CISOs say they’re prepared, their data says otherwise
Most security teams believe they can act quickly when a threat emerges. But many don’t trust the very data they rely on to do so, and that’s holding them back.
A new Axonius report, based on a survey of 500 U.S.-based IT and security leaders, shows a disconnect between perceived readiness and actual performance in vulnerability and exposure management. While 90% of respondents said their organization is prepared to act when a threat is found, only 25% said they trust the data in their security tools.
That’s a problem. Data is at the center of everything in security, from asset visibility to patch prioritization. If CISOs and their teams can’t rely on that data, their ability to act fast and effectively is compromised.
“Effective exposure management depends on reliable, trustworthy data. No amount of automation or AI integration can compensate for a broken data foundation. Until that gap is addressed, the risk of a serious breach only grows,” said Ryan Knisley, chief product strategist at Axonius.
Mistrust in data is widespread
The report finds that inconsistent, incomplete, and inaccurate data are the top reasons leaders don’t trust what their tools are telling them. These issues make it harder to prioritize vulnerabilities, assess risk, and coordinate response efforts across teams and tools.
This lack of confidence shows up in the numbers. Four in five organizations take longer than 24 hours to remediate a critical vulnerability. Only about 30% run vulnerability or exposure assessments on a weekly or daily basis. That leaves many teams flying blind between assessments.
Tools abound, but insights don’t always follow
Most organizations use multiple tools to manage vulnerabilities and exposures. But more tools don’t always mean better outcomes, especially when data is siloed or hard to correlate.
The report points out that 98% of organizations use more than one tool for vulnerability management, and 83% say they can fix critical vulnerabilities within two weeks. Yet slow remediation and low trust in data suggest that adding more tools isn’t solving the problem. Integration remains a major hurdle, with 27% of leaders citing it as a challenge when remediating vulnerabilities.
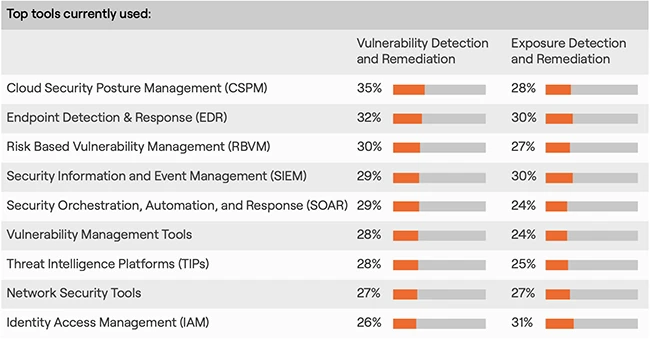
Risk-based approaches help, but need better data
When deciding what to fix first, organizations most commonly rely on a risk-based approach (39%), automation (32%), and CVSS scores (29%). These methods are only as effective as the data feeding them. Without accurate, real-time information, even the best frameworks can fall short.
Continuous Threat Exposure Management (CTEM) is gaining traction as one way to improve. About 58% of organizations in the survey have adopted CTEM, and another 34% plan to. But adoption isn’t easy. Integration across platforms and measuring effectiveness are top concerns. And again, the underlying issue often comes back to data quality.
AI and automation are promising with caveats
Leaders are also turning to AI and automation to speed up detection and remediation. Common uses include automated patching (42%), scanning (40%), and risk-based prioritization (40%). But as with CTEM, success depends on data that’s accurate, timely, and accessible across systems.
Some leaders are optimistic. About 31% believe AI and automation will become integrated into security operations, and 27% see them enhancing decision-making with human oversight still required.