Autoswagger: Open-source tool to expose hidden API authorization flaws
Autoswagger is a free, open-source tool that scans OpenAPI-documented APIs for broken authorization vulnerabilities. These flaws are still common, even at large enterprises with mature security teams, and are especially dangerous because they can be exploited with little technical skill.
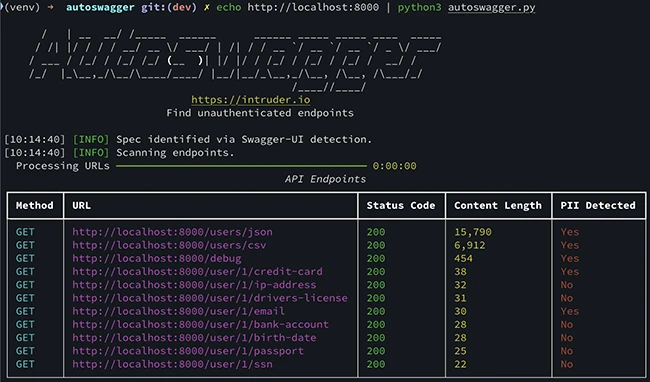
Autoswagger begins by detecting API schemas across a range of common formats and locations, starting with a list of an organization’s domains. It scans for OpenAPI and Swagger documentation pages, sending requests to each host to locate valid schemas. Once identified, it parses the API specifications and automatically generates a list of endpoints to test, taking into account each endpoint’s definition, required parameters, and expected data types.
From there, Autoswagger executes targeted scans to identify broken authorization flaws by:
- Sending requests to each endpoint using valid parameters pulled from the documentation.
- Flagging endpoints that return a valid response instead of expected HTTP 401 or 403 errors, which would normally indicate proper access control.
- Highlighting endpoints where authentication is missing or ineffective.
- For more advanced use cases, Autoswagger can be run with the
--bruteflag to simulate bypassing validation checks. This helps uncover flaws in endpoints that require specific data formats or values, which may reject generic input.
The tool analyzes any successful responses for signs of exposed sensitive data, such as PII, credentials or internal records. Any endpoint missing proper authentication and returning sensitive information is included in the output report.
“Exposing documentation for your API effectively increases your attack surface, and as a defence in depth measure, you should not expose API documentation unless it’s a business requirement,” said Daniel Andrew, Head of Security at Intruder. “The lesson here is, in addition to regular API scanning after each development iteration, that you shouldn’t publicly document your APIs unless you can’t avoid it. Without a ‘map,’ this kind of vulnerability becomes much harder for attackers to exploit.”
Autoswagger is available for free on GitHub.

Must read:
- 35 open-source security tools to power your red team, SOC, and cloud security
- GitHub CISO on security strategy and collaborating with the open-source community

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
