Hackers are targeting the COVID-19 vaccine supply chain
Unknown hackers have been trying to compromise accounts and computer systems of employees in organizations involved in the COVID-19 vaccine supply chain.
While it’s obvious that their spear-phishing emails are aimed at harvesting login credentials, their final goal is likely to get their hand on as much information as possible. Also, according to IBM Security X-Force researchers, it’s unclear whether their attempts have been successful.
The phishing campaing
The phishing campaing in question started in September 2020.
The targets? Select executives in sales, procurement, information technology and finance positions at organizations around the world associated with Gavi, The Vaccine Alliance’s Cold Chain Equipment Optimization Platform (CCEOP) program.
More precisely, the hackers targeted organizations associated with the COVID-19 cold chain – a component of the vaccine supply chain that preserves vaccines in temperature-controlled environments as they are transported and stored:
- The European Commission’s Directorate-General for Taxation and Customs Union
- Companies involved in manufacturing solar panels (for vaccine refrigerators)
- Companies associated with petrochemicals (dry ice is a byproduct of petroleum production)
- A software development firm and a website development company that has clients in pharmaceutical manufacturing, container transport, biotechnology, etc.
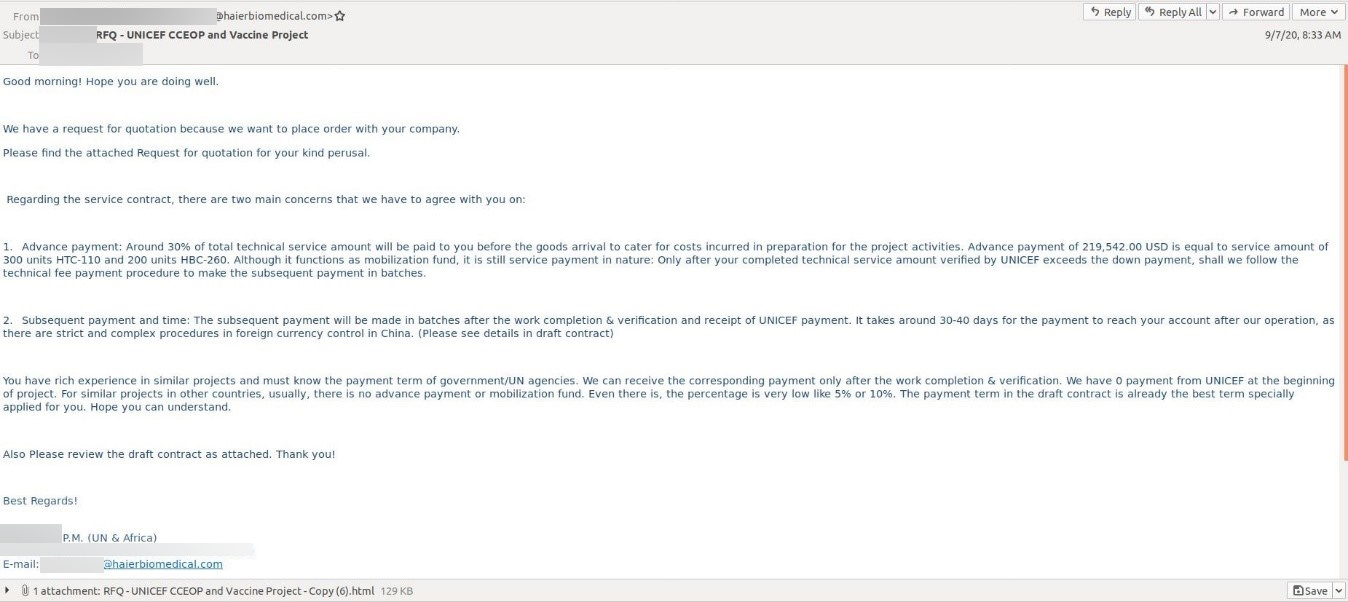
The phishing emails were made to look like requests for quotations related to the CCEOP program and like they had been sent from a business executive from Haier Biomedical, a Chinese company that’s a legitimate, qualified supplier for the program:
They carried malicious HTML attachments that would open locally and prompt recipients to enter their credentials to view the file.
“We assess that the purpose of this campaign may have been to harvest credentials to gain future unauthorized access. From there, the adversary could gain insight into internal communications, as well as the process, methods and plans to distribute a COVID-19 vaccine,” the researchers noted.
Who’s behind it?
Cyber attackers have been exploiting COVID-19 as a lure for various fraudulent schemes and phishing attemtps since the very beginning of the pandemic.
Earlier this year, the US and UK government agencies have warned about Chinese hackers targeting research facilities working on the COVID-19 research and response. On Wednesday, Interpol warned the public about “potential criminal activity in relation to the falsification, theft and illegal advertising of COVID-19 and flu vaccines.”
This latest campaign – its precision targeting and the nature of the targeted organizations – potentially points to nation-state backed hackers.
“Without a clear path to a cash-out, cyber criminals are unlikely to devote the time and resources required to execute such a calculated operation with so many interlinked and globally distributed targets. Likewise, insight into the transport of a vaccine may present a hot black-market commodity, however, advanced insight into the purchase and movement of a vaccine that can impact life and the global economy is likely a high-value and high-priority nation-state target,” the researchers opined.
Chris Ross, SVP Sales, International, for Barracuda Networks posited that the attackers could be trying to acquire leverage in a multi-million pound ransomware attempt, to sell stolen data on the “black market” to the highest international bidder, or even disrupt the UK’s standing as the first country in the world to start vaccinating its citizens on a mass scale.
“This is the first time that a significant phishing campaign has been used on a global scale to disrupt the progress of our battle with the coronavirus – this issue must be taken extremely seriously by all afflicted targets and organizations who have anything to do with the logistics, transport or distribution of the vaccine, who may have already been breached, and do not yet know it,” he added.
“Implementing an immediate and comprehensive security training session combined with a rigorous refresh of company and employee passwords and usernames must be undertaken immediately in an attempt to flush out and block any existing or future attacks. Backing up key data via a sophisticated third-party cloud backup provider is also essential in protecting organizations from any future ransomware attack attempts.”
IBM Security researchers also advised defenders conduct regular email security educational trainings, as well as to create and test incident response plans, share and ingest threat intelligence, assess their third-party ecosystem, apply a zero-trust approach to their security strategy, use MFA across their organizations, and use Endpoint Protection and Response tools.