Modern malware is increasingly leveraging evasive behaviors
Modern malware is increasingly leveraging evasive behaviors, a new report by VMware Carbon Black released at RSA Conference 2020 has revealed. The report uncovers the top attack tactics, techniques, and procedures (TTPs) seen over the last year and provides specific guidance on ransomware, commodity malware, wipers, access mining and destructive attacks.
Among some of the key findings from the report:
- Defense evasion behavior was seen in more than 90 percent of the 2,000 samples they analyzed
- Ransomware has seen a significant resurgence over the past year. Defense evasion behaviors continue to play a key role with ransomware (95 percent of analyzed samples).
- The top industries targeted by ransomware over the past year have been: Energy and Utilities, Government and Manufacturing, suggesting that ransomware’s resurgence has been a nefarious byproduct of geopolitical tension.
- Ransomware’s evolution has led to more sophisticated Command and Control (C2) mechanisms and infrastructure for attackers. Cyber criminals continue to leverage standard application protocols in network deployments to operate under the radar and blend in with standard business traffic. They are also deploying secondary C2 methods on sleep cycles, allowing them to wake up a new method of C2 upon discovery or prevention of their primary method.
- Wipers continue to trend upward as adversaries (including Iran) began to realize the utility of purely destructive attacks. Leveraging techniques across the full spectrum of MITRE ATT&CK, wipers rely heavily upon Defense Evasion techniques to avoid detection (64 percent of analyzed samples).
- Classic malware families have spawned the next generation. Throughout our research, we analyzed malware (such as NotPetya) that initially appeared to be ransomware, but upon further inspection, found the decryption component removed or ineffective, resulting in purely destructive malware.
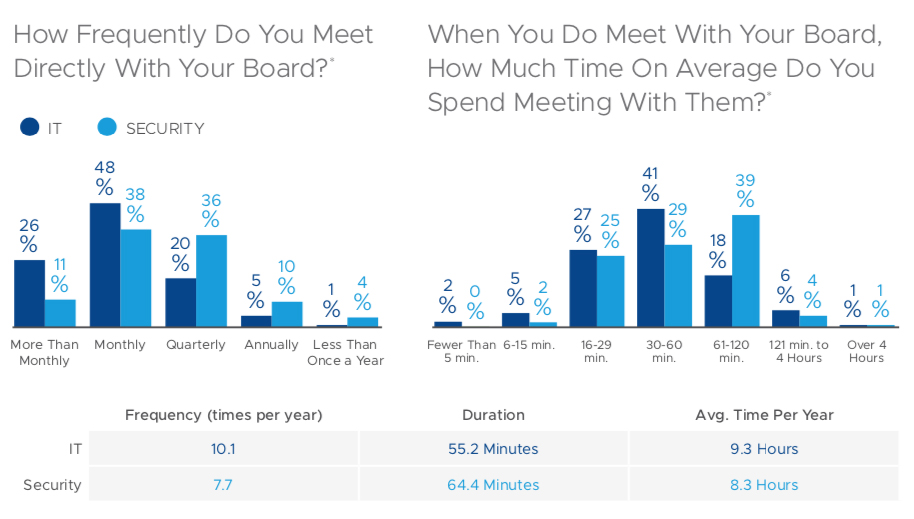
VMware Carbon Black also collaborated with Forrester Consulting on a 624-person survey (IT / security manager and above, including CIOs and CISOs) to explore the current state of IT and security relationship dynamics from the C-level to the practitioner level, and how these will evolve.
Key highlights of the survey include:
- IT and security teams appear to be aligned on goals (preventing breaches, efficiency, incident resolution) but 77.4 percent of survey respondents said IT and security currently have a negative relationship, according to our study conducted with Forrester Consulting.
- 55 percent of survey respondents said driving collaboration across IT and security teams should be the organization’s top priority over the next 12 months, according to the study.
- Nearly 50 percent of both IT and security respondents reported being understaffed with security respondents noting their teams are currently 48 percent understaffed and IT teams are 26 percent understaffed.
- The study found that, in the majority of cases (45 percent) the CISO is reporting to the CIO. However, when asked who should the CISO report to, most respondents (37 percent) said directly to the CEO. Of note, nearly half (46%) of CIOs said the CISO should report directly to the CEO.
- The talent gap continues to be a theme across the IT and security landscape. According to the study, 79 percent of respondents said finding the right security talent is either “very challenging” or “extremely challenging” and 70 percent reported the same level of challenge for IT talent.
- More than 50 percent of survey respondents said that both security and IT will share responsibility for key areas like endpoint security, security architecture and identity/access management over the next three to five years.
- When it comes to risk, security leaders said brand protection (81 percent of respondents) is the most important issue for company boards.
- Both security and IT have seen increased investments over the last year. Among survey respondents, 77 percent said they purchased new security products, 69 percent reported an increase in security staff and 56 percent reported an increase in IT staff.
“Defenders must stop thinking about how to achieve results on their own. Defenders must continue to build bridges with IT teams. The time for cooperation is now. We can no longer afford to go at this problem alone. We need IT teams to look toward security solutions that are built in and not bolted on. It’s time for security to become part of our organizational DNA. It’s time security becomes intrinsic to how we build, deploy and maintain technology,” said Rick McElroy, one of the report’s authors.