AI tools like ChatGPT expected to fuel BEC attacks
Across all BEC attacks seen over the past year, 57% relied on language as the main attack vector to get them in front of unsuspecting employees, according to Armorblox.
In other trends to watch, vendor compromise and fraud are rising as a new attack vector and graymail is wasting 27 hours of time for security teams each week.
Attacks target technology organizations
The report is based on data gathered across more than 58,000 customer tenants, analyzing over 4 billion emails and stopping 800,000 threats every month.
SMBs are particularly vulnerable to vendor fraud and supply chain email attacks. More than half of vendor compromise attacks targeted technology organizations (53%).
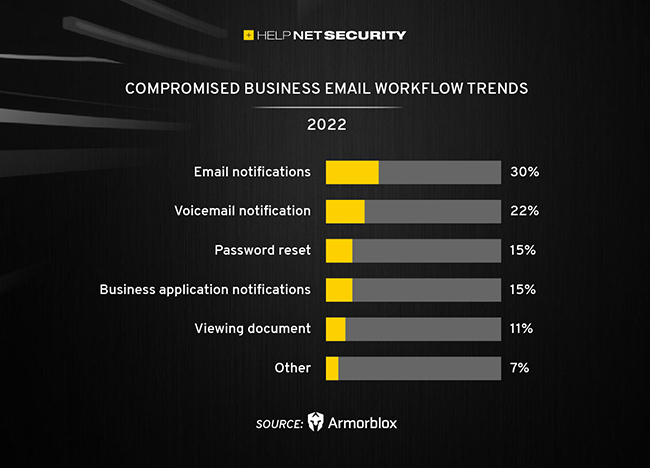
Bad actors are still infiltrating legitimate business workflows to steal sensitive business information. Business workflows involving email notifications were the most compromised, a significant uptick over 2021. Half of all attacks involve sensitive user data, such as user login credentials (52%).
Language remains the main attack vector in BEC attacks
BEC attacks continue to evolve. Language remains the main attack vector in 4 out of 5 (77%) BEC attacks that bypassed legacy solutions in 2022.
With the widespread use of email for business communications, half of account compromise attacks targeted SMBs (58%), proving to be a persistent and prevalent threat.
20% of BEC attacks involved graymail or unwanted solicitation and security teams can find themselves spending upwards of 27 person hours a week manually sorting and deleting graymail across inboxes. Of all attacks in 2022, half bypassed legacy security filters (56%). In 2022, there was a 70% increase in phishing attacks, compared to 63% in the previous year.
BEC expected to flood user mailboxes in 2023
Further, financial fraud attacks such as payroll, payment, and invoice fraud increased by 72% over 2022 and are expected to continue to rise in 2023 with banking turmoil in the headlines.
With tools such as ChatGPT, in 2023 it is expected to see a significant increase in the total number of BEC emails that flood user mailboxes inside of organizations. With an increasing hybrid approach to work, more campaigns will rise that use work-from-home-related reasons to target employees.
“Based on threats analyzed by Armorblox across our customer base of over 58,000 organizations, we see over half of email attacks targeting critical business workflows aim to exfiltrate sensitive user data. These attacks often involve bad actors infiltrating legitimate business communications to alter sensitive business information, such as assigning new routing numbers for payment requests,” said DJ Sampath, CEO of Armorblox.
“These attacks use language as the primary attack vector to impersonate trusted SaaS applications, vendors, and VIPs. This only increases the critical need for organizations to augment native and legacy security layers with modern API-based solutions that use a broad set of deep learning algorithms, machine learning models, data science approaches, and natural language-based techniques to understand the content and context of communications, and protect against these targeted attacks,” concluded Sampath.