Conjur: Open-source secrets management and application identity
Conjur is an open-source secrets management project designed for environments built around containers, automation, and dynamic infrastructure. It focuses on controlling access to credentials such as database passwords, API keys, and tokens that applications need at runtime. The project is maintained in the open and developed with input from a user and contributor base.
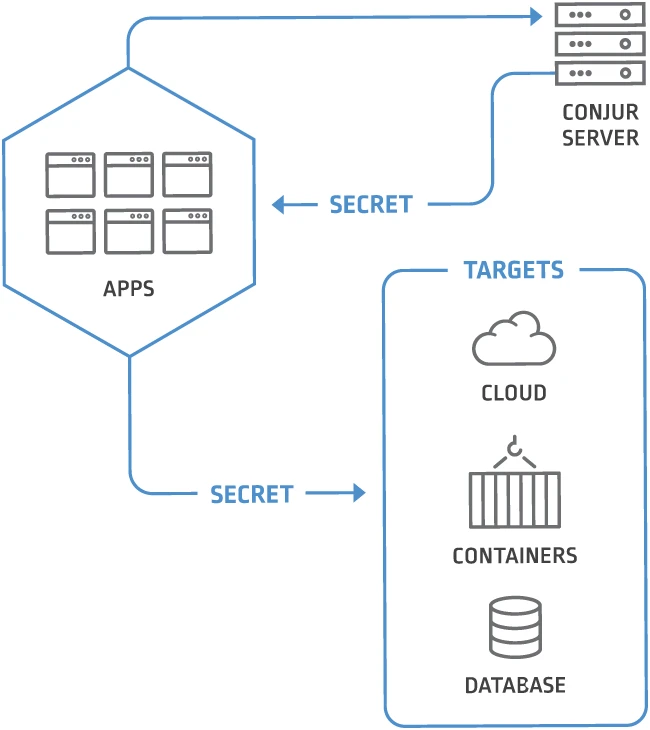
Secrets management has become a core requirement for teams running Kubernetes, CI pipelines, and microservices. Static credentials stored in files or environment variables introduce risk and create operational problems when systems scale or change. Conjur addresses this by separating secrets from application code and enforcing access through policy and identity.
Built around identity and policy
At the center of Conjur is an identity driven model. Every workload that needs a secret is assigned a unique identity. This identity is verified using mechanisms that fit the runtime environment, such as Kubernetes service accounts or host based authentication.
Policies define which identities can access which secrets. These policies are written as code and stored alongside other configuration artifacts. Teams can review, version, and audit policy changes through standard workflows. This approach supports consistent enforcement across environments and reduces reliance on manual configuration.
Conjur stores secrets in an encrypted database and never exposes them directly in configuration files. Applications request secrets at runtime through authenticated API calls. Access is granted only if the request matches the defined policy and the identity has been validated.
Designed for container platforms
Conjur is commonly deployed alongside Kubernetes and other container orchestration platforms. The project includes components that integrate with Kubernetes authentication and admission controls. Pods can retrieve secrets without embedding credentials in images or manifests.
Sidecar and init container patterns are supported for teams that want secrets injected into application memory or temporary files at startup. Direct API access is also available for applications that handle secrets programmatically.
This design aligns with short lived workloads and frequent redeployments. Secrets remain centralized even as pods and nodes come and go. Rotation of credentials happens without requiring application rebuilds.
Integration with automation pipelines
CI/CD pipelines often need access to sensitive data during build and deployment stages. Conjur supports non interactive authentication methods that fit automated systems. Build agents and deployment tools authenticate using trusted identities and receive only the secrets required for their tasks.
Policies help limit exposure by scoping access to specific pipelines or stages. Audit logs record when secrets are accessed and by which identity. Security teams gain visibility into usage patterns across development and production workflows.
Conjur is available for free on GitHub.

Must read:
- 40 open-source tools redefining how security teams secure the stack
- OpenGuardrails: A new open-source model aims to make AI safer for real-world use

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
