Zeljka Zorz
New “HashJack” attack can hijack AI browsers and assistants
Security researchers at Cato Networks have uncovered a new indirect prompt injection technique that can force popular AI browsers and assistants to deliver phishing links or …

Popular code formatting sites are exposing credentials and other secrets
Widely used code formatting sites JSONFormatter and CodeBeautify are exposing sensitive credentials, API keys, private keys, configuration files and other secrets, watchTowr …
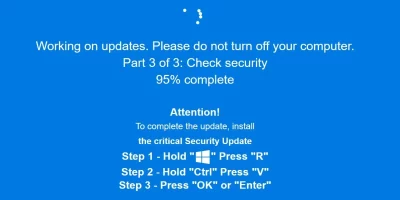
Fake “Windows Update” screen fuels new wave of ClickFix attacks
A convincing (but fake) “Windows Update” screen can be the perfect lure for tricking users into infecting their computers with malware. Add a multi-stage delivery …

Salesforce Gainsight compromise: Early findings and customer guidance
In the wake of Salesforce’s announcement about “unusual activity involving Gainsight-published applications” and the company’s revocation of access and …

Salesforce investigates new incident echoing Salesloft Drift compromise
In what may be a repeat of the Salesloft Drift supply chain compromise, Salesforce confirmed that they’ve identified unusual activity involving Gainsight-published apps …

Security gap in Perplexity’s Comet browser exposed users to system-level attacks
There is a serious security problem inside Comet, the AI-powered agentic browser made by Perplexity, SquareX researchers say: Comet’s MCP API allows the browser’s …

MacOS DigitStealer malware poses as DynamicLake, targets Apple Silicon M2/M3 devices
A new infostealer is targeting macOS users by masquerading as the legitimate DynamicLake UI enhancement and productivity utility and possibly Google’s Drive for desktop app. …

Public PoC exploit for 7-Zip vulnerability is available (CVE-2025-11001)
NHS England Digital, the technology arm of the publicly-funded health service for England, has issued a warning about a 7-Zip vulnerability (CVE-2025-11001) being exploited by …

Stealth-patched FortiWeb vulnerability under active exploitation (CVE-2025-58034)
Attackers are actively exploiting another FortiWeb vulnerability (CVE-2025-58034) that Fortinet fixed without making its existence public at the time. About CVE-2025-58034 …

Internet slowly recovers after far-reaching Cloudflare outage
A currently undisclosed issue has crippled Cloudflare’s network and has rendered a large swathe of internet’s most popular sites and services temporily …

Google patches yet another exploited Chrome zero-day (CVE-2025-13223)
Google has shipped an emergency fix for a Chrome vulnerability (CVE-2025-13223) reported as actively exploited in the wild by its Threat Analysis Group (TAG). About …

Logitech confirms data breach
Logitech, the Swiss multinational electronics and technology company best known for marketing computer peripherals and hardware, has suffered a data breach. “While the …