Crypto crime hits record levels as state actors move billions
Nation-state involvement in crypto increased in 2025, signaling a shift in how on-chain crime operates.
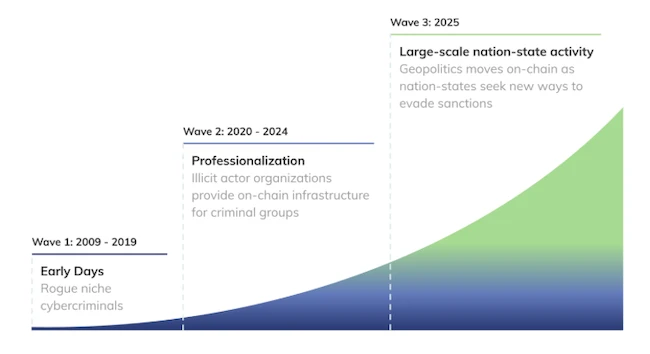
Three waves of crypto crime (Source: Chainalysis)
Research from Chainalysis shows that crypto-related crime has grown more organized over recent years, with illicit groups running large-scale on-chain infrastructure to support cross-border criminal networks, procure services, and launder funds.
That same infrastructure is being used by state actors, both through established professional service providers and through custom-built systems designed to evade sanctions.
Illicit transaction value reaches a record
Wallets identified as being associated with illicit activity received at least $154 billion in cryptocurrency during 2025. This figure represents a 162% increase from 2024 and is the highest annual total recorded in this research.
The estimate reflects transactions tied to wallets identified at the time of analysis. The report states that the figure represents a lower bound and may increase as additional illicit addresses are identified.
Illicit activity accounted for less than one percent of total cryptocurrency transaction volume during the year.
Stablecoins accounted for 84% of illicit transaction volume in 2025. This made stablecoins the most commonly used asset in illicit on-chain activity.
The report notes that stablecoins are widely used in cross-border transactions and appear frequently in illicit cryptocurrency activity. Other cryptocurrencies were present at lower volumes.
State-linked actors contribute significant volume
North Korean-linked hacking groups stole approximately $2 billion in cryptocurrency during 2025. The largest single incident involved the exploit of the Bybit exchange, which resulted in losses of nearly $1.5 billion. This event is identified as one of the largest on-chain thefts recorded.
Russian-linked activity also appeared in the data. A ruble-backed stablecoin known as A7A5 processed more than $93 billion in on-chain transactions within its first year. These transactions were associated with sanctions evasion and financial flows involving restricted entities.
Iran-aligned networks were also linked to criminal use of cryptocurrency. Wallets connected to sanctioned Iranian entities processed more than $2 billion in cryptocurrency. The activity was associated with oil sales, procurement, and related transactions.
Chinese money laundering networks played an expanded role during 2025 by providing services that support the movement and conversion of illicit funds. These services appeared in connection with multiple forms of illicit activity, including fraud schemes, scam operations, activity linked to state-associated hacking groups, and transactions involving sanctioned entities and designated organizations.
Crypto crime moves beyond the screen
There have been growing connections between on-chain activity and violent crime. Human trafficking operations have turned to cryptocurrency, and physical coercion attacks have become more common, with criminals using violence to force victims to transfer assets. In some cases, attackers timed these assaults to coincide with periods of elevated crypto prices.
Familiar cybercrime is still active
While nation-state activity generated headlines, conventional cybercriminal operations persisted through 2025. The ecosystem still contained ransomware operators, malware distribution networks, fraud rings, and darknet marketplaces that moved funds across jurisdictions.
These cybercriminals rely on a complex web of infrastructure, including domain registration services and hosting platforms that resist takedowns and enforcement.

Exam prep hacked: Study tips and tricks that really work