Researchers unearth highly evasive “parasitic” Linux malware
Security researchers at Intezer and BlackBerry have documented Symbiote, a wholly unique, multi-purpose piece of Linux malware that is nearly impossible to detect.
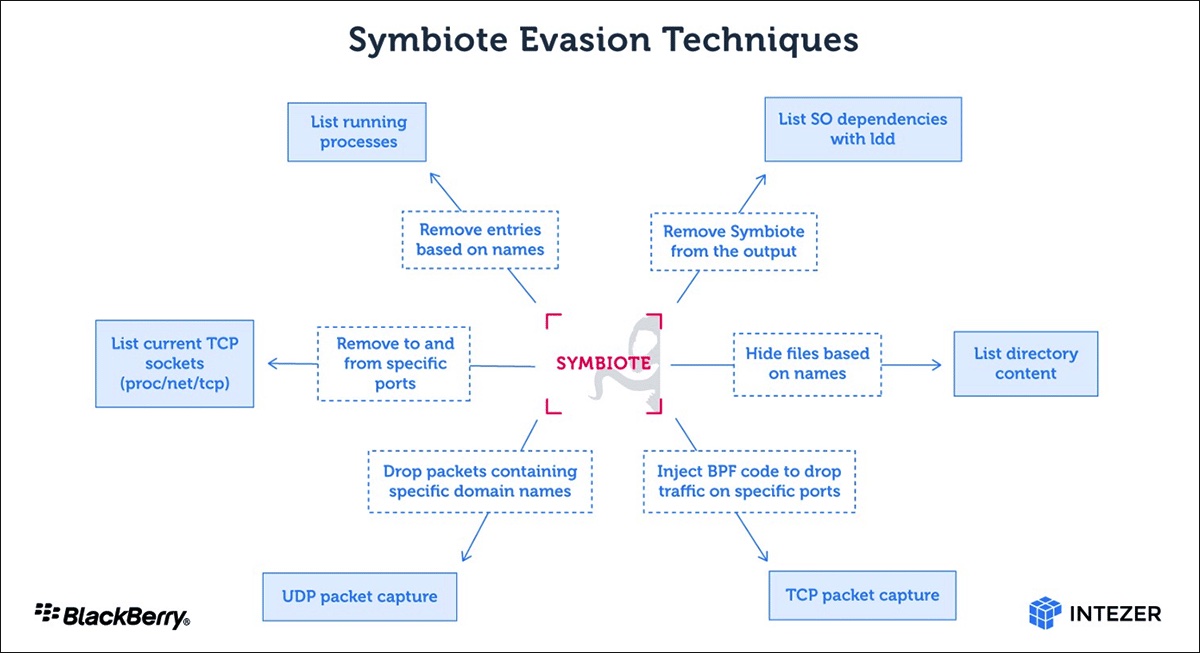
“What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object (SO) library that is loaded into all running processes using LD_PRELOAD (T1574.006), and parasitically infects the machine,” the researchers pointed out.
The many capabilities of the Symbiote Linux malware
Symbiote is an eminently capable piece of Linux malware: it operates as a rootkit, it can serve as a backdoor (allowing attackers to log in remotely with the help of a hardcoded password), it can execute commands with the highest privileges and can harvest credentials.
“The domain names used by the Symbiote malware are impersonating some major Brazilian banks. This suggests that these banks or their customers are the potential targets,” the researchers noted, but said that they weren’t able to determine whether the malware is being used in targeted or broad attacks.
But the one sample they got their hands on and the associated domain names led them to two more samples uploaded to VirusTotal, which used C&C servers parked at domains that apprently impersonated Caixa and Banco do Brasil, as well as Cintepol, an intelligence portal provided by the Federal Police of Brazil.
All the samples had been uploaded by the same submitter from Brazil. “Given that these files were submitted to VirusTotal prior to the infrastructure going online, and because some of the samples included rules to hide local IP addresses, it is possible that the samples were submitted to VirusTotal to test Antivirus detection before being used. Additionally, a version that appears to be under development was submitted at the end of November from Brazil, further suggesting VirusTotal was being used by the threat actor or group behind Symbiote for detection testing,” the researchers pointed out.
How the malware is delivered to targets is not known, but once it has infected a machine, it hides itself and any other malware used by the threat actor, by scrubbing evidence of files, processes, and network artifacts it uses.
Performing live forensics on an infected machine may not turn anything up any evidence of the presence of the malware, the researchers noted, and since it operates as a userland-level rootkit, detection is made even more difficult.
“Network telemetry can be used to detect anomalous DNS requests and security tools such as antivirus (AVs) and endpoint detection and response (EDRs) should be statically linked to ensure they are not ‘infected’ by userland rootkits,” they advised.