Maltrail: Open-source malicious traffic detection system
Maltrail is an open-source network traffic detection system designed to spot malicious or suspicious activity. It works by checking traffic against publicly available blacklists, as well as static lists compiled from antivirus reports and user-defined sources. These “trails” can include domain names, URLs, IP addresses, or even HTTP User-Agent values. On top of that, Maltrail can use optional heuristic methods to identify new or unknown threats, such as emerging malware.
Maltrail follows a Traffic -> Sensor <-> Server <-> Client architecture that keeps things simple but powerful.
It starts with the sensor, a small, standalone component that monitors network activity. Sensors usually run on Linux systems that are connected to a SPAN or mirror port, or they can sit inline on a Linux bridge. They can also operate on their own, like in a honeypot environment. The sensor’s job is to watch network traffic and flag anything suspicious, such as blacklisted domain names, URLs, or IP addresses. When it spots something, it sends the details to a central server, where all the activity logs are stored.
If the sensor and server run on the same machine (which is the default setup), the data is saved locally. In larger environments, sensors can send log data to a remote server over UDP.
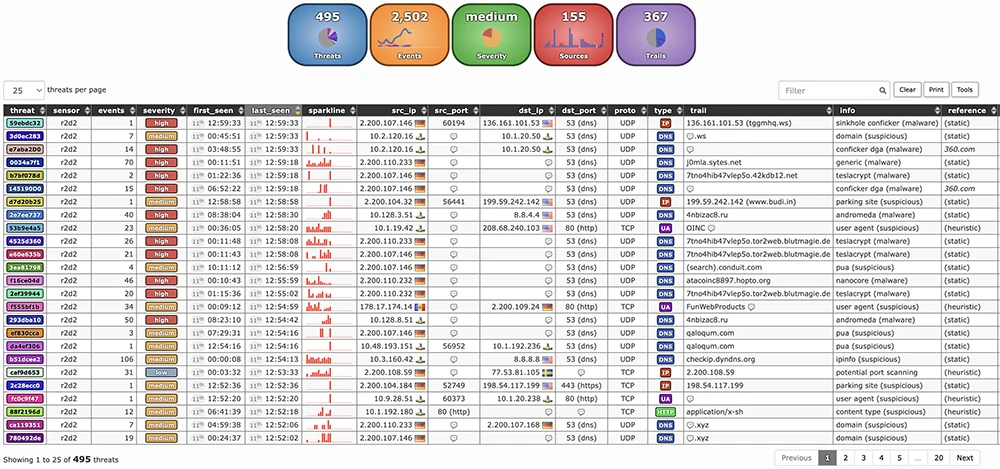
The server does the heavy lifting on the backend. It stores all event data and supports the reporting web interface. By default, both the server and sensor run together, but to keep things fast and avoid slowing down traffic monitoring, the reporting tool relies on a “fat client” model. That means your web browser does most of the work when processing and visualizing data.
When you open a report, the server sends event logs for the selected 24-hour period to your browser in compressed chunks. The browser then processes the data and displays it in a clean, compact report that can handle thousands of events without lag.
For smaller or simpler setups, you can skip the server completely. The sensor can log everything locally, and you can review the data manually or open it with any CSV viewer.
Maltrail is available for free on GitHub.

Must read:
- 35 open-source security tools to power your red team, SOC, and cloud security
- GitHub CISO on security strategy and collaborating with the open-source community

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!