Cyber crooks migrate to “ce.ms” free domains
Online scammers and malware peddlers often exhibit locust-like behavior as they migrate from one type of free domains to another in order to evade detection by spam filters and to keep users’ suspicions at bay.
As the recent blacklisting of the .co.cc and the .cz.cc domains by Google has shown, the scammers just begin using others such as .co.tv and, very recently, .ce.ms.
According to Zscaler researchers, a number of .ce.ms are currently hosting exploits that take advantage of a variety of client-side vulnerabilities.
The domain names used are random and contain obfuscated JavaScript code.
“The numbers in the arrays used by the scripts are intentionally spread across separate lines. This way the size of HTML file becomes huge and the total code spans 29K lines,” explain the researchers:
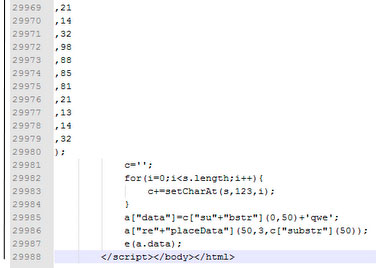
This allows the exploit kit to evade detection by IDS, IPS and antivirus solutions.
Popular free domains will surely continue to be exploited by these malicious individuals. Since Microsoft has yesterday dropped the suit against the Kelihos botnet domain provider, who has agreed to work with the company to create and implement best practices to prevent abuse of free subdomains, let’s hope they will share the knowledge with other providers of free domains.