HashiCorp HCP Boundary helps organizations struggling with security as they transition to the cloud
HashiCorp released HashiCorp Cloud Platform (HCP) Boundary, a secure remote access product. With this release, Boundary joins HCP Vault and HCP Consul to provide a zero trust security solution to secure applications, networks, and people built for the cloud.
As organizations move to the cloud and adopt cloud operating models, they require a different approach to security — commonly referred to as zero trust security — where the default security posture is to trust nothing, authenticate and authorize everything. But the gap between legacy security postures and the accelerated move to the cloud is contributing to a significant increase in security breaches. According to the HashiCorp State of Cloud Strategy Survey, 89% of respondents believe security is the number one determining factor for cloud success, which is driving organizations to adopt zero trust security postures.
HashiCorp’s approach to zero trust security focuses on using identity to secure applications, networks, and people across multiple clouds, on-premises, and hybrid environments, which reduces the attack surface and automates complex security workflows. This ensures people, machines, and services are authenticated, every action is authorized, and data is protected.
“As organizations continue to expand their cloud estates, they must shift their security strategies to keep up with the growth and complexity of applications, network components, and cloud-based systems,” said Armon Dadgar, co-founder and CTO, HashiCorp.
“At HashiCorp, we have always believed that identity is the foundation for zero trust security for applications, networks, and users. With HCP Boundary, companies now have a modern solution for privileged access management, securing access in dynamic, ephemeral environments for their workforce. We think we’ve reached an important milestone for our customers by delivering a security solution built for today’s threat and infrastructure landscape.”
As organizations move out of traditional datacenters and into multiple clouds, hybrid, and edge environments, securing their infrastructure becomes more complex at scale. The HashiCorp zero trust solution covers all three of these aspects:
- Applications: HashiCorp Vault provides a consistent way to manage application identity by integrating many platforms and identity providers. Vault enables fine-grained access control and authorization between applications and databases, including dynamically rotating credentials, PKI certificates, and API tokens, while also ensuring application data is always secure in transit and at rest.
- Networks: HashiCorp Consul secures network traffic between applications and services, enabling fine-grained access control policies, observability, and traffic shaping. Consul integrates with Vault’s identity platform to leverage application identity for the policies and to allow dynamic PKI.
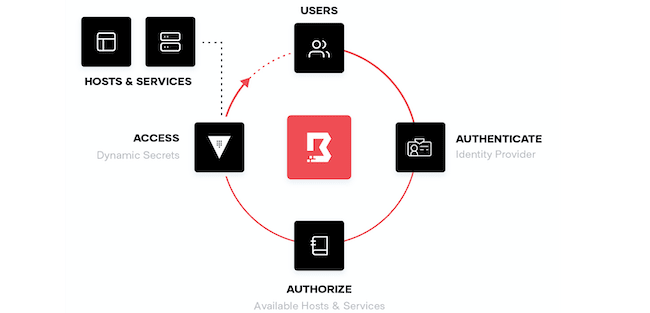
- People: HashiCorp Boundary ensures the right people have access to the right systems and cloud services while removing the need to distribute and issue credentials, expose private networks, or manage static credentials. Boundary integrates with Vault to issue just-in-time credentials and ensure ephemeral access to critical systems.
General availability of HCP Boundary
HCP Boundary provides a secure remote access solution for a cloud operating model, offering improvements over existing software-defined perimeter (SDP) solutions, like VPNs, and privileged access management (PAM) solutions that are IP-driven and highly manual. With HCP Boundary, teams gain fine-grained authentication and authorization controls, rapid user onboarding, and automated workflows for target discovery and credential management for ephemeral resources. As a cloud-based service, HCP Boundary benefits organizations struggling with security as they transition to the cloud, driven by people and skills shortages.
HCP Boundary allows teams and users to access the critical systems they need while abstracting the session connection, establishment, credential issuance, and revocation. Boundary provides operations and security teams the ability to dynamically pull in cloud service catalogs and on-premises resources and map out policies to which systems, users, and groups should have access. To do this Boundary leverages Vault to provide passwordless connections, and after each use revokes the credentials. This helps ensure critical information like credentials, networks, and resources are never exposed to the user or outside actors.
In addition to core secure remote access capabilities, Boundary also offers:
- Identity platform integration with Microsoft Azure Active Directory and Okta, along with many other identity platforms that support OpenID Connect to onboard trusted identities and delegate authentication
- Role-based access control (RBAC) to provide broad or fine-grained access to people throughout your organization
- Passwordless authentication for seamless integration with dynamic secrets and Vault
- Automated service discovery for streamlined discovery and configuration of targets. Dynamic host catalogs are currently available with Microsoft Azure and AWS, as well as direct HashiCorp Terraform integration to pull in resources under management
- Session visibility and logging to get insights into session metrics, events, logs, and traces with the ability to export data to business intelligence and event monitoring tools