Anamarija Pogorelec

Mobile privacy audits are getting harder
Mobile apps routinely collect and transmit personal data in ways that are difficult for users, developers, and regulators to verify. Permissions can reveal what an app can …

New infosec products of the week: February 6, 2026
Here’s a look at the most interesting products from the past week, featuring releases from Avast, Fingerprint, Gremlin, and Socure. Gremlin launches Disaster Recovery Testing …

GitHub enables multi-agent AI coding inside repository workflows
GitHub has expanded Agents HQ, enabling AI coding agents such as GitHub Copilot, Claude by Anthropic, and OpenAI Codex to execute development tasks directly within GitHub and …

Microsoft launches LiteBox, a security-focused open-source library OS
Microsoft has released LiteBox, a project intended to function as a security-focused library OS that can serve as a secure kernel for protecting a guest kernel using …

Measuring AI use becomes a business requirement
Enterprise teams already run dozens of AI tools across daily work. Usage stretches from code generation and analytics to customer support drafting and internal research. …

Auto finance fraud is costing dealers up to $20,000 per incident
Auto retailers see fraud as a regular part of selling and financing vehicles, something that shows up often enough to plan around, according to Experian. Income and identity …

Sandisk brings SPRandom to open source for large SSD testing
Enterprise storage environments already run long qualification cycles as solid-state drive capacities rise and validation teams try to mirror production workloads. …
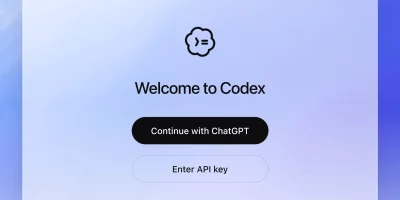
OpenAI releases Codex macOS app for agent-based software development
OpenAI has launched the new Codex app for macOS, a dedicated workspace for managing multiple AI coding agents in parallel. The app is designed to help developers reduce …

Open-source attacks move through normal development workflows
Software development relies on a steady flow of third-party code, automated updates, and fast release cycles. That environment has made the software supply chain a routine …
Product showcase: 2FAS Auth – Free, open-source 2FA for iOS
Online accounts usually rely on a password, but passwords alone can be weak if they’re reused, easily guessed, or stolen. Two-factor authentication (2FA) adds a second layer …

Cybersecurity jobs available right now: February 3, 2026
Application Security Engineer Liebherr Group | Germany | Hybrid – View job details As an Application Security Engineer, you will As an Application Security Engineer, you …

AI is flooding IAM systems with new identities
Most organizations view AI identities through the same lens used for other non-human identities, such as service accounts, API keys, and chatbots, according to The State of …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month