How secure are mobile banking apps?
Do banking institutions have a good handle on the things they need to remediate and new control layers they need to adopt to keep users secure?

To answer those questions, Accenture and NowSecure have performed vulnerability assessments of customer-facing mobile banking apps of 15 banking institutions in the North American market.
They have tested the iOS and Android app versions of each of these banks, and found that every app they tested had at least one security issue.
“Of the 465 tests completed for banking apps running on Android, 44 or nine percent had low security issues; 48 or 10 percent had medium security issues; and 10 or two percent had high level security issues. For banking apps running on iOS, a total of 315 tests indicated 24 or eight percent low level security issues; 13 or four percent with medium level issues; and none with high level issues,” they noted.
Security risks
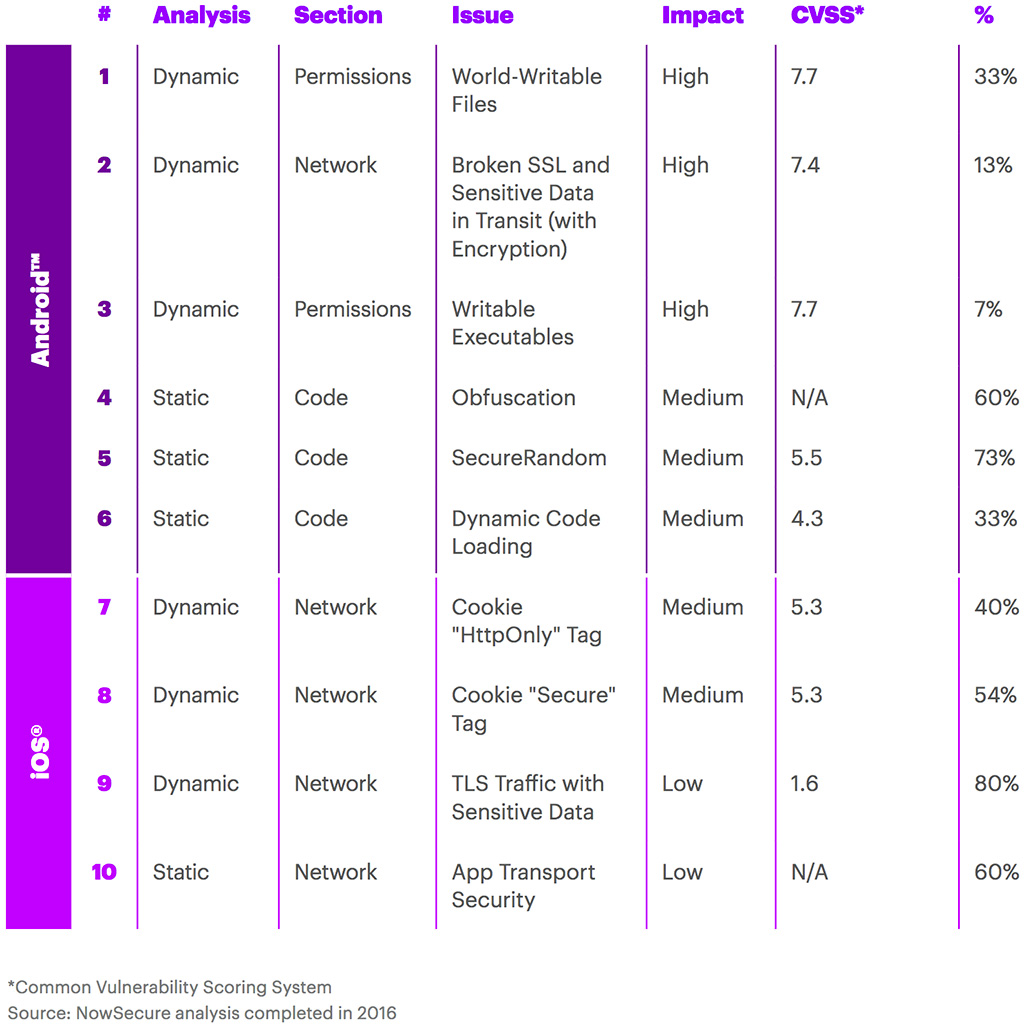
Among the security risks identified were:
- World-writable files (i.e. other apps can have write access to the files)
- Broken SSL check / sensitive data in transit (i.e. unencrypted communications). Curiously enough, none of the tested iOS apps had this problem
- Writable executables – a failing that can be combined with other issues and lead to additional app vulnerabilities, including remote code execution ones.
- Lack of obfuscation of the app source code, allowing for easy reverse-engineering (some 60% of the tested Android banking apps are guilty of this)
- Weak SecureRandom implementation
- Dynamic code loading
- Inappropriately set “HttpOnly” flag (to prevent XSS attacks)
- Inappropriately set “Secure” flag (to prevent the sending of cookies over insecure channels)
- TLS traffic with sensitive data (80% of tested iOS banking apps had sensitive values intercepted while proxying SSL and Transport Layer Security (TLS) app communications (i.e. username, password, GPS coordinates, etc.)
- Lack of app transport security (60% of tested iOS banking apps had ATS globally disabled, which allows a connection regardless of HTTP or HTTPS configuration, connection to servers with lower TLS versions and a connection using cipher suites that do not support forward secrecy).
Based on this and other historical app security assessments, the researchers have concluded that banking institutions have been proactive when it came to remediating well-known critical security issues such as Heartbleed, MITM exposure and others, but less so in regards to the above noted security risks.
Many of the institutions have also introduced multi-factor authentication for online banking (a good step), but chose to leverage SMS technology to deliver authentication codes (inherently insecure choice).
Top security risks identified in vulnerability assessment
Tips for mitigating mobile banking security risks
The researchers have flagged insecure communication as the biggest risk.
Security around the transfer of data across communication channels is a challenge for developers, they noted, pointing out that developers are placing too much confidence in secure end-user behavior and back-end server-side communications.
“Development teams should strive to embed security within the end-to-end mobile SDLC (Systems Development Life Cycle), with proper security governance and oversight supported by recurring developer training and awareness and testing,” the concluded.
“Organizations should also have a strategy for performing regular vulnerability and/or configuration assessments, complemented by penetration testing, app fuzzing, and source code reviews, to obtain a comprehensive understanding of the mobile security environment across the entire mobile deployment stack.”