Vulnerabilities in Anti-Virus Software – reaction to the McAfee Statement
During the past few months, specialists from the n.runs AG, along with other security experts, have discovered approximately 800 vulnerabilities in anti-virus products. The conclusion: contrary to their actual function, the products open the door to attackers, enable them to penetrate company networks and infect them with destructive code. The positioning of anti-virus software in central areas of the company now poses an accordingly high security risk.
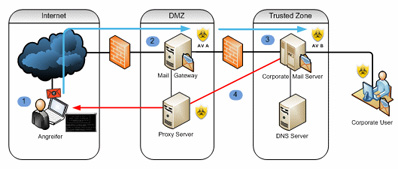
The tests performed by the consulting company and solutions developer n.runs have indicated that every virus scanner currently on the market immediately revealed up to several highly critical vulnerabilities. These then pave the way for Denial of Service (DoS) attacks and enable the infiltration of destructive code — past the security solution into the network. With that, anti-virus solutions actually allow the very thing they should instead prevent.
In this context, n.runs was able to make out so-called “parsing” as one of the main causes of this boomerang effect. The principle functions as follows: virus scanners must recognise as many “Malware” applications as possible — and thereby comprehend and process a large number of file formats. In order to be able to interpret the formats, an application must partition the corresponding file into blocks and structures. This separation of data into analysable individual parts is called “parsing”. Mistaken assumptions in the course of programming the parsing code create constellations which enable the infiltration and subsequent running of programme code.
As a reaction McAfee posted an statement to their Avert blog, which tries to negate some of the statements given in the original n.runs Press-release, this represents a short summary of our response to the McAfee Statement on AV Vulnerabilities. For the complete response see: Response to McAfee Statement .
Ryan Permeh (McAfee) wrote: “The ZDNet posting includes scary graphs to frighten users of security products.”
n.runs would like to clarify the statistics those graphs are based on were gathered using an independent database from Secunia and National Vulnerability Database, ZDnet has not produced them. Secunia and the National Vulnerability Database are trusted and respected aggregators of security vulnerabilities and advisories and provided the database to these statistics. Let us emphasize that the intention was not to scare as the statement from McAfee implies, but to put independent facts in addition to those from n.runs on the table. The statistics show a vendor independent view on AV vulnerabilities.
“One of the conclusions drawn by N.Runs is that having AV in your environment makes you less secure than not having it at all.”
n.runs would like to emphasize this is clearly not what n.runs believes. We are convinced that AV software is necessary and a requirement for today’s security defense. What n.runs believes is that multiple engines increase the chance of parsing bugs to occur. Let us show what we mean by using an example based on an Email setup (Detection rates are examples, attack surface in this case is represented by the number of formats supported, # of vulnerabilities per format is an estimate based on our audits).
Reaction to Statement
E-mail is being routed through all three engines, the detection rate increases as does the remotely reachable attack surface.
n.runs firmly believes that the use of AV software or even multiple AV software is a requirement as of today, but that the inherent bugs of AV Software need to be taken into account when designing your perimeter and internal security defense. The rising number of available formats, cryptors, packers combined with the intrinsic market pressure in the AV field (release early, release often) has not helped AV Vendors to increase code quality over the years, as the very same statistics and our experience over the years have clearly indicated (more on this later). We are convinced that AV vendors should focus on doing what AV vendors do best: Recognize malware, aps-AV takes care of the rest.
“In addition, McAfee has not seen any evidence of any of the vulnerabilities reported by N.Runs being exploited to attack our products in real world environments.”
This is due to the fact that n.runs reports these vulnerabilities in order to protect our own and McAfee customers. Our vulnerability notification policy is rigid and strict, advisories included no details as to how the vulnerability was found or how it could be exploited.In our view, the bigger concern are those vulnerabilities not found and published by us, especially as black-market prices for AV-vulnerabilities are on the rise. n.runs is aware of two publicly documented incidents where AV software (running on E-mail servers) was the remote entry vector to internal networks. n.runs also believes that security is a process aimed at being proactive and not solely a process in reaction to events or bugs. Statements such as “McAfee has not seen any evidence” can be deceptive.
For instance, Immunity explained in great detail how they penetrated an Enterprise over AV software on an MTA and used it to covertly shuffle data in and out over weeks. They further explain why they choose AV Software and not a web server or client-side exploits. The attack was done in a similar way to how a professional attacker would proceed. They replicated the existing infrastructure and searched for exploitable conditions and they found one. We do think this backs up our views of the actual threat posed by vulnerabilities in AV software.
The logic that bugs are fixed when they are found is no argument against a professional attacker for the sole reason that these professional and/or military style attackers rarely use known flaws. If the paradigm you follow is — “we protect against what is known” (quite common in the AV industry) then you are doing no favor to those who demand protection against professional attackers.
“Our numbers seemed to have peaked in 2005, which is contrary to the trending that the N.Runs reports.”
n.runs finds it astounding that McAfee comes to this conclusion without taking the vulnerabilities into account that have been reported but where the patch is still pending – and without taking into account the vulnerabilities listed for example on secunia, which are not listed in CVE.
n.runs has the following bugs pending and is aware of at least another DoS bug pending from a independent researcher.
Here is the list of pending McAfee bugs reported by n.runs :
Incident ID: MFE-FW-20060227-01 – Date of receipt: February 27, 2006
Incident ID: MFE-ENG-20070605-01 – Date of receipt: June 5, 2007 (Possible Vuln #15)
Incident ID: MFE-ENG-20070607-01 – Date of receipt: June 7, 2007 (Possible Vuln #18)
Incident ID: MFE-ENG-20070608-01 – Date of receipt: June 7, 2007 (Possible Vuln #23)
Incident ID: MFE-ENG-20070608-02 – Date of receipt: June 7, 2007 (Possible Vuln #25)
Incident ID: MFE-ENG-20070615-01 – Date of receipt: June 15, 2007 (Possible Vuln #27)
Incident ID: MFE-ENG-20070615-02 – Date of receipt: June 15, 2007 (Possible Vuln #28)
Incident ID: MFE-ENG-20071111-01 – Date of receipt: November 11, 2007 (Possible Vuln #36)
Incident ID: MFE-ENG-20071111-02 – Date of receipt: November 11, 2007 (Possible Vuln #37)
Simply adding these pending reports to the graph gives the following result: Statement
n.runs believes this does indeed represent a trend, not to mention these only include problems reported by n.runs, not external researchers or entities nor internal penetration test efforts (which also pose a security threat during the exposure window but are never published).