Hackers love LOTL, this approach shuts them down
Every time cyber defenders and companies discover new ways to block intrusions, attackers change their tactics and find a way around the defenses.
“Living off the Land” (LOTL) is a prime example: since many detection tools became good at flagging malware, attackers had to find an alternative. They realized that the use of legitimate tools built into operating systems is less likely to raise warning flags, so they leaned heavily into that approach. Recent research has shown that 84% of major attacks now include LOTL techniques and the exploitation of trusted system tools such as PowerShell, WMIC, PsExec and others .
LOTL is part of a broader approach of hiding malicious activity within normal operations. Unfortunately, what’s normal for one system or user is not normal for another, so static rules and one-size-fits-all policies are not the solution for this problem.
A new approach by Bitdefender: GravityZone PHASR
Proactive Hardening and Attack Surface Reduction (PHASR) is a tool within Bitdefender’s GravityZone platform, and its goal is to reduce organizations’ exposure to threats by limiting what’s available to attackers.
Its standout feature, though, is that it does it intelligently, without adding operational burden.
PHASR distinguishes between legitimate and malicious use of system tools by:
- Learning how each endpoint and user pair actually behaves, and establishing baselines
- Tailoring protection policies at a granular level, per user and per endpoint
- Flagging and blocking suspicious deviations aligned with attacker behavior
“PHASR is very effective in reducing risk, particularly in dynamic environments and for remote workers, as it learns exactly the tools and behaviors that are employed by each user,” says Cristian Iordache, Director of Product Marketing at Bitdefender.
“For example, you might have a company that is developing blockchain technology or using certain tools that are typically used by developers. These tools will be allowed for the particular employees that need them to do their job, but not for others.”
A system tool can be used or misused. PHASR knows the difference and acts accordingly: it allows the first and blocks the second.
PHASR is built to catch the sneaky stuff: someone using a built-in Windows tool to dig around where they shouldn’t, or installing remote access software in odd ways. It knows what normal looks like for your team, so when something steps out of line, it’s on it.
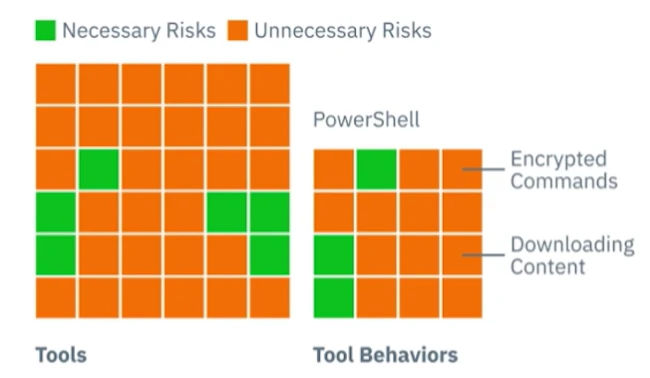
Figure 1: GravityZone PHASR allows legitimate use of native tools, but blocks specific actions frequently used by threat actors in Living off the Land attacks.
And as attackers change tactics, it “evolves”: backed by Bitdefender’s global threat intelligence, it stays current without the IT team having to do anything. New patterns and rule updates are pushed regularly, allowing the tool to separate harmless quirks from security risks.
Easy to set up and easy to use
PHASR performs a constant assessment of unnecessary access to risky tools and provides automated remediation and enforceable policy controls. Once it’s activated, existing customers will see actionable hardening recommendations within minutes.
“For new customers, the time to actionable recommendations varies,” Iordache told Help Net Security. “Some recommendations will be populated shortly after the activation while others will require a few weeks of learning, but the protection just keeps getting better.”
The tool can be set to work in two different modes: Autopilot and Direct Control.
Autopilot quietly handles threats in the background. It is well suited for companies that want to move fast without monitoring every setting, especially those managing many endpoints or remote workers.
Direct Control gives IT teams the authority to review and apply each recommendation manually. If your company relies on niche tools or has strict internal processes, this mode provides the oversight you need while still getting the benefits of PHASR’s insights.
When PHASR flags a tool or behavior, it tells you why: it’s rarely used, or known to be risky, or simply not part of someone’s typical routine.
“And we built PHASR with flexibility in mind. If it recommends a block that doesn’t make sense, you can override it with a few clicks, so there’s no need to call in a specialist,” Iordache noted.
Breaking the attack playbook reuse cycle
Attackers thrive on repetition: once they find a technique that works, they often reuse it across different targets with only small changes. This cycle makes it easier for them to scale their attacks, and that’s the reason they rely on proven tactics and techniques.
PHASR breaks this pattern by creating tailored protections for each user and device, and that means a tactic that succeeds in one environment will not necessarily work in another. This proactively nullifies the advantage attackers gain from copy-paste methods.
For defenders, this brings a measure of predictability because they can trust that controls are adjusting to the context of each system. For attackers, it introduces unpredictability because they cannot assume the same playbook will succeed twice. The result is a defense posture that is dynamic and harder to bypass.
The benefits of deploying PHASR
Deploying PHASR brings clear strategic gains for security teams and the business as a whole.
It strengthens the overall security posture by closing gaps before attackers can exploit them. Instead of waiting for an incident to reveal weaknesses, PHASR identifies and addresses them in advance. By closing the stealthy attack paths that threat actors use, it prevents their progress and exposes them, preventing a compromise from turning into a data breach.
At the same time, it reduces operational complexity by removing the need to constantly adjust and fine-tune manual rules, giving security teams more time to spend on other work that cannot be easily automated.
Compliance is another benefit: By aligning with security best practices and documenting controls, PHASR helps organizations meet regulatory and audit requirements.
Finally, it supports business continuity by protecting systems in the background without disrupting normal operations. The focus is on lowering risk while keeping people productive, which makes security a partner rather than an obstacle.
Security and business growth don’t have to compete. With Gravity Zone PHASR, you can achieve both.