Zeljka Zorz

Cl0p exploits Oracle E-Business Suite zero-day in data theft, extortion campaign (CVE-2025-61882)
The Cl0p extortion gang exploited multiple Oracle E-Business Suite (EBS) vulnerabilities, including one zero-day flaw (CVE-2025-61882), “to steal large amounts of data …

Hackers claim to have plundered Red Hat’s GitLab repos
The Crimson Collective, an emerging extortion / hacker group, has made a bombshell claim on their Telegram channel: they have gained access to Red Hat’s GitLab and have …

Oracle customers targeted with emails claiming E-Business Suite breach, data theft
Unknown attackers claiming affiliation with the Cl0p extortion gang are hitting business and IT executives at various companies with emails claiming that they have exfiltrated …

North Korea’s IT workers are targeting firms beyond tech, crypto, and the U.S.
North Korea’s clandestine IT Worker (ITW) program, which is long known for targeting U.S. technology firms and crypto firms, has broadened its scope to attempt to infiltrate a …
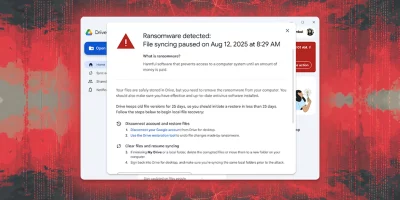
Google Drive for desktop will spot, stop and remedy ransomware damage
Google has rolled out AI-powered ransomware detection and file restoration features in Drive for desktop, Google’s official file syncing and access app for Windows and …

Too many Cisco ASA firewalls still unsecure despite zero-day attack alerts
Despite Cisco and various cybersecurity agencies warning about attackers actively exploting zero-day vulnerabilities (CVE-2025-20333 and CVE-2025-20362) in Cisco Adaptive …

Hackers love LOTL, this approach shuts them down
Every time cyber defenders and companies discover new ways to block intrusions, attackers change their tactics and find a way around the defenses. “Living off the …

CISA says it will fill the gap as federal funding for MS-ISAC dries up
The cooperative agreement between the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the not-for-profit Center for Internet Security is ending today, the …

Western Digital My Cloud NAS devices vulnerable to unauthenticated RCE (CVE-2025-30247)
Western Digital has fixed a critical remote code execution vulnerability (CVE-2025-30247) in the firmware powering its My Cloud network-attached storage (NAS) devices, and has …

Akira ransomware: From SonicWall VPN login to encryption in under four hours
Four hours or less: that’s how long it takes for Akira affiliates to break into organizations and deploy the ransomware on their systems, Arctic Wolf researchers have …

Attackers exploited critical Fortra GoAnywhere flaw in zero-day attacks (CVE-2025-10035)
CVE-2025-10035, a perfect CVSS 10.0 vulnerability in the Fortra GoAnywhere managed file transfer solution, has apparently been exploited in zero-day attacks before the patch …

Cisco ASA zero-day vulnerabilities exploited in sophisticated attacks
A widespread campaign aimed at breaching organizations via zero-day vulnerabilities in Cisco Adaptive Security Appliances (ASA) has been revealed by the US, UK, Canadian and …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month