Apple fixes security feature bypass in macOS (CVE-2021-30892)
Apple has delivered a barrage of security updates for most of its devices this week, and among the vulnerabilities fixed are CVE-2021-30892, a System Integrity Protection (SIP) bypass in macOS, and CVE-2021-30883, an iOS flaw that’s actively exploited by attackers.
Source: Microsoft
About CVE-2021-30883
CVE-2021-30883, a memory corruption issue in IOMobileFrameBuffer, was patched by the company in iOS and iPadOS v15.0.2 earlier this month, when Apple said that it was “aware of a report that this issue may have been actively exploited,” and ZecOPs researchers confirmed that it’s “accessible from the browser” and “perfect for 1-click & water-holing mobile attacks”.
A security researcher who analyzed the patch created a POC that worked on iOS 15.0 and iOS 14.7.1, and said it would probably work on earlier versions of the OS.
Two weeks later, the fix has finally been included in iOS and iPadOS 14.8.1, tvOS 15.1, and watchOS 8.1.
We still don’t know the nature of the attacks in which the vulnerability has been or is still being exploited.
About CVE-2021-30892 (aka “Shrootless”)
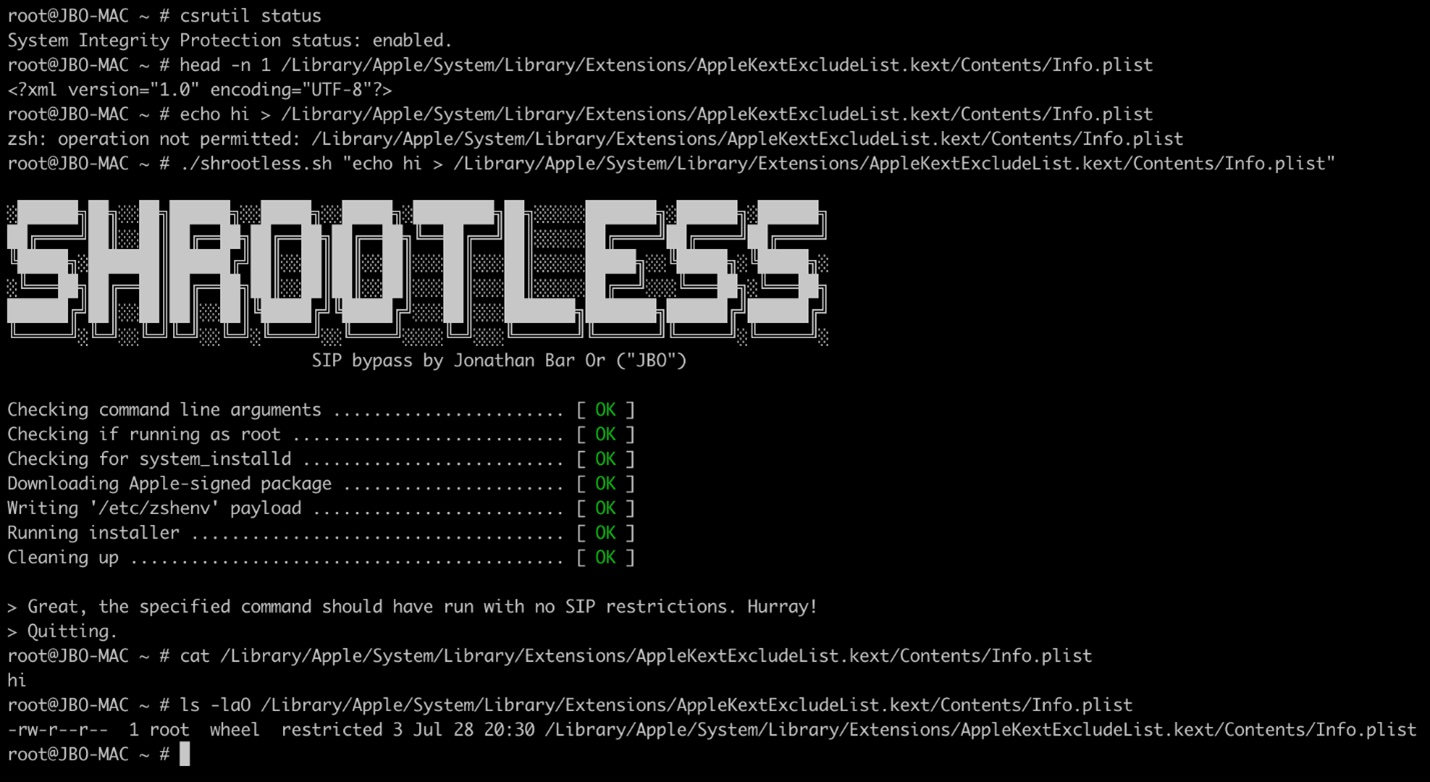
CVE-2021-30892 was unearthed and reported by Jonathan Bar Or, a security researcher with the Microsoft 365 Defender Research Team.
It is a vulnerability that may allow attackers to bypass the macOS System Integrity Protection (SIP) feature by creating a specially crafted file that would hijack the installation process. This would allow them to install rootkits, other malware, overwrite system files, and more.
“SIP is a security technology in macOS that restricts a root user from performing operations that may compromise system integrity. While assessing macOS processes entitled to bypass SIP protections, we came across the daemon system_installd, which has the powerful com.apple.rootless.install.inheritable entitlement. With this entitlement, any child process of system_installd would be able to bypass SIP filesystem restrictions altogether,” the team explained.
They found that by invoking the operating system’s default shell (zsh) via post-install scripts in an Apple-signed package and changing the /etc/zshenv file zsh uses to run commands, they can deliver the malicious payload and install it.
To prove the vulnerability’s exploitability, they created a POC that overrode the kernel extension exclusion list.
In addition to this, they found that zshenv can also be used to achieve persistence and to elevate user privileges to root.
CVE-2021-30892 has been fixed in macOS Monterey 12.0.1, macOS Big Sur 11.6.1, and Security Update 2021-007 for macOS Catalina.