Counterfeit digital certificates for sale on underground forums
Signing malicious code with valid digital certificates is a helpful trick used by attackers to maximize the odds that malware won’t be flagged by antivirus solutions and often even by network security appliances.
Digitally signed malware can also bypass OS protection mechanisms that install or launch only programs with valid signatures.

As it happens, it has recently been pointed out that the practice of signing malicious code is more widespread than previously thought.
But, while there’s a general assumption (granted, backed by many instances) that attackers prefer using stolen certificates to sign their malicious payloads, Recorded Future researchers have discovered that, for the last couple of years, a few underground vendors have been offering legitimately issued code signing certificates and domain name registration with accompanying SSL certificates.
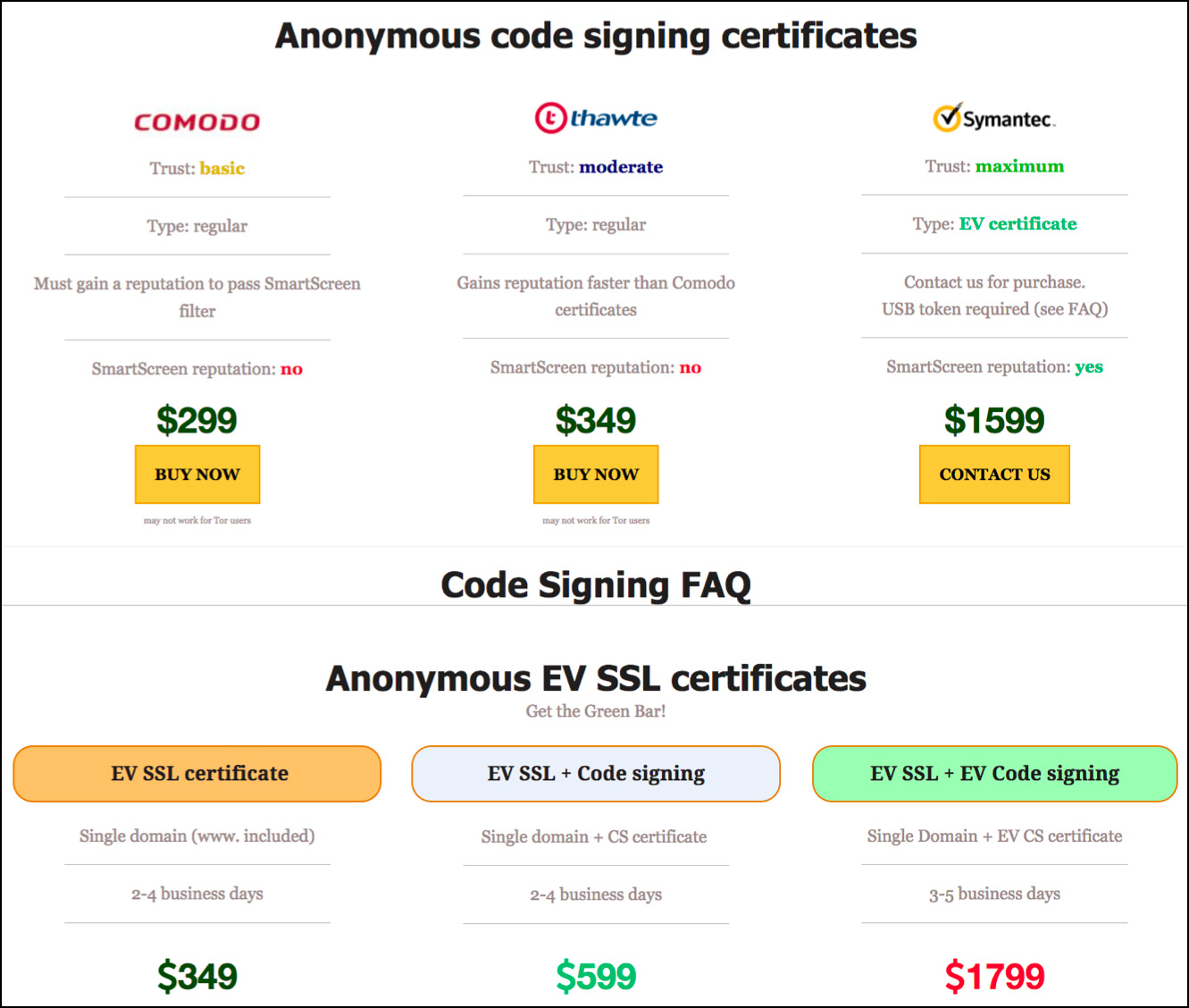
The vendors
“C@T,” one of the first providers of this commodity, started in early 2015, and sold Microsoft Authenticode capable of signing 32/64b versions of various executable files, as well as Microsoft Office, Microsoft VBA, Netscape Object Signing, and Marimba Channel Signing documents, and supported Silverlight 4 applications. He apparently even sold Apple code signing certificates.
“In his advertisement, C@T explained that the certificates are registered under legitimate corporations and issued by Comodo, Thawte, and Symantec — the largest and most respected issuers,” the researchers shared.
“The seller indicated that each certificate is unique and will only be assigned to a single buyer, which could be easily verified via HerdProtect.com. According to C@T, the success rate of payload installations from signed files increases by 30 to 50 percent, and he even admitted to selling over 60 certificates in less than six months.”
Since then, other sellers waded into these waters, but only two remain and continue to offer their wares to Russian-speaking actors in the Eastern European underground – and they aren’t cheap:
Testing the effectiveness of this approach
“According to the information provided by both sellers during a private conversation, to guarantee the issuance and lifespan of the products, all certificates are registered using the information of real corporations. With a high degree of confidence, we believe that the legitimate business owners are unaware that their data was used in the illicit activities,” the researchers noted.
To prove the effectiveness of these offerings, they even managed to convince one of these vendors to sign an executable of a previously unreported Remote Access Trojan (RAT) with a recently issued Comodo certificate.
When the encrypted but not signed executable was fed into VirusTotal, it was flagged as malicious by eight solutions. When encrypted and signed, it was caught by two – and that number fell to one when the same test was conducted for a non-resident version of the payload.
Not for everybody
So, the option to sign malicious code with legitimate certificate exists, but who’s going to make use of it?
With encryption services readily available at $10-$30 per each encryption, the researchers seriously doubt that low-level cybercrime operations will opt for using counterfeit certificates.
“However, undoubtedly, more sophisticated actors and nation-state actors who are engaged in less widespread and more targeted attacks will continue using fake code signing and SSL certificates in their operations,” they noted.