Phishers go after business email credentials by impersonating U.S. DOL
Phishers are trying to harvest credentials for Office 365 or other business email accounts by impersonating the U.S. Department of Labor (DOL), Inky‘s researchers have warned.
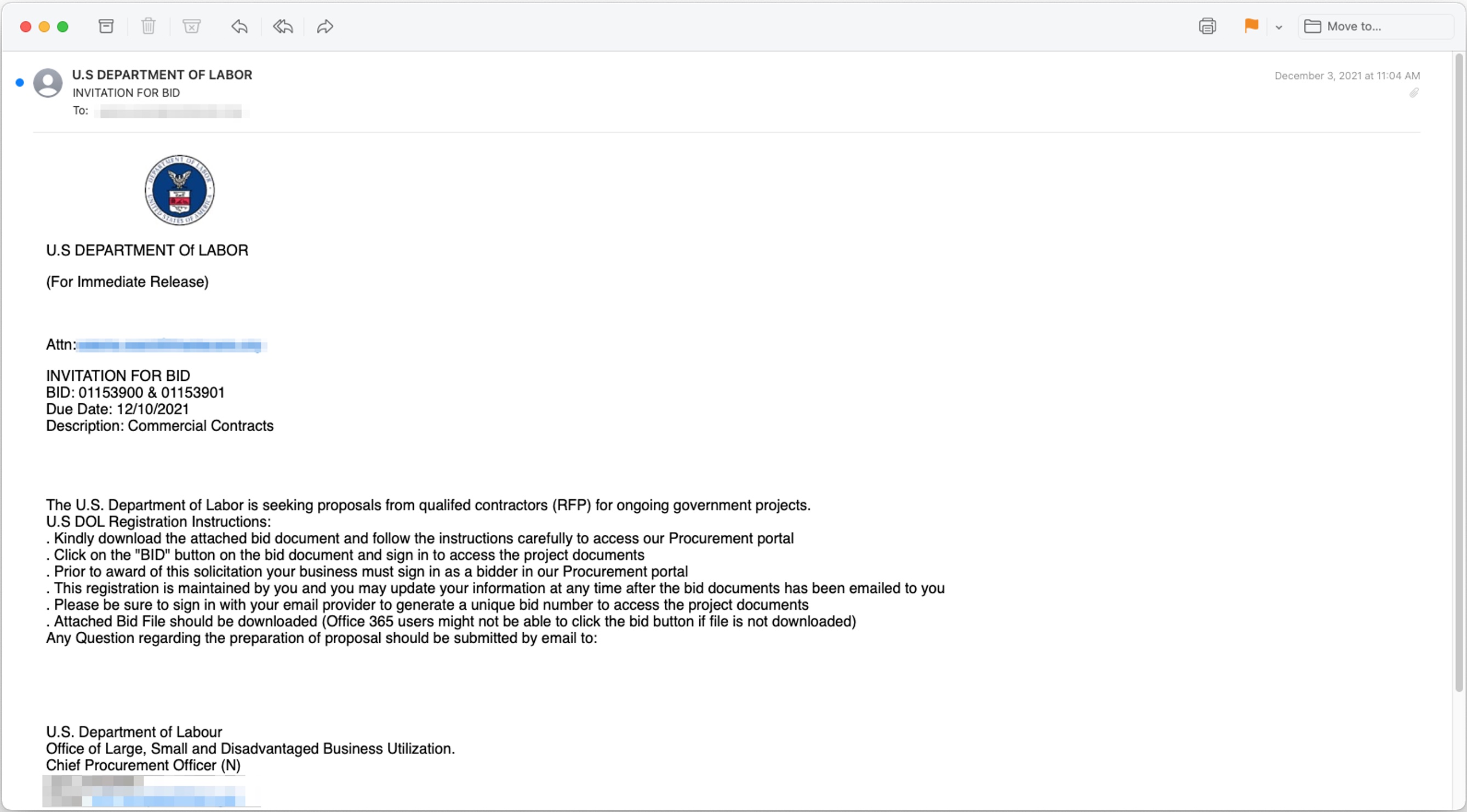
The ploy? The DOL is ostensibly inviting companies to submit “proposals from qualified contractors for ongoing government projects”, and helpfully explaining the various steps of the process:
By clicking on the “BID” button in the PDF, potential victims are taken to a fake DOL procurement portal that is an identical copy of the real DOL website.
Finally, when clicking on the “Click here to bid” button, they are asked to sign in with a business email account:
Tricks used by the phishers to grab business email credentials
This phishing scheme is very clever:
- The email, PDF and the phishing page are very believable (despite a few spelling mistakes)
- Some of the emails received a DKIM pass because they were sent from abused servers nominally controlled by a non-profit professional membership group
- Some of the emails were able to pass standard email authentication (SPF, DKIM, and DMARC) because the attackers sent them from newly created domains imitating the DOL (e.g., usdol-gov.com, usdol-gov.us, dol.global, and others)
“Since they are brand new, the domains represent zero-day vulnerabilities; they have never been seen before and typically do not appear in threat intelligence feeds commonly referenced by legacy anti-phishing tools,” the researchers explained.
Another clever trick was making the phishing page display a fake “Incorrect Credentials” error when visitors entered their credentials and redirecting them to the real DOL site if they repeated the process.
“This nuanced touch, borrowed from con artistry that well-predates the digital era, is designed to confuse the victim and delay the moment when they realize that they were taken,” the researchers explained.
They urged employees to remember that official U.S. government domains usually end in .gov or .mil rather than .com or another suffix, and that the U.S. government does not typically send out cold emails to solicit bids for projects.
“Potential victims should be aware that it makes no sense to be asked to log in with email credentials to view a document on a completely different network,” they added.