An introduction to deception technology
This article is first in a five-part series being developed by Dr. Edward Amoroso in conjunction with the deception technology team from Attivo Networks. The article provides an overview of the evolution of deception, including its use in the enterprise, with emphasis on the practical requirements that have emerged in recent years to counter the growing number and nature of malicious threats.
Purpose of deception for cyber
The idea of modern deception in cyber security involves creating a false perception of the attack surface for an adversary. The objective is to cause any malicious activity by that adversary to be adversely affected by the deception thus reducing risk and achieving an improved security posture for the organization. The approach, by design, would work for both human and automated adversaries, and would provide the same benefit of detecting insiders, suppliers, and external threats.
This issue of human versus automated control is equally relevant to both the offensive malicious actor and the defensive team employing the deception. In both cases, the functional goal of enacting a misleading environment to trick the adversary is the same. Both use diversionary measures to redirect normal activity from real assets toward a set of deceptive or fake assets that are put in place for defense. Both cases also address how an organization can significantly improve their overall security posture via deception.

Basic idea of deception in computing
The schema for any deceptive system is straightforward. Benign and malicious users each access a common interface, although schemes do exist where the deceptive interface is hidden from typical employee workflows, which highlights anyone really looking for an entry point. The common interface then includes functionality that redirects access to the deceptive system through use of deceptive lures and decoys. This is a powerful concept that changes the nature of cyber security risk management.
One challenge in any deception-based scheme is that an adversary might be capable, and not easily fooled by a phony entry point, interface, or service. Similarly, an automated attack such as from a botnet will not be swayed by any human or subjective hints or traps that might trick a human. This does not, however, remove the possibility that deception can prevent automated attacks, but rather – it changes the required strategy.
Why deception now?
The evolution of modern enterprise networking has progressed to the point where two conditions make deception an important and urgent control to introduce to a target environment now:
- Inevitability of attacks – Most cyber experts agree that continued emphasis on preventing attacks is essential and must continue; but at the same time, most experts also agree that determined adversaries are more than likely to find their way to your critical assets. As a result, the use of deceptive traps allows for both prevention if detection and action can be initiated quickly, or incident response if the trap picks up evidence that an attack has already begun.
- Context-awareness of attacks – Modern cyber attacks are aware of their contextual environment and use indictors in a target system to make dynamic decisions about attack strategy. This was always true for human attackers, but is now also true for automated attacks. For this reason, it is imperative to use deception to adjust this contextual equation in favor of the defense.
Many enterprise teams have been considering use of deception for years, but these factors of inevitability and context will hopefully convince security teams that this time is right now for an effective deployment of deception to the enterprise.
Using deception against adversaries
Deception has a rich history in the battle against malicious adversaries in conflict situations. Military teams have long known, for example, the great advantages of using deceptive means for dealing with their enemies. Specific types of advantages that traditional emerge when deception is used by defenders to prevent attacks or respond to existing conflict can be listed as follows:
- High value to cost ratio – The cost of using deception in any adversarial situation is generally low, as compared with the cost of introducing more active functional controls into live systems. A non-computing example from the Second World War is the use of mocked up military vehicles and equipment, including inflatable tanks, which looked like an entire army to aerial reconnaissance, tricking the enemy about both the objective of an upcoming attack and the strength involved. Obviously, inflatable tanks were much less expensive than real ones.
- Supports strategic analysis – Any deceptive sting operation provides the opportunity for analysts to observe, review, interact with, and learn from an active offensive actor. The insights gained allow for safe engagement with an adversary under controlled conditions that prevent live assets from being destroyed or compromised.
- Ease of deployment and use – For most applications, the deployment of deception is relatively simple – perhaps for the same reason that building a Hollywood façade row of buildings is easier than building an actual city. Clearly, the amount of work that goes into deployment will be directly related to the authenticity and believability of the deceptive trap and content.
For these reasons, applying deception to computing is a natural progression of modern cyber risk management. In fact, one might view the introduction of deceptive technology, as exemplified by the Attivo Networks solution offerings, as one of the more impressive and exciting aspects of the cyber security industry. I am encouraged to see the company’s current momentum and the traction they are achieving with critical infrastructure applications and medical IOT device threat detection.
Honey pot methods
The earliest deceptive techniques were designed around cleverly-designed content repositories called honey pots. The idea of a honey pot is that by placing specially crafted information, services, data, or other resources considered attractive to an adversary, the associated deceptive system would be successful in establishing persistence of that actor with the trap. It’s the tech equivalent of placing peanut butter on a mouse trap.
The original conception of honey in a deceptive system often involved a human defender interacting in real-time with a human attacker. The resulting back-and-forth would follow a human-time cadence where the strategy would unfold like in a chess match. Bill Cheswick wrote back in the 1990’s of his experiences at Bell Labs trapping a live hacker by using crafted and enticing information provided specifically for such purpose. He wrote this:
“On 7 January 1991, a cracker, believing he had discovered the famous sendmail DEBUG hole in our Internet gateway machine, attempted to obtain a copy of our password file. I sent him one. [1]”
The manual creation of a honey pot requires great skill and insight on the part of the defensive team. They must understand the interest tendencies of a human actor as well as the functional tendencies of an automated one. This requires that the process for creating, maintaining, and supporting a honey pot must follow a well-developed lifecycle process to ensure that meaningful and effective deceptive content is in place. (Luckily, commercial platforms such as from Attivo Networks ease this task considerably by introducing practical deceptive traps that are less dependent on manual creation of honey pot content.)

Traditional honey pot lifecycle
The lifecycle for honey pot content starts with researching the attributes of an adversary. This can include human tendencies for honey pots designed to entice a person or group to some deceptive content. The second step involves creation of the honey content, in a manner consistent with the consumption model of the target. If a botnet is being targeted by the honey pot, then the content must be consistent with what a botnet might be programmed to find.
The third step involves realistically deploying the honey pot in a manner that will not offer clear evidence to the adversary of the deception. Working with a competent vendor such as Attivo Network will help you assess whether this type of approach can work in your environment. Finally, the lifecycle continues with monitoring of the honey pot usage to influence adjustments or to round out the research understanding of what works to entice the target.
The primary requirement for a honey pot is that it must establish persistence of a potential adversary to a deceptive system. Common examples include files of interest (such as the password file provided by Cheswick to his cracker), bogus machines, links to bogus systems, and even fake networks or documents. This must work for both humans expressing interest, as well as automated attacks that are programmed to seek specific types of content.
It’s important to recognize that legal considerations exist in most countries to protect innocent citizens and groups from being lured by an overly aggressive defender. Most vendors such as Attivo Networks provide solutions that are well-within the boundaries of reasonable network controls in every conceivable setting. Furthermore, once an adversary is already inside an enterprise, it is generally considered fine to employ means to protect assets.
Basic schema for deception in computing
The basic high-level architecture for deception in a typical enterprise or network includes several components. First, there are the deceptive traps placed strategically into a target system of interest. Second, these traps require a secure communication path to a deception collection and analysis system. And finally, set-up, support, and content require an administration system for day-to-day support. Native integration of the deception into the target environment simplifies all of these tasks considerably.
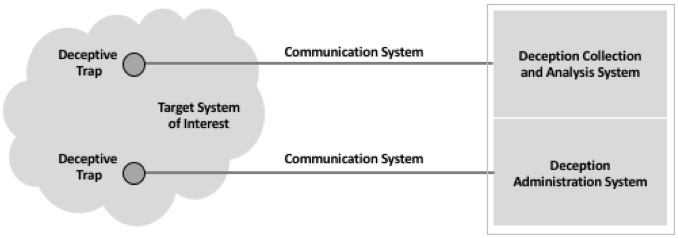
Basic deception schema
Obviously, this deception schema is high-level and is intended to provide a basic, notional view of how most enterprise networks would deploy a commercial deception tool. Security technology companies such as Attivo Networks continue to refine their offerings to ensure optimal integration into the evolving enterprise – which everyone can agree is moving toward more extensive use of public cloud and mobile networks.
In addition, it is worth mentioning that deception solutions were rarely integrated into production designs. Instead, in the early days of cyber security, target systems were in operation before deception was added to the defensive architecture. As such, most modern deception deployments, including commercial solutions from Attivo Networks, will usually involve an architectural overlay onto existing networks, systems, applications, and databases.
Good news is that machine learning and related advanced heuristics are beginning to simplify this process considerably. Present and future deployments of deception will increasingly rely on such heuristic processing to automate the generation, deployment, and on-going operations of deception campaigns and their authenticity.