G Suite admins get context-aware access controls, rule-based automated actions and alerts
Google is rolling out new security capabilities for G Suite Enterprise administrators, allowing them to implement context-aware access controls for users and to create rules to automate actions and alerts through the security center.
The company is also providing new security management controls for all G Suite editions, allowing admis to get a clearer picture of all the devices that are accessing corporate data, see whether they should be more secure, sign out users if their device is compromised, etc.
Context-aware access controls
Context-aware access gives administrators control over which G Suite apps a user can access based on their context, such as whether their device complies with the organization’s IT policy.
Admins can set up different access levels based on a user’s identity, organizational unit, location, device security status, or IP address.
For example, they can make it so that only users from a corporate-owned device and a corporate IP address or only those whose desktop device storage is encrypted can access the organization’s Google Drive. Or they can allow access to apps from outside the corporate network only for users from a certain organizational unit (e.g., executives), only from company-issued devices, and only if the device is protected with a password. Or they can allow access to apps only for those users who have the latest OS security updates.
When access is disallowed, users will see a message that should tell them who to contact to get access (the message can be customized).
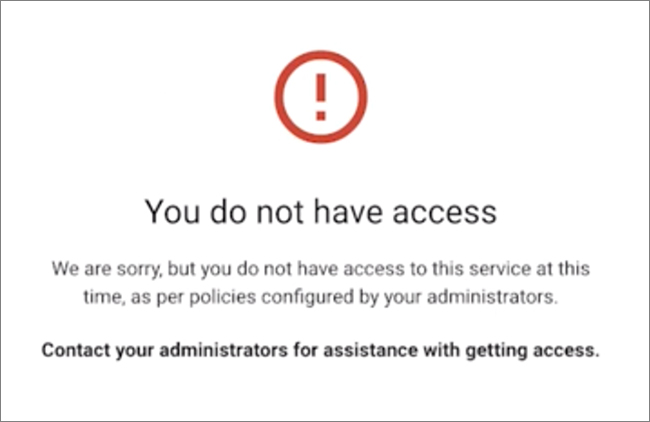
This feature will be available to G Suite Enterprise, G Suite Enterprise for Education, and Cloud Identity Premium customers, and is off by default.
Automated actions and alerts
The option of automating actions and alerts through the security center allows admins and analysts to automate security management tasks and improve their organization’s security posture.
“This makes it possible for teams of admins and analysts to collaborate on security investigations instantly based on alerts, and makes it easier to assess and manage threats with automated actions and improved tracking—key steps to improve your organization’s security posture,” Google Cloud product managers Vidya Nagarajan and Brad Meador pointed out.
Admins can create reporting and activity rules, configure them to create alerts or perform remediation actions, and put them into monitor mode to test them prior to implementation. Log entires allow security analysts to see why specific rules got triggered and what action they performed.

Alerts can be triggered by suspicious device activity, user-reported phishing, suspicious logins, data exfiltration activity, etc.
This feature will be available to G Suite Enterprise, G Suite Enterprise for Education, and Cloud Identity Premium customers, and is on by default.