
France Travail fined €5 million for failing to protect job seeker data
France data protection authority CNIL has fined public employment agency France Travail €5 million for failing to ensure the security of personal data of job seekers. …

A new framework helps banks sort urgent post-quantum crypto work from the rest
Financial institutions now have a concrete method for deciding where post-quantum cryptography belongs on their security roadmaps. New research coordinated by Europol sets out …

EU tightens cybersecurity rules for tech supply chains
The European Commission has proposed a new cybersecurity package aimed at strengthening the EU’s cyber resilience, including a revised EU Cybersecurity Act designed to secure …

Pro-Russian hacktivist campaigns continue against UK organizations
The UK’s National Cyber Security Centre reports ongoing cyber operations by Russian-aligned hacktivist groups targeting organizations in the UK and abroad. NoName057(16) …

A new European standard outlines security requirements for AI
The European Telecommunications Standards Institute (ETSI) has released a new European Standard that addresses a growing concern for security teams working with AI. The …

Sensitive data of Eurail, Interrail travelers compromised in data breach
A data breach at the Netherlands-based company that sells Eurail (Interrail) train passes resulted in the compromise of personal and sensitive information belonging to an …

AWS European Sovereign Cloud puts data, operations, and oversight inside the EU
Amazon has made the AWS European Sovereign Cloud generally available to customers across the European Union, backed by a €7.8 billion investment. According to AWS, the funding …
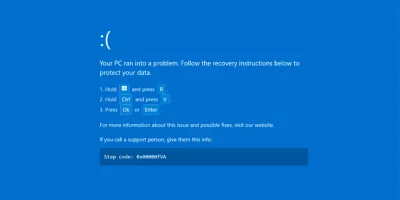
Fake Booking.com emails and BSODs used to infect hospitality staff
Suspected Russian attackers are targeting the hospitality sector with fake Booking.com emails and a fake “Blue Screen of Death” to deliver the DCRat malware. The …

What European security teams are struggling to operationalize
European security and compliance teams spend a lot of time talking about regulation. A new forecast report from Kiteworks suggests the harder problem sits elsewhere. According …

Europe’s DMA raises new security worries for mobile ecosystems
Mobile security has long depended on tight control over how apps and services interact with a device. A new paper from the Center for Cybersecurity Policy and Law warns that …

The internet isn’t free: Shutdowns, surveillance and algorithmic risks
Global internet freedom has declined for the 15th straight year, according to the latest Freedom House report. Out of 72 countries evaluated, 28 recorded declines and 17 saw …

Russia-linked hackers intensify attacks as global APT activity shifts
State-aligned hacking groups have spent the past six months ramping up espionage, sabotage, and cybercrime campaigns across multiple regions, according to ESET’s APT Activity …
Featured news
Resources
Don't miss
- Google disrupts proxy network used by 550+ threat groups
- eScan AV users targeted with malicious updates
- Google agrees to pay $135 million over Android data harvesting claims
- SolarWinds fixes critical Web Help Desk RCE vulnerabilities, upgrade ASAP!
- Open-source malware zeroes in on developer environments