Getting ahead of a major blind spot for CISOs: Third-party risk
For many CISOs and security leaders, it was not long ago that their remit focused on the networks and digital ecosystems for their organization alone.
In today’s digital world, those days are a thing of the past with a growing number of businesses relying on third-party vendors to scale, save time and outsource expertise in order to stay ahead. With this change, new security risks affiliated with third-party vendors are more prevalent than ever before.
Supply-chain attacks like SolarWinds making headlines and causing domino effects to organizations involved have made third-party security risk a topic that’s present in boardrooms and SOCs alike. In fact, supply-chain attacks were reported as one of the top concerns of U.S. CISOs in 2021.
“While third-party risk is not necessarily new, it is something that is often a blind spot as it’s often not seen as a direct responsibility of CISOs and security teams,” said Gene Yoo, CEO of Resecurity, Inc and former security executive at a major U.S. financial institution. “This blind spot is typically created when there’s a lack of visibility into the actual state of the cybersecurity posture and security team of the third-party vendor. However, when an incident does occur, that is when it quickly becomes an issue as the organization itself will take the blame for the breach.”
Today, organizations, government and the cybersecurity industry are taking this supply-chain challenge head-on to make this blind spot a bit clearer. From ‘trust but verify’ approaches to ensure better security posture from third-party vendors to implementing more rigorous DevSecOps protocols to ensure security is top of mind from end to end, both organizations and the industry are establishing new standards for their third-party vendors.
But where does that leave CISOs and organizations while this transformation takes place?
The lowest hanging fruit is implementing Third-Party Risk Management solutions that can identify the network, identity, technology and geographical risks, said Yoo.
“It’s essential for organizations to have a good understanding of where their third-party risk stands today to protect themselves and those in their ecosystem (customers, vendors, partners, etc.),” said Yoo. “Having insights across today’s landscape, organizations can make better decisions about which third-party vendors to trust.”
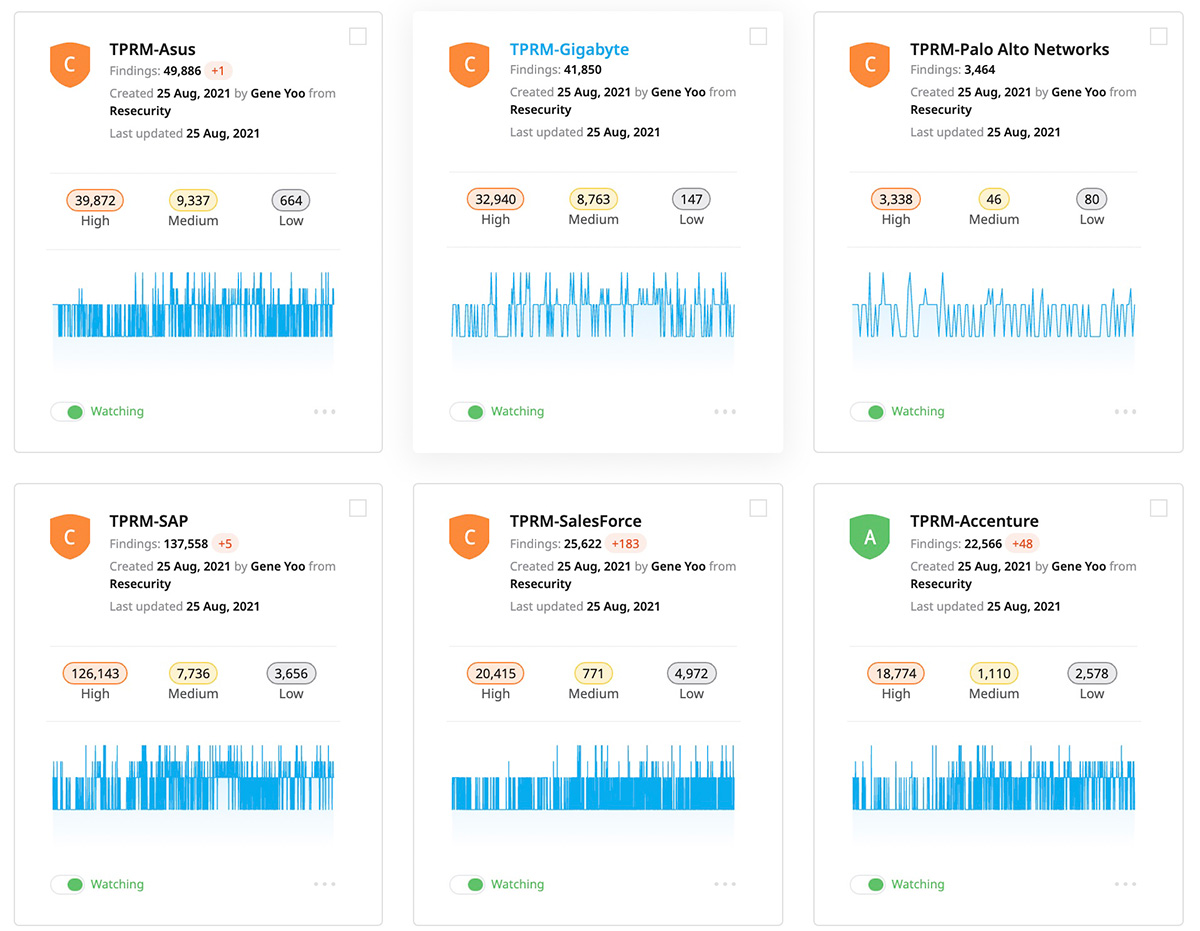
Third-party risk management – Cyber Risk Spider Graph generated by Resecurity
Continuous security monitoring of multiple elements of enterprise supply chain
Third-party Risk Management solutions (TPRM) like Resecurity’s Risk platform allows organizations to tap into actionable, external threat intelligence such as recent data leaks, breached accounts, misconfigured services and infections.
Dark Web exposure
Understanding when and if an organization has been targeted in the past by cyber attackers is essential when evaluating third-party risk. Third-party risk management solutions can offer an inside look on the dark side of the web, providing insight into if the hackers were targeting the third-party vendor in the past, or if such activity has been identified recently and may require consideration.
Threats originating from the Dark Web are the most unpredictable as they are driven by particular actors and groups leveraging previously seen or never seen TTPs, making it complicated for CISOs and threat intelligence teams to react without proper visibility and context.
Dark Web actors have a strong interest in the supply chain of enterprises and government organizations, particularly technology companies, cloud providers, hardware manufacturers, semiconductors developers and engineering vendors. In certain cases, threat actors may also be focused on the human element including IT staffing, accounting firms and contractors whom they can target or recruit to leverage as an insider. Analysis of the recent ransomware activity shows major cybercriminal groups and their affiliates actively attempt to infiltrate employees from the private sector to embed malicious code or to steal sensitive data which may provide them more privileged access to the victim’s IT infrastructure.
Network hygiene
Many of the recent supply-chain attacks making headlines were a result of organizations not having a strong understanding of their third-party vendor’s security and network hygiene. Using TPRM, organizations can complete a comprehensive digital risk assessment of the third-party vendor by performing more than 20 unique quality checks related to network hygiene of the enterprise including analysis of exposed identities in the Dark Web, breached accounts, infected endpoints and historical indicators of compromise (IOCs).
One of the key focuses is uncovering possible infection by malicious implants and tools that can lead to data exfiltration of covert channels, allowing a remote attacker to connect to the victim’s environment and perform network intrusion. For example, the activity of malware such as Agent Tesla, Azorult, Racoon Stealer, Pony Loader and Trickbot are dominating in email traffic in 2021. These threat actors use e-mail and malicious attachments as one of their key delivery methods, using increasingly advanced techniques to obfuscate and design the content to increase the chances the employee will execute it. Attackers often design malicious content as an element of the supply chain in hopes that will not draw the target’s attention. An being a document that appears to be a Docusign notification for further review before e-signing, a typical supplier fax or a secure email protected by Information Rights Management (IRM) available in Office 365.
As the industry has seen firsthand, even mature and well-established enterprise security teams have a lack of visibility into network hygiene of their branches, offices and contractors abroad due to varying security policies and protocols, management hierarchy and known pain points in franchised-based businesses. The same is applicable to their supply chain, where the level of network hygiene is typically a “black box” or something the third-party is simply not willing to discuss.
Acquisition of the quantitative, historical and the most recent indicators of compromise is a vital component of TPRM, providing enterprise organizations actionable information to determine if a counterpart may be compromised with malware and what service may be potentially breached by it. This knowledge enables CISOs to make strategic and tactical decisions, as well as to communicate with other teams, including those responsible for vendor management and supply chain and the organization’s legal team. In particular, legal teams may facilitate building a proper supply chain risk policy to require vendors to share and report possible cybersecurity incidents or threats that may have a negative impact on the operations of your enterprise. With these types of policies in place, vendors who are not able to maintain proper cybersecurity posture may be excluded from doing business with your organization in order to reduce security risks.
Identity health check
Similar to how companies run background checks on their potential employees, identity health checks for third-party vendors who have access to an organization’s networks and data can go a long way. By enumerating user identities of third-party, TPRM can establish an initial understanding of how trustworthy an organization is, the size of their footprint, or if the users have been previously or recently hacked — a vital piece of intel that can warn CISOs to prevent further communications with them via e-mail.
Technology risk
Similarly to using identity health checks to ensure user security hygiene, it’s essential to understand the risks of the technology stack third-party vendors are using themselves. Resecurity’s Risk platform analyzes the third-party’s technology stack based on in-depth analysis of external digital footprint, as well as network reconnaissance and infrastructure assessment. Using AI and proprietary risk-scoring models, the platform analyzes how secure their products are, if particular software components have a negative history of patches or certain vulnerability trends and if the software is based on open-source libraries or components with closed source code — all of which can make it impossible to research their security independently.
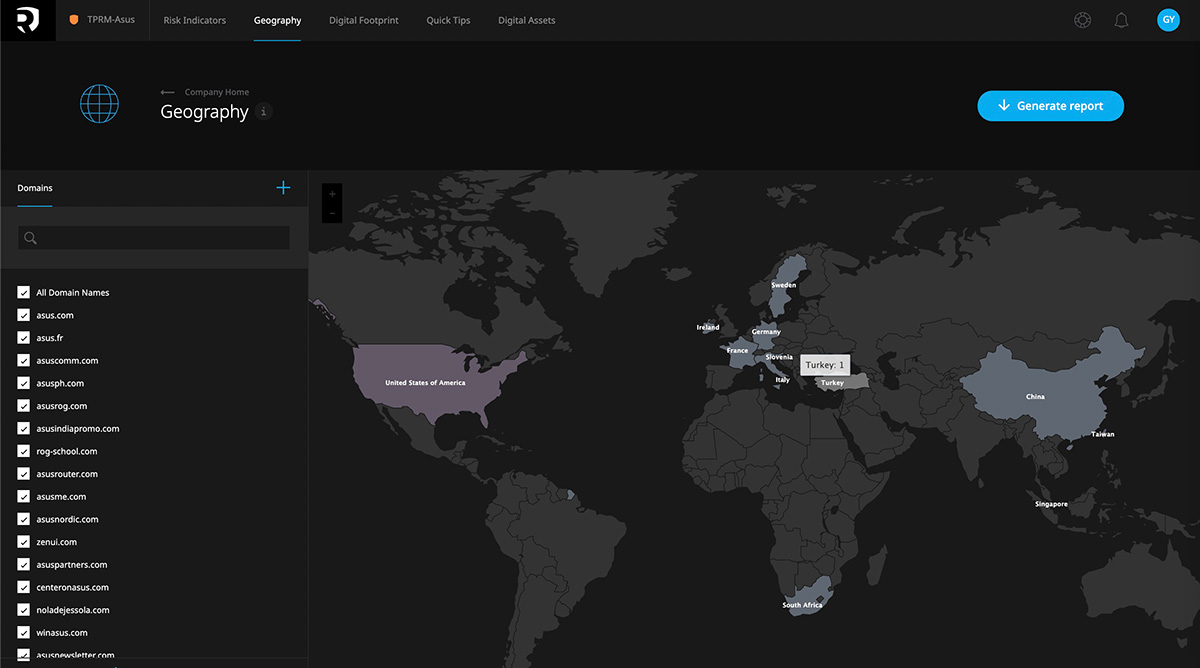
Geographical risk
When understanding geographical risk, it’s critical to identify and analyze the origin of development and the IT infrastructure location for both the vendor and the technologies they use. Due to recent geopolitical dynamics, it is important to be aware of third-parties having infrastructure or presence in hostile states or foreign countries that pose a significant risk to the U.S. national security. While the source may appear obvious, it can often be deceiving due to the vendor may use multiple companies created to blur the origin of where a particular IT solution has been developed or where the staff is actually located. Foreign intelligence and advanced cybercriminal groups are actively trying to infiltrate into the supply chain of U.S. enterprises to steal sensitive data. With the growing remote workforce and global digitization, this risk is greater than ever.
Actors from OFAC-listed countries and other high-risk states targeting the U.S. economy are constantly trying to bypass sanctions and develop alternative channels to penetrate into domestic and foreign markets by creating synthetic marketplaces, misinformation, modifying existing technologies and targeting various software and hardware providers as well as organizations acting as resellers or IT integrators. TPRM includes actionable threat intelligence to keep enterprise security leaders informed to mitigate possible risks.
While today’s cyber threat landscape continues to grow, solutions like TPRM are making it more accessible than ever for CISOs and security leaders to have the security and peace of mind they need when working with third-party vendors.
Implementation of TPRM is a fundamental component of modern cybersecurity management aimed to increase visibility into third-party risks and to protect enterprise supply-chain from malicious activity.
Click here to learn more about Resecurity’s Risk TPRM platform.