Phishers steal Office 365 users’ session cookies to bypass MFA, commit payment fraud
A massive phishing campaign has been targeting Office 365 (i.e., Microsoft 365) users in over 10,000 organizations since September 2021 and successfully bypassing multi-factor authentication (MFA) set up to protect the accounts.
The attackers use proxy servers and phishing websites to steal users’ password and session cookie. Their ultimate goal is to access finance-related emails and to hijack ongoing email threads to commit payment fraud and mount business email compromise (BEC) campaigns against other targets, Microsoft researchers explained.
Phishing Office 365 targets with MFA enabled on their accounts
The attackers start by sending phishing emails to multiple recipients in different organizations. The emails are usually fake notifications about missed phone call and urge the recipient to download the attached file to listen to the recorded voice message.
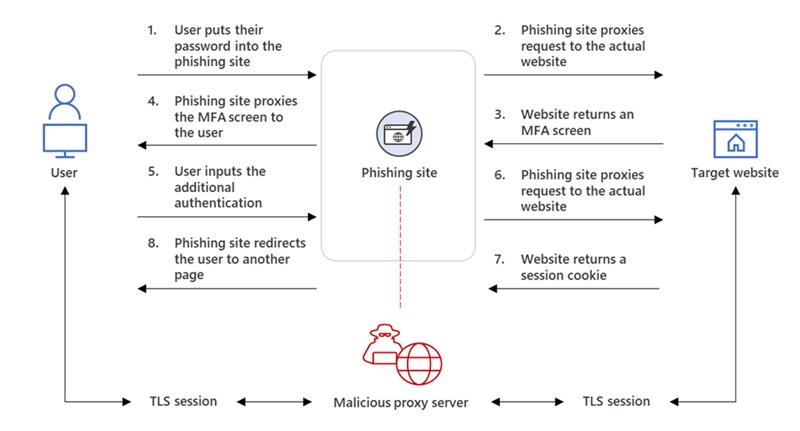
The ruse was just so that the target can be directed first to a redirector site and then to a spoofed Office online authentication page that’s been populated with the target’s email address.
“The phishing site proxied the organization’s Azure Active Directory (Azure AD) sign-in page, which is typically login.microsoftonline.com. If the organization had configured their Azure AD to include their branding, the phishing site’s landing page also contained the same branding elements,” Microsoft noted.
“Once the target entered their credentials and got authenticated, they were redirected to the legitimate office.com page. However, in the background, the attacker intercepted the said credentials and got authenticated on the user’s behalf. This allowed the attacker to perform follow-on activities—in this case, payment fraud—from within the organization.”
Once the attackers had long-standing access to the compromised email accounts, they searched for finance-related emails and email threads, responded to them and attempted to defraud the person/organization on the other side. To hide this activity from the owner of the email account, they used rules to hide replies (by archiving them and marking them as “read”).
Attackers are finding ways around MFA
Using any form of MFA is better than not using it at all, though some ways of delivering authentication factors are safer than others.
But there are ways to bypass MFA, and attackers are trying them all: rogue apps, vulnerabilities, legacy authentication protocols, spamming a target user with MFA prompts, and others.
According to the researchers, the attackers being this campaign are using the Evilginx2 phishing kit to stand up their adversary-in-the-middle (AiTM) infrastructure and achieve MFA-bypassing capability.
“MFA is still very effective at stopping a wide variety of threats; its effectiveness is why AiTM phishing emerged in the first place. Organizations can thus make their MFA implementation ‘phish-resistant’ by using solutions that support Fast ID Online (FIDO) v2.0 and certificate-based authentication,” they noted, and suggested additional solutions and best practices that can be implemented to stymie attackers using these particular tactics.