Phishing PyPI users: Attackers compromise legitimate projects to push malware
PyPI, the official third-party software repository for Python packages, is warning about a phishing campaign targeting its users.
“We have additionally determined that some maintainers of legitimate projects have been compromised, and malware published as the latest release for those projects. These releases have been removed from PyPI and the maintainer accounts have been temporarily frozen,” the PyPI team noted.
The malicious releases that they are currently aware of are:
- exotel – v0.1.6
- spam – v2.0.2 and v4.0.2
- deep-translator – v1.8.5
They also added that they’ve “taken down several hundred typosquats that fit the same pattern.”
The phishing campaign
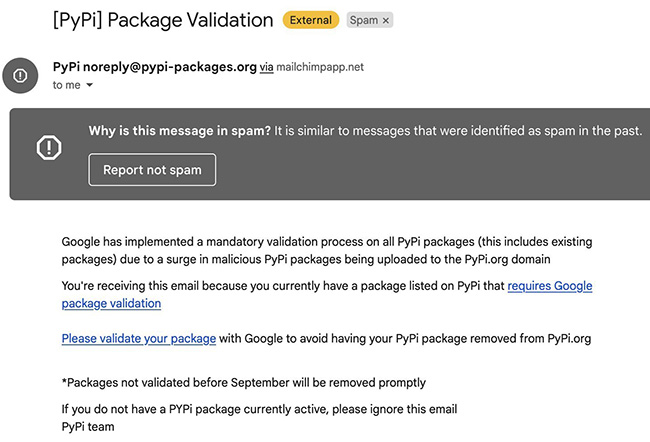
The phishing message came via email, warning users that they have to perform “package validation” to avoid their PyPI packages being removed from the online repository:
A click on the provided link took victims to a phishing site mimicking PyPI’s login page.
“We are unable to determine whether the phishing site was designed to relay TOTP-based two-factor codes. Accounts protected by hardware security keys are not vulnerable,” the PyPI team said.
According to Checkmarx security researcher Aviad Gershon, “The phishing attempt and the malicious packages are linked by the domain linkedopports[.]com, which appears in the malicious package code and also functions as the location to which the phishing site tries to send the stolen credentials.”
The malicious packages are trying to download and execute a file from another URL, which is atypically large and signed with a valid signature, he added, and noted that they discovered another unreported domain related to this attacker’s infrastructure, hosting a site imitating the website of the LedgerLive crypto wallet app.
Gershon has also apparently shared a list of the malicious typosquatting packages he spotted during the investigation.
PyPI’s response
Threat actors (and occasionally security researchers) are constantly trying – and sometimes succeeding – to get malicious packages on PyPI.
“We’re actively reviewing reports of new malicious releases, and ensuring that they are removed and the maintainer accounts restored. We’re also working to provide security features like 2FA more prevalent across projects on PyPI,” the PyPI team said in the wake of this latest security incident.
PyPI (i.e., the Python Software Foundation, which runs the repository) will soon start requiring maintainers of critical projects/packages to have 2FA enabled to publish, update, or modify them, and is distributing 4000 hardware security keys to help them.
The team has urged users who have fallen for the phish to reset their password and 2FA recovery codes, and to review their account for suspicious activity.
UPDATE (August 25, 2022, 07:35 a.m. ET):
The article has been amended to reflect the fact that the enabling of 2FA has not yet been mandated for maintainers of critical projects/packages. The requirement will go into effect “in the coming months.”