Creating the security operations center of the future with Siemplify
Security operations teams are engaged in a constant struggle to keep up with the volume of security alerts, maintain the right skills, and manage incident response processes.
They want quality information, presented in a way that makes it easy to grasp and react to quickly. They want not to be bogged down in security alerts, and not to spend precious time searching for information. They want every task that can be automated to be automated. They want to have one central place where they can ingest all the information needed to make decisions that will minimize IT and business risk for their organizations.
In short: they want a technological solution that is built with them in mind.
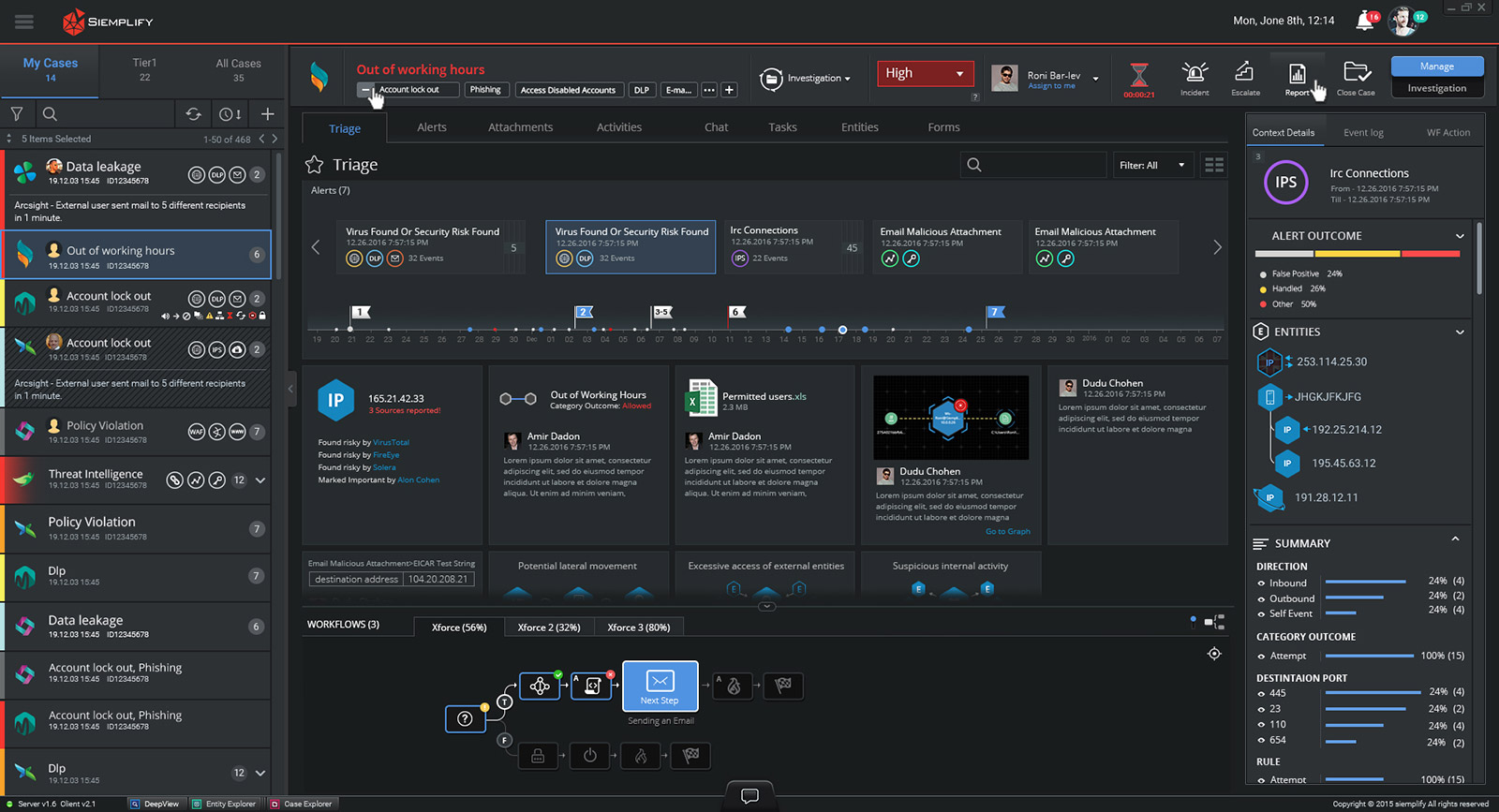
Siemplify ThreatNexus is such a solution, and it’s already being widely used globally by enterprise and MSSP security teams to power their security operations centers (SOCs).
The analyst’s needs and wants
“Time and again we hear analysts rave about ThreatNexus’s ability to raise their game. No longer focused on low-level, mundane tasks and mind-numbing activities, they are able to focus on the value added work they were trained for,” says Amos Stern, co-founder and CEO of Siemplify.
The list of individual processes that can be automated is growing, and effective automation simplifies routine tasks (e.g. creating a connection between different pieces of the puzzle, data gathering, alerts context enrichment). Yet, even the most advanced automation systems filter only a percentage of security alerts that register on a company’s network.
Stern says that, while effective automation is a component of orchestration that addresses both automated machine-driven and analyst-led response, it is important to recognize that automation alone is not the answer.
Still, ThreatNexus’s capability to mix manual and automated activities into a single flow is what makes it stand out. “Most security leaders recognize they are not going to automate away risk. But automation can be leveraged where possible, and empower the analyst where manual investigation is needed,” he notes.
That’s especially important when you known the problems plaguing security operations: too many point solutions and not enough integration; alert fatigue; and a shortage of good analysts. That last problem is also getting worse, and it doesn’t help that getting buried in basic tasks and immense pressure are driving burnout and a high turnover among these professionals.
ThreatNexus reduces alerts by 80% and triples analyst efficiency, and dramatically reduces response time. It does so by providing the ability for analysts to perform their job from a single unified console, which enables them to handle large volumes of alerts and see the big picture in a matter of moments.
Siemplify’s founders’ military intelligence experience helped them create a platform that fuses together the disparate security data in organizations, and a proprietary graph architecture that leverages patented cyber ontology, as well as proprietary machine-learning algorithms, provides the context necessary to understand the full threat “story.”
Finally, ThreatNexus provides total visibility to measure, report and manage every aspect of the security operations center’s activity.
The SOC trifecta
“Building an effective SOC requires organizing internal resources and capabilities in a way that improves communication, increases efficiencies, and provides visibility across the security footprint,” Stern explains.
“Often the starting point is technology and architecture but it is not as simple as that – an effective SOC is predicated on the trifecta of people, process, and technology.”
Organizations need a well-trained team of professionals to operate and drive their SOC. And whether this team is built from in-house resources or by hiring fresh blood, organizations must consider which resources will be needed and must ensure that proper training is put in place to accelerate analysts ramp up and give them the capabilities they need to be effective.
These workers will then need processes, workflows and playbooks to not lose themselves needlessly and to be productive as they can be.
Lastly, they need the proverbial “single pane of glass” that can integrate their security environment, allow them to address the tsunami of alerts, reduce response time, and provide visible (and measurable!) ROI.
“Organizations require a centralized ‘workbench’ for security analysts to drive efficiency: a platform that provides the full scope of threat response to unify people, process, and technology and not just automate selective tasks,” Stern concludes.