Industry collaborates on automotive cybersecurity best practices
New technology has paved the way for extraordinary advancements in vehicle safety, emissions reduction, and fuel economy. Today’s vehicles do more to keep drivers secure and connected than ever before. However, connected vehicles must be designed and manufactured with security in mind.
Members of the Automotive Information Sharing and Analysis Center (Auto-ISAC) released an overview of comprehensive Automotive Cybersecurity Best Practices developed as a proactive measure to further enhance vehicle cybersecurity throughout the industry.
More than 50 automotive cybersecurity experts from around the world have participated in the development of these best practices to advance automotive cybersecurity capabilities. The effort began in early 2016 when the 15 automaker members of the Auto-ISAC formed a working group to examine all cybersecurity aspects of the motor vehicle ecosystem.
“While the auto industry shows major efforts to address cyber threats, as shown in the ISAC best practices document, I believe that the most important measure against cyber threats is to automatically harden car controllers according to factory settings. This enables automatic detection and prevention of security bug exploits and blocks attackers from successfully hacking the car,” David Barzilai, Executive Chairman of Karamba Security, told Help Net Security.
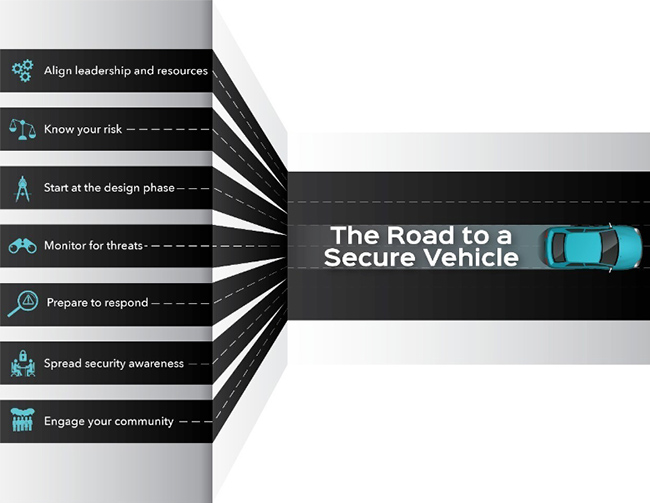
Key topic areas
The best practices provide guidance to assist an organization’s development in seven key topic areas, including:
- Governance: Aligns a vehicle cybersecurity program to an organization’s broader mission and objectives.
- Risk assessment and management: Mitigates the potential impact of cybersecurity vulnerabilities by developing processes for identification, categorization, prioritization, and treatment of cybersecurity risks.
- Security by design: Follows secure design principles in developing a secure vehicle, as well as the integration of cybersecurity features during the product development process.
- Threat detection and protection: Detects threats, vulnerabilities, and incidents to proactively monitor environments and mitigate risk.
- Incident response: Enables automakers to respond to a vehicle cyber incident in a reliable and expeditious manner.
- Awareness and training: Cultivates a culture of cybersecurity and ensures individuals understand their role and responsibility in promoting vehicle cybersecurity.
- Collaboration and engagement with appropriate third parties: Enhances cyber threat awareness and attack response.
The best practices provide deep technical and organizational breadth to support, develop, and improve defenses against potential cybersecurity threats of the motor vehicle ecosystem. They are grounded in ISO, NIST and other established cybersecurity frameworks but are tailored to the motor vehicle. Auto-ISAC members have committed to continuously enhancing them over time to keep pace with the constantly evolving cyber landscape.