Cyber risk is becoming a hold-period problem for private equity firms
Private equity firms have spent years treating cybersecurity as an IT hygiene issue inside portfolio companies. That approach is getting harder to sustain as ransomware, data theft, and regulatory pressure interfere with value creation during the hold period.
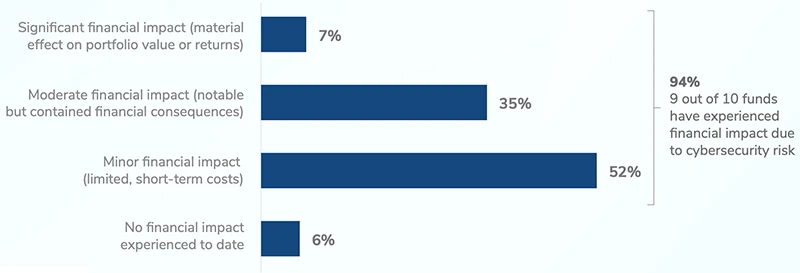
Has cybersecurity risk had any financial impact on your portfolio companies? (Source: Kroll)
A recent Kroll survey of 325 private equity portfolio leaders found that 80% of firms experienced some form of disruption tied to cybersecurity risk during the hold period over the past year. The disruption ranged from unexpected remediation costs to litigation, downtime, and integration failures after acquisitions.
Hold-period risk is also growing more frequent. Nearly 70% of respondents reported an increase in cybersecurity incidents year over year during that stage, with 22% calling the increase significant.
The findings reflect a reality many PE operating teams already see in practice: the hold period is long enough for security debt to surface, attackers to find weak points, and regulators to scrutinize portfolio controls.
Remediation costs and downtime are common
The most common disruption during the hold period was unexpected remediation spending. Forty-four percent of respondents said they incurred unplanned costs to fix inherited cyber or IT issues.
Other recurring problems included difficulty integrating IT systems across portfolio companies. Regulatory or compliance-related litigation was also common, along with direct business disruption or downtime caused by cyber incidents.
Those operational disruptions can delay planned technology consolidation projects and create friction in shared services models, especially in portfolios built through add-on acquisitions.
Regional differences also emerged. Business disruption or downtime was most common in the U.S., with lower levels reported in Europe and APAC. Litigation and regulatory burdens were more frequently reported in APAC and Europe.
Deal value is being affected
Cyber incidents are also influencing transaction outcomes. Nearly a quarter of respondents reported disruption during the pre-investment stage. Nineteen percent saw deal delays due to unresolved IT or cyber findings, 8% reported valuation reductions after cyber issues were discovered, and 2% experienced deal termination tied to unacceptable cyber risk.
Exit-stage disruption was also present. Some firms reported deal delays tied to weak exit preparedness or buyer concerns about cyber readiness. Others experienced valuation reductions after buyers uncovered cybersecurity issues.
Smaller firms reported a higher rate of deal disruption at exit. Twenty percent of firms under $1 billion in assets under management reported deal disruption due to a cybersecurity incident, compared with 8% for firms above $1 billion.
Average financial impact is $2.1 million
Financial impact is widespread. Most surveyed firms reported financial consequences tied to cybersecurity risk. Some described the impact as significant, with a material effect on portfolio value or returns.
“The average financial impact is $2.1 million, but that’s just the tip of the iceberg. The real cost emerges in regulatory investigations, deal timeline delays and continuation vehicles triggered by post-incident governance gaps; and we’re seeing that maturity matters. Our call to action is that those in the private equity ecosystem need to monitor and challenge assumptions, including compliance, reputation and defense across their entire security perimeter,” said Dave Burg, Global Group Head of Cyber and Data Resilience at Kroll.
The most common sources of financial impact were increased ongoing compliance or cybersecurity spending. Many firms also cited direct remediation and consulting costs, along with reduced valuation or exit price.
Lower-AUM firms were more likely to report valuation reductions. Forty-four percent of firms with under $500 million in AUM said cybersecurity risk reduced valuation or exit price, compared with 17% of firms with more than $25 billion in AUM.
Large firms are enforcing baseline controls
The survey found a sharp split between large and small PE firms in how cybersecurity governance is handled.
Among firms with more than $25 billion in AUM, 55% enforce a formal, mandatory baseline of cybersecurity controls across portfolio companies. For firms under $25 billion, that number drops to 12%.
Smaller firms were more likely to operate without consistent standards. Fifty-one percent reported handling cybersecurity controls on a case-by-case basis. Thirty-five percent of firms with under $500 million in AUM reported having no defined baseline at all.
Large firms also tend to formalize cybersecurity procurement. Fifty-two percent of firms with more than $25 billion in AUM reported having preferred security technology and services providers with pre-negotiated rates that portfolio companies are required to use.
Monitoring tools and staffing gaps remain
Visibility remains a persistent problem. Many respondents involved in cybersecurity procurement said they use dedicated platforms to aggregate portfolio cyber risk information, along with specialized tools for evaluating specific risks in select portfolio companies.
Smaller firms leaned heavily on manual monitoring and outsourced providers. Fifty percent reported manual monitoring methods such as periodic interview-based consulting assessments, and 53% used managed service providers.
Staffing is another weak spot. Many firms reported having no dedicated leader or team responsible for managing cybersecurity risk across the portfolio. Larger firms were more likely to assign ownership through a dedicated leader or team.