Cyber defense: Prioritized by real-world threat data
The impact of a cybersecurity breach can be painful for any enterprise, and devastating for some. Any one of the top five threats we see in today’s environment—malware, ransomware, web application hacking, insider and privilege misuse, and targeted intrusions— are serious and can cause severe, long-lasting financial and reputational damage. First, there’s the financial cost—$4.24 million on average, according to IBM’s 2021 Cost of a Data Breach Report. Then there’s reputational cost, which is much more difficult to quantify and can take years to overcome.
So, what can an enterprise do to defend itself against these most prevalent cyber-attacks? Whether driven by a need to meet compliance requirements based on industry frameworks or as an effort to improve its cyber defense program, the journey can be daunting—especially when there is a lack of clear, actionable guidance.
Read on to learn how proven and effective guidance from the Center for Internet Security (CIS) can help organizations defend up to 92% of attacker techniques.
Prioritized guidance for achieving essential cyber hygiene
When working toward compliance with security frameworks, many IT security teams reference the CIS Critical Security Controls (CIS Controls) to help guide their strategy. The CIS Controls are a set of 18 prioritized actions and 153 defensive measures known as Safeguards. They’re developed and refined by a global community of volunteer experts under the leadership of CIS.
Enterprises that adopt the Controls have repeatedly asked us to identify, “What should we do first?” In response, the Controls community categorized the Safeguards in the CIS Controls into three Implementation Groups (IGs) based on their difficulty and cost to implement.
Implementation Group 1 (IG1) helps enterprises achieve what we call essential cyber hygiene, and are the Safeguards we recommend every enterprise should deploy at a minimum. For those that face more sophisticated attacks, or must protect more critical data or systems, these Safeguards also provide the foundation for the other two Implementation Groups, IG2 and IG3.
Proven defense using the MITRE ATT&CK framework
Naturally, many enterprises want to know how effective the CIS Controls are against the most prevalent types of attacks. The CIS Community Defense Model (CDM) v2.0 was created to help answer that and other questions about the value of the Controls based on threat data from leading industry reports.
At CIS, we understand that not all enterprises will be able to perform this type of analysis on their own, which is why we created the Community Defense Model in the first place. The improved CDM v2.0 can be used by any enterprise to design, prioritize, implement, and improve its security program. And, it builds on the experience of the same security experts who help create the CIS Controls.
The CDM uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework, which enables us to express any attack type as a set of attack techniques, or attack patterns. For each of the five most prevalent attack types, such as ransomware, we collect the corresponding attack patterns, then track which CIS Safeguards defend against each technique found in those patterns. This methodology helps us measure which Safeguards are most effective overall for defending across attack types.

The findings from CDM v2.0 both reaffirmed and strengthened, with objective data, what we already thought to be true—that CIS Controls IG1 provides a viable cyber defense against the top five attacks.
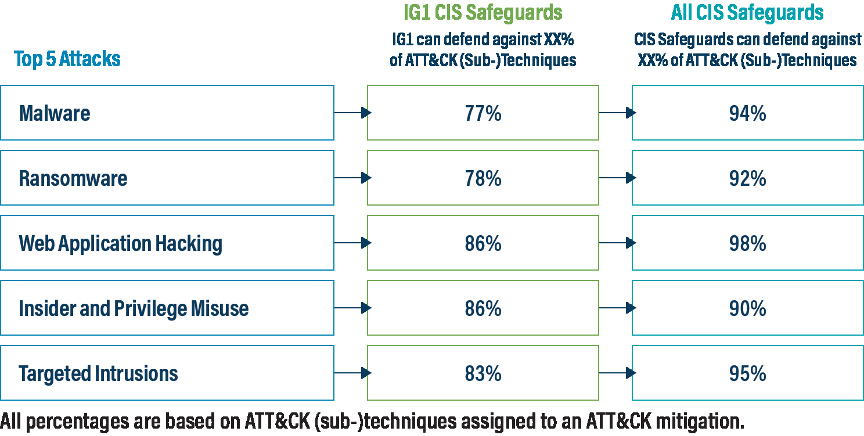
For CDM v2.0, the top five attack types are malware, ransomware, web application hacking, insider and privilege misuse, and targeted intrusions. Our analysis found that implementing IG1 Safeguards defends against 77% of ATT&CK (sub-)techniques used across the top five attack types. That rate of effectiveness improves to 91% if all CIS Safeguards are implemented.
These results show how a relatively small number of well-chosen and basic defensive steps (IG1) can significantly improve an enterprise’s cybersecurity posture, while also demonstrating how IG1 is the ideal on-ramp to implementing the CIS Controls. We also found that CIS Safeguard 4.1, “Establish and Maintain a Secure Configuration Process,” is most effective in defending against the top five attacks, reinforcing the importance of secure configurations, such as those contained within the CIS Benchmarks.
We also examined each attack type individually. Our analysis determined that implementing IG1 Safeguards defends against 78% of Ransomware ATT&CK (sub-)techniques, while implementing all CIS Safeguards defends against 91% of those techniques. This, and other attack pattern findings, can be seen in the image below. It’s worth noting that 100% protection against all attacker techniques for any attack type is difficult, as some techniques cannot be defended against.
Additionally, some IG1 Safeguards are foundational and process-oriented, such as enterprise and software asset management. While these foundational Safeguards may not be included in the ATT&CK model as defensive measures, they are necessary in order to successfully implement other Safeguards that map to ATT&CK.
Study after study has demonstrated that virtually all cyber-attacks succeed by taking advantage of conditions that could reasonably be described as poor cyber hygiene. CIS offers a wide range of tools and resources to turn the tables on today’s bad actors.
Want to get started? Get your copy of the CIS Community Defense Model 2.0 today.