Google disrupts proxy network used by 550+ threat groups
Google has disrupted Ipidea, a massive residential proxy network consisting of user devices that are being used as the last-mile link in cyberattack chains.
“In a single seven day period in January 2026, GTIG observed over 550 individual threat groups that we track utilizing IP addresses tracked as Ipidea exit nodes to obfuscate their activities, including groups from China, DPRK, Iran and Russia. The activities included access to victim SaaS environments, on-premises infrastructure, and password spray attacks,” Google Threat Intelligence Group said on Thursday.
Millions of home IPs for hire
Residential proxy networks are collections of proxy servers that route internet traffic through real residential IP addresses, making it look like it’s coming from a regular household connection somewhere in the world.
“A robust residential proxy network requires the control of millions of residential IP addresses to sell to customers for use,” GTIG explained.
“To do this, residential proxy network operators need code running on consumer devices to enroll them into the network as exit nodes. These devices are either pre-loaded with proxy software or are joined to the proxy network when users unknowingly download trojanized applications with embedded proxy code. Some users may knowingly install this software on their devices, lured by the promise of ‘monetizing’ their spare bandwidth. When the device is joined to the proxy network, the proxy provider sells access to the infected device’s network bandwidth (and use of its IP address) to their customers.”
Residential proxies have legal uses when used responsibly. For example, they can be used for mraket research, price comparison, fraud verification, app testing, SEO monitoring, cybersecurity research, etc.
But, they are also used by fraudsters and other criminals for credential stuffing and account abuse, data scraping, ad fraud, ticket scalping, as well as for malware C2 obfuscation, phishing campaigns, evading detection and IP blacklists, and so on.
IP addresses in the US, Canada, and Europe are particularly desirable, Google’s threat researchers noted.
Disturping the Ipidea proxy network
According to Google, the Ipidea proxy network is operated by a Chinese company of the same name, which controls a number of other ostensibly independent proxy and VPN brands like 922 Proxy, 360 Proxy, Luna Proxy, Galleon VPN and Radish VPN.
(Previous research by Sekoia found that the residential proxy market is very opaque, and its fragmentation an illusion.)
Google crippled the proxy network by taking down C2 domains for controlling devices and proxy traffic, as well as domains used to market proxy software and the Ipidea software development kits (SDKs).
The company also pinpointed over 600 seemingly benign Android apps that use the Ipidea SDKs.
“To safeguard the Android ecosystem, we enforced our platform policies against trojanizing software, ensuring Google Play Protect on certified Android devices with Google Play services automatically warns users and removes applications known to incorporate Ipidae software development kits (SDKs), and blocks any future install attempts,” GTIG announced.
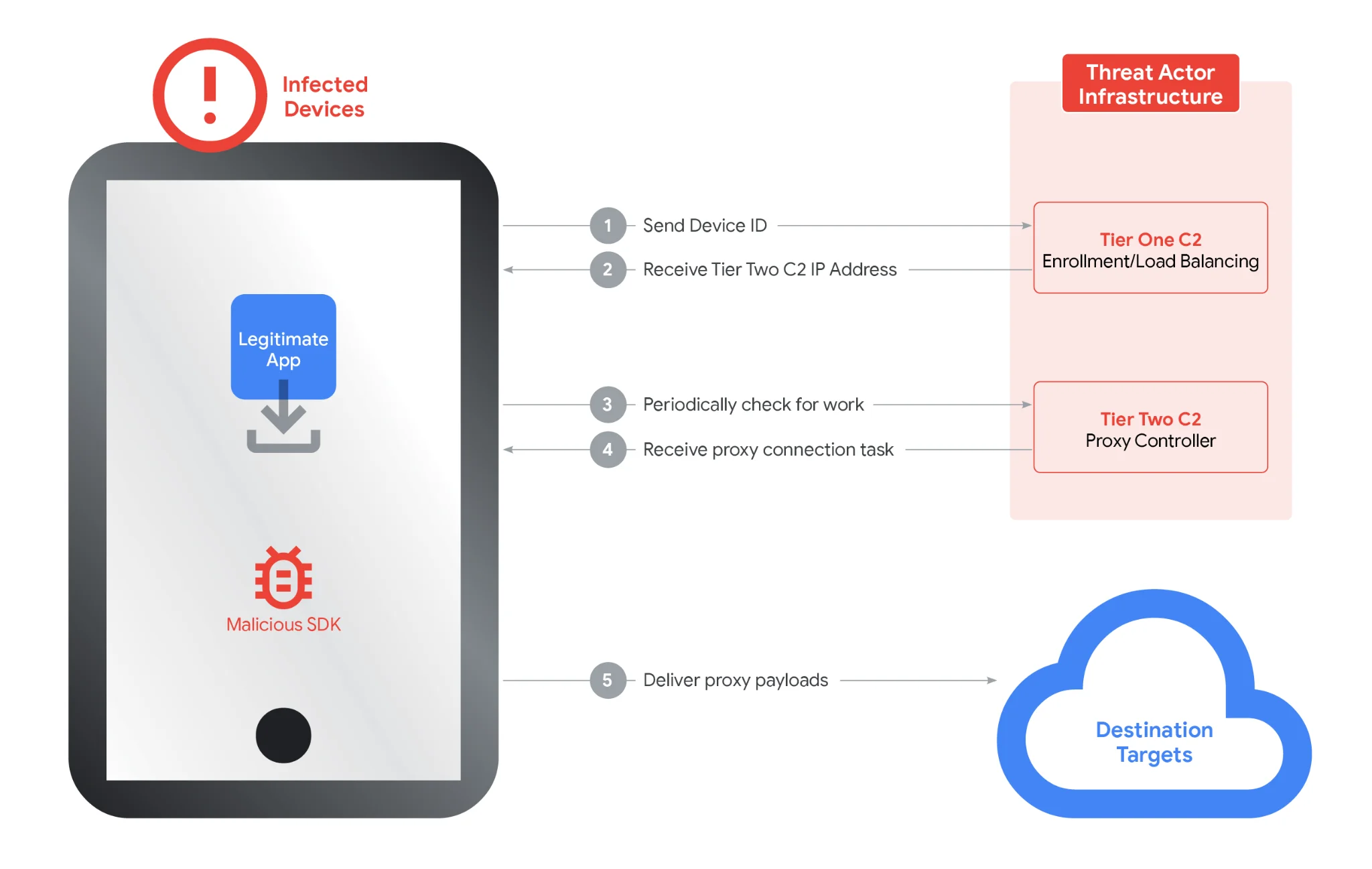
Ipidea’s infrastructure model is a two-tier system (Source: Google Threat Intelligence Group)
“We believe our actions have caused significant degradation of Ipidea’s proxy network and business operations, reducing the available pool of devices for the proxy operators by millions. Because proxy operators share pools of devices using reseller agreements, we believe these actions may have downstream impact across affiliated entities,” the threat researchers added.
Google also shared information about Ipidea’s SDKs and proxy software with platform providers, law enforcement, and research firms, so they can take additional action to limit their distribution and the harm that may arise from malicious use of the network.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
