Dridex gang follows trends, also created FriedEx ransomware
The gang behind the infamous banking Trojan Dridex has also created the FriedEx (aka BitPaymer) ransomware, ESET researchers confidently claim.

The similarities between Dridex and FriedEx
By analyzing and comparing the code of both threats, the researchers discovered a handful of similarities:
- Both malware use the same function for generating UserID (i.e., that generates a unique string from several attributes of the victim’s machine)
- Most of the other functions that correspond to the specific malware functionalities are the same and are listed in the same order in the binaries
- The two threats use the same malware packer
- The PDB (Program Database) paths included in the analyzed malware binaries are the same (and unique to the Dridex and FriedEx projects).
- Several Dridex and FriedEx samples have the same date of compilation (with time differences of several minutes at most) and consistent randomly generated constants (which means that the samples were probably built during the same compilation session).
- Malware binaries of both threats are compiled in Visual Studio 2015.
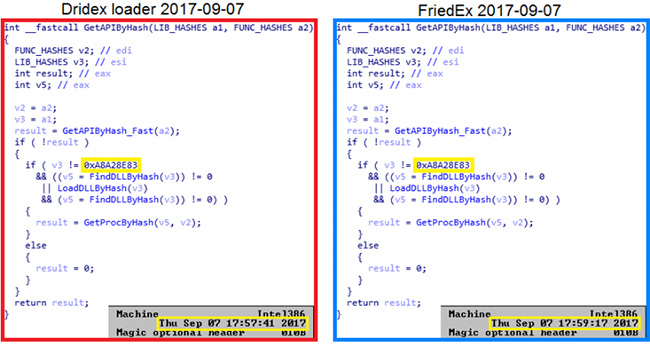
“With all this evidence, we confidently claim that FriedEx is indeed the work of the Dridex developers,” the researchers noted.
An active group
This discovery points to the group being active on multiple fronts: they consistently update the banking malware (a new code injection technique that makes it easier to avoid AV detection, a new MS Word zero-day exploit to help the malware spread), but also follow the latest malware trends and participate in them (they created their own ransomware).
FriedEx has been first detected in July 2017, concentrates on higher profile targets (companies), and is usually delivered via an RDP brute force attack. Dridex first appeared in 2014. The Dridex botnet has had its ups and downs 1,2) during the years, but continues to chug along.