Picus Security uses AI to turn threat intelligence into attack simulations
Picus Security launched new AI-powered breach and attack simulation (BAS) capabilities within the Picus Security Validation Platform. This introduces a new level of speed and intelligence, enabling security teams to create and simulate complex attack scenarios, validate the effectiveness of their defenses and prioritize actions that reduce real-world risk.
The speed and scale of new threats have outpaced traditional approaches to validation. Even with automation, legacy BAS tools require lengthy setup and expert tuning to keep up with evolving adversaries. As a result, defenders are left reacting to attacks that have already happened instead of proactively preparing for what’s next.
Picus’ new AI-powered capabilities close that gap by transforming how organizations emulate attacker behavior and validate security controls. Leveraging multi-agent orchestration, conversational threat builder and a continuously updated threat library, Picus automatically creates attack scenarios from user prompts and converts live threat intelligence into runnable, ATT&CK-mapped simulations, reducing the time to validate new threats from days to minutes.
“The industry is at a turning point. Generative AI is redefining security validation by empowering security teams to instantly validate an organization’s readiness for emerging threats and high-profile breaches in the news,” said Volkan Ertürk, CTO, Picus Security.
“This advancement isn’t a buzzword; it builds exposure validation into day-to-day operations. Instead of mobilizing everyone for emergency patching, AI-powered validation converts live intel into attack simulations, verifies control effectiveness in seconds and enables teams to patch what matters first, reduce immediate risk and buy crucial time,” Ertürk continued.
A new standard for intelligent validation
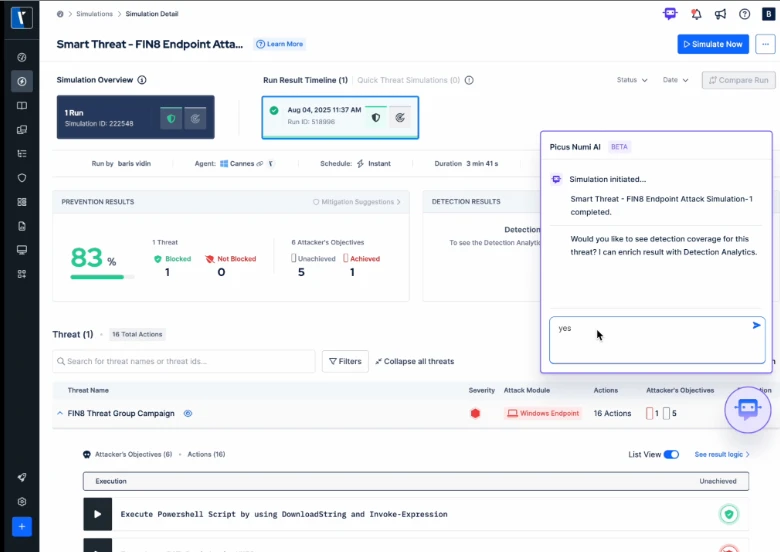
With AI powering attack development, simulation execution and result interpretation, Picus enables a new model for continuous exposure validation. Key advancements include:
- AI-generated adversary emulation: Multi-agent orchestration automates research, payload and TTP mapping from live threat intelligence feeds.
- Conversational simulation control: Through the platform’s Numi AI assistant, teams can request, run and analyze simulations using natural language commands.
- Evidence-based insights: AI summarizes simulation results into actionable reports that measure control effectiveness, prioritize exposures and quantify security improvements.
These advancements accelerate organizations’ adoption of continuous threat exposure management (CTEM) practices, helping them operationalize threat intelligence and maintain real-time visibility into their security posture.