AV vendors detect on average 19% of malware attacks
Traditional AV vendors continue to lag behind online criminals when it comes to detecting and protecting against new and quickly evolving threats on the Internet, according to a report by Cyveillance.
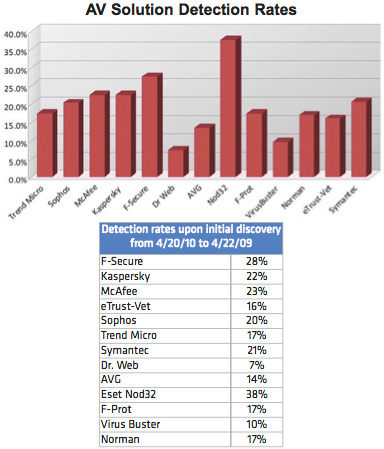
Testing shows that even the most popular AV signature-based solutions detect on average less than 19% of malware threats. That detection rate increases only to 61.7% after 30 days.
“Even after 30 days, many AV vendors cannot detect known attacks, making it critical for enterprises to take a more proactive approach to online security in order to minimize the potential for infection,” said Panos Anastassiadis, COO of Cyveillance.
Cyveillance tested thirteen popular AV solutions to determine their detection rate over a 30 day period and found that popular solutions only detect an average of 18.9% of new malware attacks. By day eight, AV solutions average a 45.7% detection rate. This rises to 56.6% on day 15, 60.3% by day 22, and 61.7% after 30 days.

Top AV solutions take an average of 11.6 days to catch up to new malware. Since this does not include malware signatures undetected even after 30 days, users should not rely on the AV industry as their only line of defense.
All figures and statistics in the Cyveillance report (registration required) are actual measurements rather than projections based upon sample datasets, unless otherwise noted.
The data used for this study were collected and analyzed between April 20, 2010 and April 22, 2010, resulting in an overall total data set of approximately 1,708 confirmed malware files. The files were then run through the latest release of the top desktop AV solutions upon initial detection and again every six hours for one month to determine their detection and lag rates.