Win-DDoS: Attackers can turn public domain controllers into DDoS agents
SafeBreach researchers have released details on several vulnerabilities that could be exploited by attackers to crash Windows Active Directory domain controllers (DCs), one one of which (CVE-2025-32724) can also be leveraged to force public DCs to participate in distributed denial-of-service (DDoS) attacks.
Win-DDoS – as the researchers dubbed this new attack technique – hinges on the attackers’ ability to trick public DCs into connecting to a Lightweight Directory Access Protocol (LDAP) server they set up, which instructs them (via LDAP referrals) which specific victim server they should overwhelm with requests.
CVE-2025-32724 and the Win-DDoS technique
Domain controllers are the servers that manage security, authentication, and access control within a network domain. Though alternatives exists, in most organizations domain controllers are usually Windows Server machines running Active Directory Domain Services (AD DS).
The researchers’ past exploration of how to exploit the LDAPNightmare vulnerability (CVE-2024-49113) has pushed them to identify similar DoS vulnerabilities in Windows Server and Windows:
- CVE-2025-32724, which allows uncontrolled resource consumption in Windows Local Security Authority Subsystem Service (LSASS), can be used by attackers to DoS a vulnerable, internet-exposed server or to make it participate in a Win-DDoS attack
- CVE-2025-26673 and CVE-2025-49716, which allow for uncontrolled resource consumption in Windows LDAP and Windows Netlogon, respectively, may be used to DoS a vulnerable DC
- CVE-2025-49722, allowing uncontrolled resource consumption in Windows Print Spooler Components, can be used to crash DCs and all other Windows machines in a domain
The first three vulnerabilities can be triggered remotely by unauthenticated attackers. The last requires limited privileges (i.e., they must first authenticate as a user, but any user account will do).
“The vulnerabilities we discovered are zero-click, unauthenticated vulnerabilities that allow attackers to crash these systems remotely if they are publicly accessible, and also show how attackers with minimal access to an internal network can trigger the same outcomes against private infrastructure,” the researchers noted.
“Our findings break common assumptions in enterprise threat modeling: that DoS risks only apply to public services, and that internal systems are safe from abuse unless fully compromised. The implications for enterprise resilience, risk modeling, and defense strategies are significant.”
With Win-DDoS, they have also demonstated how attackers can turn the Windows platform into a weapon without having to breach systems, achieve code execution or without having valid credentials.
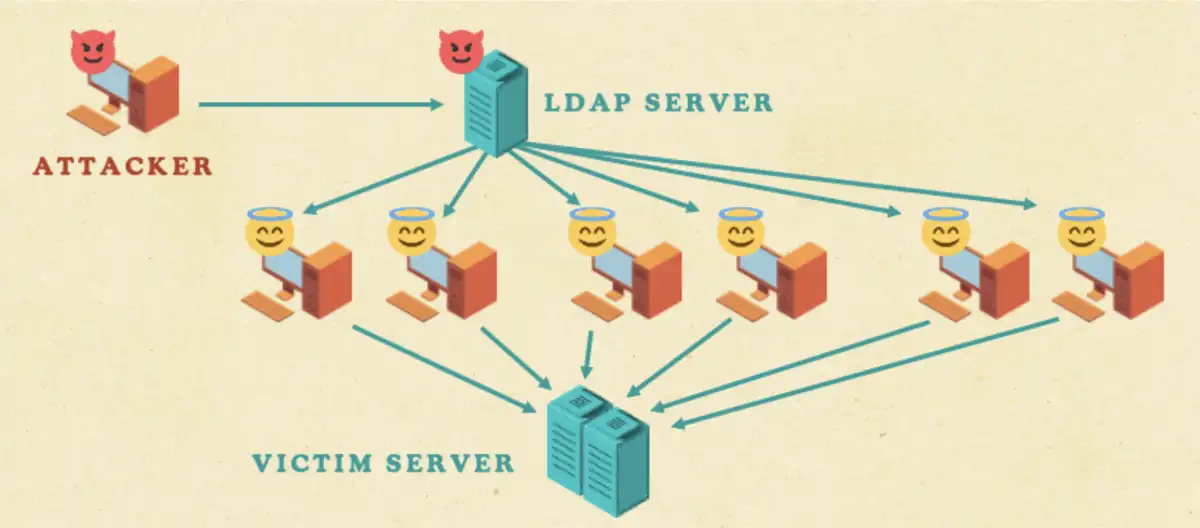
The attack involves:
- Sending a specially crafted RPC call to internet-reachable DCs to turn them into CLDAP clients and make them reach out to the attacker’s CLDAP server
- The attacker’s CLDAP server responding with an LDAP referral that tells the DC to contact the attacker’s LDAP/TCP server next
- The attacker’s LDAP/TCP server responding with a referral list of thousands of LDAP URLs that resolve to the same victim IP and port
“The DCs then send an LDAP query to that port, and that port can be a port that serves a web server, for example. Due to the fact that web servers do not expect LDAP packets, which are not valid HTTP packets, most of them just close the TCP connection as a result. Once the TCP connection is aborted, the DCs continue to the next referral on the list, which points to the same server again. And this behavior repeats itself until all the URLs in the referral list are over, creating our innovative Win-DDoS attack technique,” the researchers explained.
What to do?
All four vulnerabilities have been patched by Microsoft issuing security updates for supported Windows Servers and Windows versions in April, June and July 2025. Now that the details of these vulnerabilities and exploit modules are public, organizations that have yet to implement the patches should do it sooner rather than later.
“Organizations must assume that all of their servers and endpoints can be targeted for DDoS attacks, whether they are public facing or not. In response, they should set up proper mitigations for such attacks in their infrastructure, including the ability to both defend assets and also quickly identify the source of such attacks,” SafeBreach researchers Or Yair and Shahak Morag advised.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
