EternalBlue vulnerability scanner statistics reveal there are exposed hosts worldwide
After the recent massive WannaCry ransomware campaign, Elad Erez, Director of Innovation at Imperva, was shocked at the number of systems that still sported the Microsoft Windows SMB Server vulnerabilities that made the attack possible.
So, he decided to do something about it: he created Eternal Blues, an easy-to-use vulnerability scanner that he made available for download for free.

The tool does one single thing: it scans computers for the aforementioned vulnerabilities, and lets users know which machines on their network are vulnerable to EternalBlue-based attacks.
Unfortunately for those companies hit with the NotPetya wiper/ransomware, the release of the tool came a few days after that particular threat proliferated with the help of the same exploit.
What Eternal Blues usage statistics showed
Still, the statistics collected by the tool, as well as the total number of downloads, show that after the NotPetya attack, people’s awareness of the threat did increase.
“Running Eternal Blues is, by definition, being aware of the problem,” Erez noted.
He shared with Help Net Security the statistics collected from July 1 to July 12, and they tell the following story:
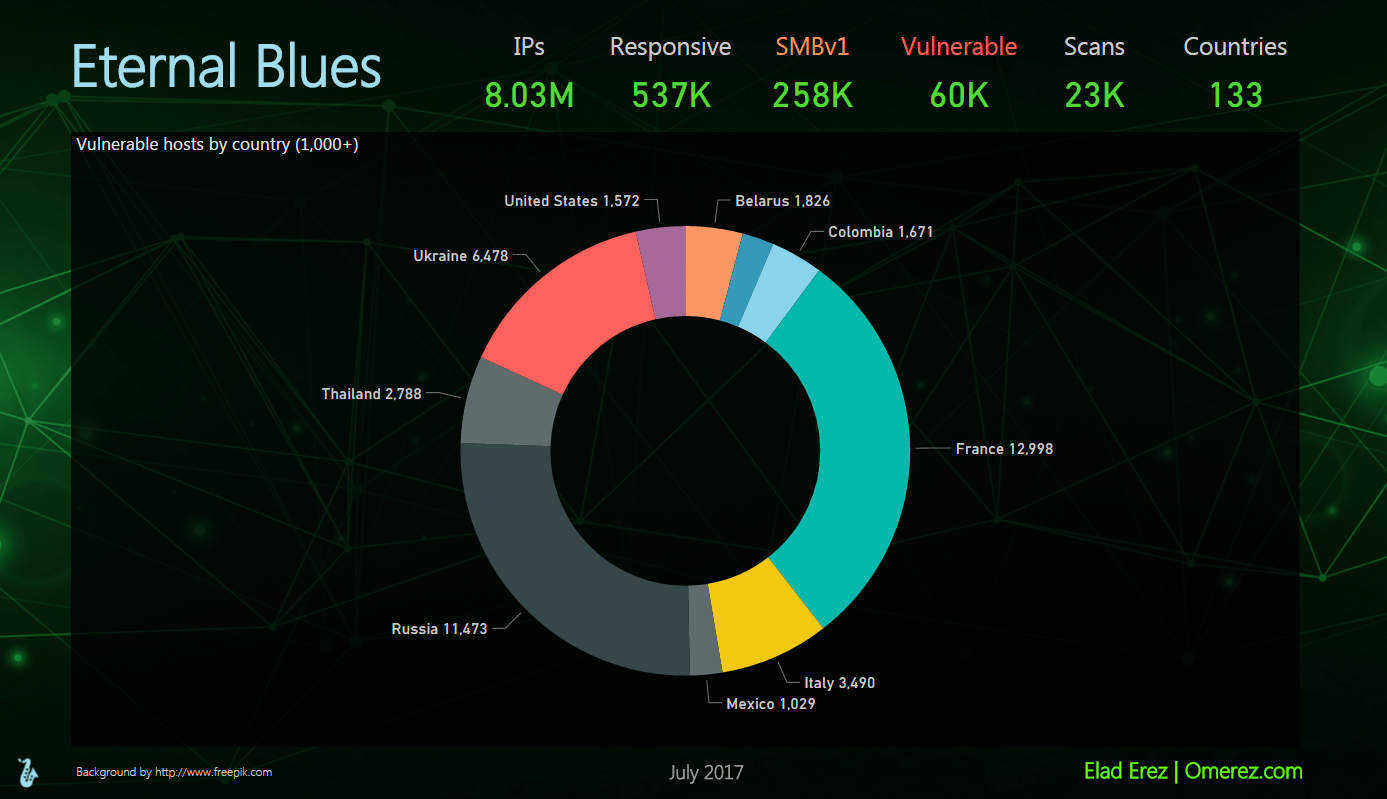
Eternal Blues was used for over 23,000 scans. Over 8 million IP addresses were scanned, and a total of 60,000 vulnerable hosts were identified (out of ~537,000 that were responsive). Of the ~537,000 responsive hosts, some 258,000 still had SMBv1 enabled.
The top 3 vulnerable countries (out of ~130), had nearly 31,000 vulnerable hosts altogether:
But what surprised him the most was the fact that some scans were extremely helpful.
“One organization in France scanned 13,000+ IPs, found ~10,000 responsive hosts (which means this is a large organization), and only 2 hosts were detected as vulnerable to EternalBlue. Without Eternal Blues, finding those two needles in the haystack would have been an almost impossible mission,” he told us.
Here are some more examples of those needles in the haystack:
Mitja Kolsek, CEO at ACROS Security and co-founder of 0patch, also finds those “needles” interesting.
“These are probably not forgotten machines that were just found by the scan, but computers that can’t be updated or reconfigured for some reason. And the fact that they remain in the network means they likely play an important business role – which is an unfortunate InfoSec irony,” he noted.
Practical advice for organizations
Erez advised companies to use the tool, patch vulnerable hosts, disable SMBv1 on all computers, set Windows computers to automatically download and deploy updates, and to periodically assess the risk in their network with their favorite vulnerability scanner.
“The scanner I created checks only for one very specific vulnerability, but just imagine how many potential risks there are out there,” he pointed out.
“Here is a lesson for IT/Security departments: don’t be so certain that you know your network well. Deploy a multi-layered stack of security tools for both risk analysis and real time enforcement.”
He also noted that organizations that haven’t been hit with WannaCry or NotPetya should not be so sure they haven’t been targeted by attackers leveraging the EternalBlue exploit.
He believes that there are many more EternalBlue-based attacks that flew under the radar, and victims are still unaware of having been targeted (e.g. remote code execution was effected for the purpose of data exfltration or making machines part of a botnet).