How cybercriminals exploited Telegram flaw to deliver malware
A “vulnerability” in Telegram’s desktop instant messaging client for Windows was exploited for months by Russian cybercriminals to deliver malware to users.
Kaspersky Lab researchers discovered in October 2017 that the flaw – which is actually more of a loophole, really – was being actively exploited. They notified Telegram about the issue, and sometime between then and now the loophole was closed by the developers.
“We don’t have exact information about how long and which versions of the Telegram products were affected by the vulnerability. What we do know is that its exploitation in Windows clients began in March 2017,” malware analyst Alexey Firsh shared.
About the loophole
The crooks took advantage of the fact that the Telegram app for Windows accepts and uses a specific character.
“The special nonprinting right-to-left override (RLO) character is used to reverse the order of the characters that come after that character in the string,” Firsh explained.
“In the Unicode character table, it is represented as ‘U+202E’; one area of legitimate use is when typing Arabic text. In an attack, this character can be used to mislead the victim. It is usually used when displaying the name and extension of an executable file: a piece of software vulnerable to this sort of attack will display the filename incompletely or in reverse.”
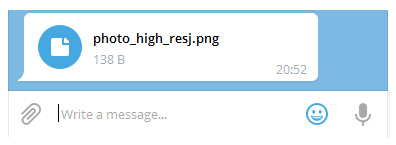
This is just what happened in these attacks: the criminals prepared the malware (a JavaScript file) and gave it a name and icon that is unlikely to raise suspicion with many users (but would not change the nature of the file).
For example: the file name photo_high_re*U+202E*gnp.js would show as photo_high_resj.png.
The attacks
Technically, these were social engineering attacks, as their success hinged of the target running the file despite Windows identifying it as software:

Nevertheless, some were successful, and saddled victims with backdoors (downloaders capable of being controlled remotely) or cryptocurrency mining software (for Monero, Zcash, and Fantomcoin).
To make the illusion complete, the downloaded file would also show a decoy document (a photo).
“It appears that only Russian cybercriminals were aware of this vulnerability, with all the exploitation cases that we detected occurring in Russia. Also, while conducting a detailed research of these attacks we discovered a lot of artifacts that pointed to involvement by Russian cybercriminals,” Firsh shared, but noted that they analyzed only those cases that were reported by Kaspersky Lab’s telemetry systems.
“The full scope and other methods of exploitation remain unknown,” he pointed out.