
Microsoft Edge 145 lands with major enterprise security upgrades
Microsoft has begun rolling out Edge 145 to the Stable release channel, adding several enterprise-focused security enhancements. The update is being deployed in phases, with …
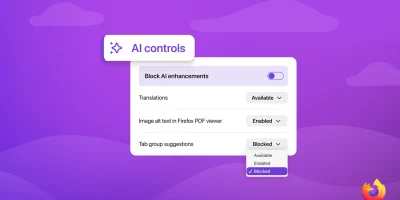
Firefox to let users manage and block AI features
Mozilla will add a set of controls in Firefox that let users manage and block GenAI features in the desktop browser. The controls will be included in Firefox version 148 on …

Grammarly and QuillBot are among widely used Chrome extensions facing serious privacy questions
A new study shows that some of the most widely used AI-powered browser extensions are a privacy risk. They collect lots of data and require a high level of browser access. The …

Fake browser crash alerts turn Chrome extension into enterprise backdoor
Browser extensions are a high-risk attack vector for enterprises, allowing threat actors to bypass traditional security controls and gain a foothold on corporate endpoints. …

Browser agents don’t always respect your privacy choices
Browser agents promise to handle online tasks without constant user input. They can shop, book reservations, and manage accounts by driving a web browser through an AI model. …
New “HashJack” attack can hijack AI browsers and assistants
Security researchers at Cato Networks have uncovered a new indirect prompt injection technique that can force popular AI browsers and assistants to deliver phishing links or …

Security gap in Perplexity’s Comet browser exposed users to system-level attacks
There is a serious security problem inside Comet, the AI-powered agentic browser made by Perplexity, SquareX researchers say: Comet’s MCP API allows the browser’s …

The browser is eating your security stack
Employees log into SaaS platforms, upload files, use AI tools, and manage customer data from a single tab. While the browser has become the enterprise’s main workspace, it …

What your browser knows about you, from contacts to card numbers
Chrome and Safari are the most popular browser apps, accounting for 90% of the mobile browsers market share, according to Surfshark. They also collect the most data. Chrome: …

Browser extensions make nearly every employee a potential attack vector
Despite being present on virtually every employee’s browser, extensions are rarely monitored by security teams or controlled by IT, according to LayerX. Most extensions have …

Best practices for ensuring a secure browsing environment
In this Help Net Security interview, Devin Ertel, CISO at Menlo Security, discusses how innovations like AI and closer collaboration between browser vendors and security …

How to enable Safe Browsing in Google Chrome on Android
To safeguard your data, Google Chrome uses Safe Browsing to protect you from: harmful websites and extensions, malicious or intrusive advertisements, malware, phishing …