Hunters SOC Platform enhancements enable users to prioritize incidents based on their urgency
Hunters announced new capabilities in the Hunters SOC Platform to enhance and accelerate security operations workflows for data ingestion and normalization, threat detection, investigation and response.
The advances free up data engineers, security engineers and analysts in Security Operations Centers (SOC) to focus on higher value work, such as dealing with threats and challenges unique to their organizations.
Security operations have long focused on response-based automation to orchestrate mitigation measures, using solutions like SOAR – efforts that only address the final phase of the security workflow – leaving significant opportunities for improvement earlier in the threat management process. SOC reliance on SIEM tools forces them to operate manual, labor-intensive tasks, such as data ingestion, cross-correlation of suspicious activities, detection rules maintenance, and more.
These challenges open an opportunity to streamline and automate common SOC tasks – including data engineering, detection management, cross correlation, incident investigation, and response, and to free up the security practitioners to focus on threats that are unique to their environment.
The newest version of the Hunters SOC Platform fills these gaps with powerful capabilities:
- Unlimited data ingestion, retention and schema mapping, removing data engineering efforts from the security teams
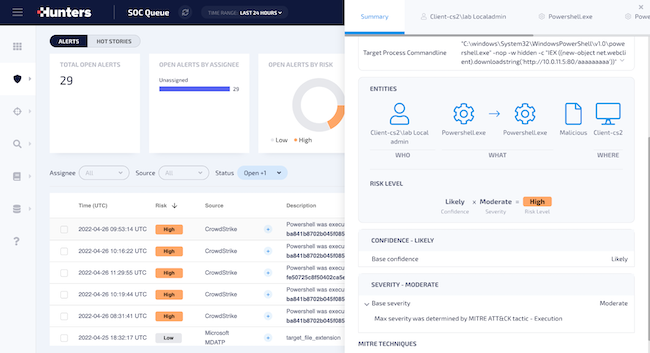
- Automatic calculation of risk level for each threat lead with Hunters Risk Score to determine a Confidence score and Severity score and rapidly identify the most pressing threats
- A Detection Engine to offload the never-ending task of building and maintaining detection queries, replacing it with MITRE ATT&CK-based automated threat detection across the entire attack surface (including cloud, email, endpoint, identity, etc.)
- Human-readable Attack Stories, where response and reporting are streamlined as analysts receive a complete contextual view of each real incident
“With our traditional SIEM, we would run canned searches to manually contextualize IP addresses, machines, and events, relying on manual efforts to tell the narrative of the incident. But Hunters is laid out in a chronological sequence that is human readable, and not simply epoch timestamps going from earliest to latest. Hunters’ investigation results are presented in a report designed for a human to consume, which was incredibly helpful for my team and our leadership team to immediately understand and make informed decisions with,” said John Fung, Director of Cybersecurity Operations at MorganFranklin and former deputy CISO at Cimpress, a Hunters’ customer.
Hunters Risk Score – Deep dive
Hunters’ new Risk Score runs multiple scoring models to calculate the risk level of each threat lead, examining multiple characteristics to determine a Confidence score and Severity score of the lead. Confidence and Severity scores are then combined to determine a Risk Score to prioritize the top incidents for analysts to focus on. Risk Score enables security analysts to:
- Assess the risk of a specific threat in the organization
- Clearly understand the necessary urgency of response based on the risk assessment
- Allow analysts to prioritize incidents based on their urgency
- Customize scoring to fit the risk profile of the organization
- Add business context to increase precision and reduce the noise
“The Hunters Risk Score is a culmination of integrated automation steps that reduce the noise that SOCs are struggling with and point the analysts to the efforts where they can best leverage their expertise to secure their environments,” said Ofer Gayer, VP Product at Hunters. “The security market has been conditioned to expect that more data means more people, time, and costs to address threats. Hunters shifts that paradigm by enabling cross-stream correlation, built-in detection, and auto-investigation to cull the noise and false positives, and to allow analysts to focus on the appropriate response measures.”
Security operations teams seeking to break away from the data dilemma that burdens engineers and analysts increasingly look to Hunters to modernize their SOCs with a platform that provides automation that enables their people to better focus on threat detection and response.