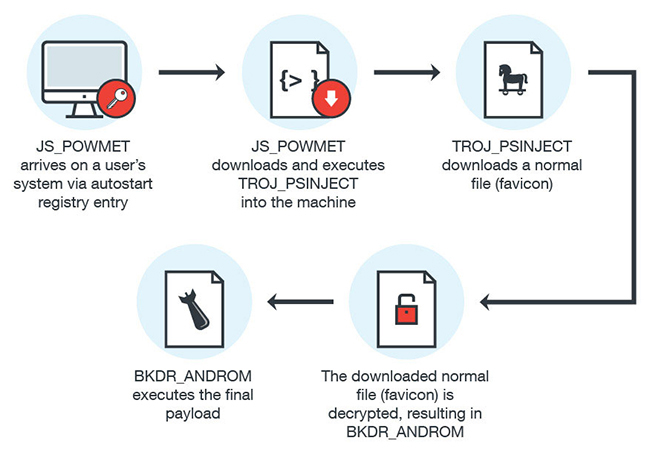
As noted before, the autostart registry fetches an XML with the malicious JavaScript from a specified URL, and executes the script without saving the XML file on the machine/system (this will happen each time the affected machine starts up).
Once JS_POWMET is executed, it downloads another file: TROJ_PSINJECT, a Powershell script that runs under the process of Powershell.
TROJ_PSINJECT connects to a .ru domain and downloads a normal file called favicon, decrypts it (resulting in a malicious DLL file known as BKDR_ANDROM), and injects it into the powershell.exe process without saving it into the machine.
BKDR_ANDROM gathers data such as OS version, IP address, root volume serial number, and administrator privilege from the compromised system and sends it to a remote server, making it likely that this infection is part of a reconnaissance operation. Still, this final payload can be easily changed to fit the attackers’ needs.
What it means for the future
“While JS_POWMET and the rest of the files it downloads are relatively light in terms of impact, this malware demonstrates the lengths cybercriminals will go to avoid detection and analysis. It also shows that even relatively uncommon infection methods involving fileless malware continually evolve,” the researchers noted, adding that organizations and users should always be on the lookout for “stealthy” malware that manages to slip into the system virtually unnoticed.
“One of the more effective methods for mitigating the effects of fileless malware would be to limit access to critical infrastructure via container-based systems that separate endpoints from the most important parts of the network,” they advised.
“For this specific malware, IT professionals can also look into disabling Powershell itself to help mitigate the effects of JS_POWMET and its various payloads.”