Researchers uncover mobile, PC surveillance platform tied to different nation-state actors
The Electronic Frontier Foundation (EFF) and mobile security company Lookout have uncovered a new malware espionage campaign that has targeted activists, journalists, lawyers, military personnel, and enterprises in more than 20 countries in North America, Europe, the Middle East, and Asia.
They have dubbed the threat Dark Caracal, and have traced its activities to as far back as 2012.
The malware used by Dark Caracal
The attackers went after information stored on targets’ Android devices and Windows PCs: SMS messages, call records, contacts, account information, WhatsApp, Telegram and Skype databases, files, legal and corporate documentation, photos, audio recordings, iPhone backups, and so on.
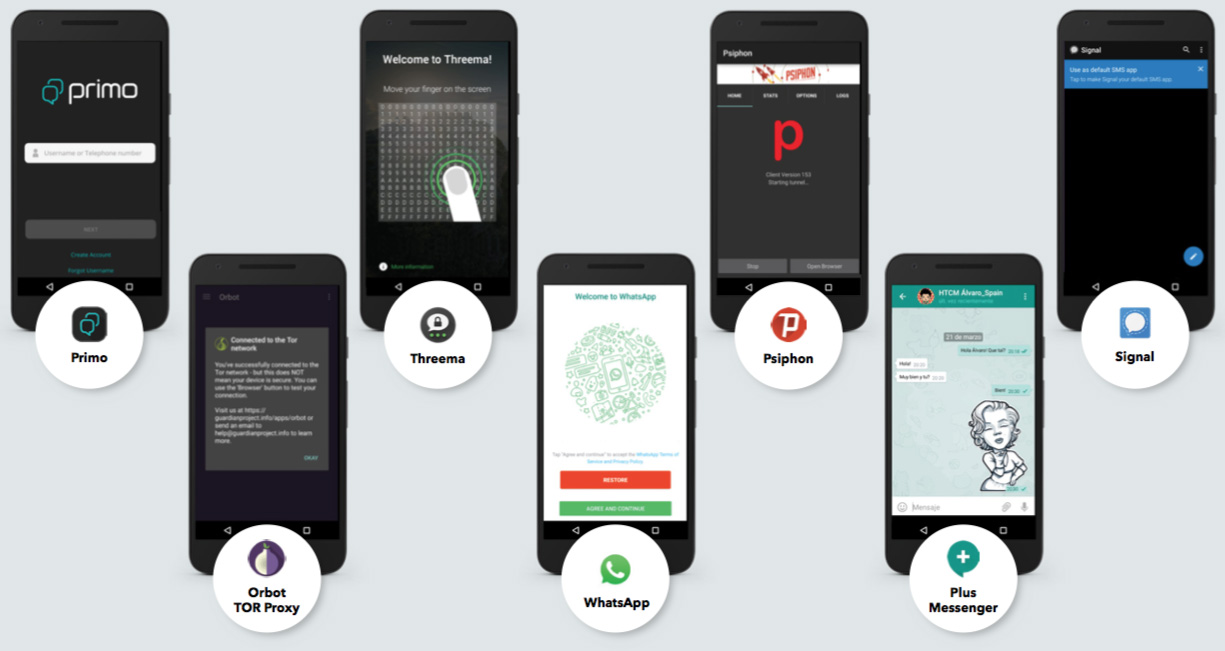
The malware used to exfiltrate data from Android devices has been dubbed “Pallas” by the researchers, and comes in the form of trojanized messaging apps (Signal, WhatsApp, Threema, Primo, Plus Messanger), security/privacy apps (Psiphon VPN, Orbot: TOR Proxy), or other apps (Adobe Flash, Google Play Push).
The apps retained the legitimate functionality so that they would not raise suspicion, but were also capable of spying on users (activate microphone, take photos) and extracting information.
The malware used to compromise Windows machines and spy on users’ activity includes the Bandook RAT (signed with a valid SSL certificate), and CrossRAT (a new remote access trojan developed by Dark Caracal, capable of also compromising Linux and OS X machines).
“Neither the desktop nor the mobile malware tooling use zero day vulnerabilities,” Lookout researchers noted.
“Pallas samples primarily rely on the permissions granted at installation in order to access sensitive user data. However, there is functionality that allows an attacker to instruct an infected device to download and install additional applications or updates. Theoretically, this means it’s possible for the operators behind Pallas to push specific exploit modules to compromised devices in order to gain complete access.”
The desktop malware comes in a range of file types and, again, no zero days or publicly known exploits were located in them. Most often then not, the malware was delivered to the victims with the help of some clever social engineering via spear-phishing.
Who’s behind it?
The researchers believe that the Dark Caracal threat is being administered out of the headquarters of the General Directorate of General Security (GDGS) in Beirut, Lebanon.
How did they come to that conclusion?
Among the many infected devices, they identified some test devices. Within the cluster of test devices, they noticed what could be unique Wi-Fi networks, and discovered that they are mapped to Beirut (some near the GDGS building).
Also, the logins into the administrative console of the C2 server come from three IP addresses, two of which have been geo-located just south of the GDGS’s building.
The infrastructure they uncovered serves a broad set of purposes: it includes command & control servers, servers for storing exfiltrated data, phishing content and malware, an Android App Store hosting malware, and so on.
“The joint Lookout-EFF investigation began after EFF released its Operation Manul report, highlighting a multi-platform espionage campaign targeted at journalists, activists, lawyers, and dissidents who were critical of President Nursultan Nazarbayev’s regime in Kazakhstan,” Lookout researchers shared.
“After investigating related infrastructure and connections to Operation Manul, the team concluded that the same infrastructure is likely shared by multiple actors and is being used in a new set of campaigns. The diversity of seemingly unrelated campaigns that have been carried out from this infrastructure suggests it is being used simultaneously by multiple groups.”
This makes them believe that someone is renting out the Dark Caracal spyware platform to different nation-state actors.
Mike Murray, Vice President of Security Intelligence at Lookout, noted that Dark Caracal is part of a trend they’ve seen mounting over the past year whereby traditional APT actors are moving toward using mobile as a primary target platform. That should not comes as a surprise: mobile devices are chock full of data about a person’s everyday activities.
“One of the interesting things about this ongoing attack is that it doesn’t require a sophisticated or expensive exploit. Instead, all Dark Caracal needed was application permissions that users themselves granted when they downloaded the apps, not realizing that they contained malware,” EFF Staff Technologist Cooper Quintin pointed out. “This research shows it’s not difficult to create a strategy allowing people and governments to spy on targets around the world.”