Cybercriminals exploit RMM tools to steal real-world cargo
Cybercriminals are compromising logistics and trucking companies by tricking them into installing remote monitoring and management (RMM) tools, Proofpoint researchers warned.
The attackers’ end goal is to hijack freight shipments and sell the stolen goods.
How the attack unfolds
Since at least June 2025, and possibly even since January 2025, the researchers identified various campaigns aimed at getting US companies to install RMM tools like SimpleHelp, N-able, ScreenConnect, LogMeIn Resolve, Fleetdeck, and PDQ Connect.
The attackers do this by:
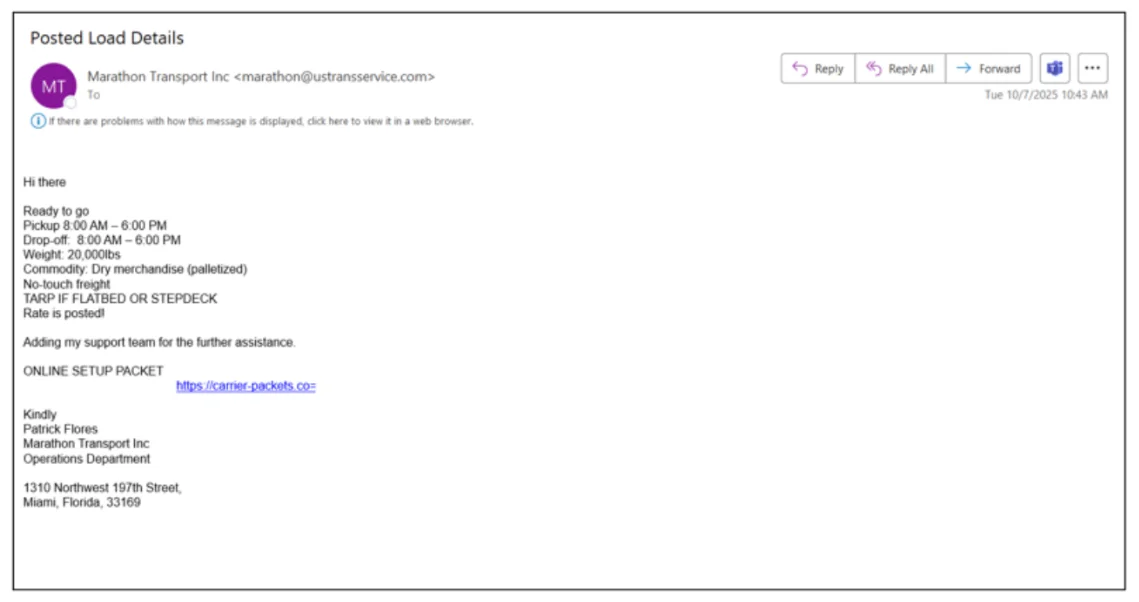
- Posting fraudulent freight listings on load boards (online marketplaces where freight brokers post loads that need to be moved, and trucking companies or independent drivers look for available loads to haul) and sending emails containing malicious URLs to carriers who inquire about the loads
- Hijacking email threads involving compromised email accounts (i.e., injecting malicious URLs into existing conversations)
- Sending emails with malicious URLs directly to asset-based carriers, freight brokerage firms, and integrated supply chain providers. “Gaining access to these entities may allow the actors to identify high-value freight loads or uncover other opportunities to further their objectives – such as posting fraudulent loads on load boards,” Proofpoint noted.
Email sent to a carrier responding to a fraudulent load posted on a load board (Source: Proofpoint)
These emails usually lead to an executable or an MSI file that, when clicked, installs an RMM tool. The landing pages and domains usually look genuine: they use generic transportation terms and have been made to look like they belong to legitimate brands.
Once the RMM tool is installed, the attackers effectively gain full control of the compromised machine and from there, can search for sensitive information about the company’s activities, and compromise the accounts they used for interacting with load boards.
“Based on campaigns observed by Proofpoint, the threat actor does not appear to attack specific companies, and targets range from small, family-owned businesses to large transport firms as described above,” the researchers noted.
“The threat actor appears to be opportunistic about the carriers that it targets and will likely attempt to compromise any carrier who responds to the fake load posting. Once a threat actor has compromised a carrier, they probably will use their knowledge of the industry and any insider information derived from other compromises to identify and bid on loads that are likely to be profitable if stolen.”
What to do?
The researchers are pretty confident that the threat actors are working with organized crime groups.
“Cargo theft is a multi-million-dollar criminal enterprise, and digital transformation has led to an increase in cyber-enabled theft,” they explained. “Cyber-enabled theft is one of the most common forms of cargo theft and relies on social engineering and a knowledge of how the trucking and transportation industries work.”
They also noted that the previously spotted campaigns aimed at getting transportation and logistics companies to install infostealers might have been mounted by the same criminals, but they can’t be sure.
If they were, the choice to switch from infostealers to RMM tools is clever, as they are less likely to be flagged as suspicious and offer much more room to maneuver: RMM tools give them live (and relatively persistent) access to target systems.
Companies can lower their risk with a few practical steps:
- Only allow RMM software that has been approved by the company’s IT administrators and block or review any attempts to download or install other RMM tools.
- Have network detections in place to spot activity related to RMM servers.
- Teach employees not to download and install .exe or .msi files sent by external senders, and to spot and report suspicious activity to the security team.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!